For day two of DEF CON, I checked out tamper evident devices, the contests area, and a few embedded talks. Read all about it after the break.
Tamper Evident Village
This year was the first run of the Tamper Evident Village. The village has a variety of tamper evident devices, including tapes, stickers, and seals. Volunteers provided tools, solvents, and instructions on how to bypass the various devices without setting them off.
The tamper evident challenge had teams trying to open a box secured with a variety of tamper-evident devices, then reassemble it. The judges evaluated the boxes on how well the security devices had been bypassed.

Contests
In the contests room, companies and volunteers ran all sorts of contests for people with various skills. The scavenger hunt list ranged from getting a mohawk to obtaining an aircraft exit slide. Gamers teamed up with hackers in Hack Fortress, a game where Team Fortress players get bonuses when the hackers on their team complete hacking challenges. Crash and Compile is a coding-drinking game, where competitors try to solve a programming problem and have to drink every time their code crashes.
Embedded Talks
[Todd Manning] and [Zach Lanier] presented their GoPro hacking in a talk called “GoPro or GTFO”. They managed to get a root shell on the camera and found that all of the services run as root. They also showed that the device could be used for surveillance proposes. They will be publishing source and information on their exploits on Github.
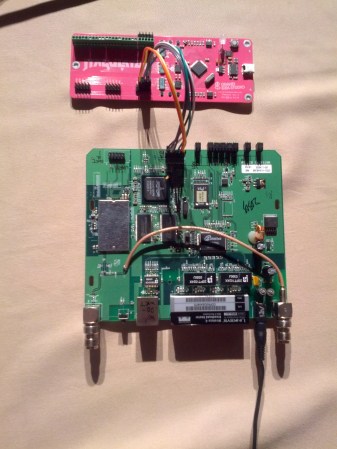
[Joe Grand] gave a talk on his new device: the JTAGulator. This open source hardware project helps with the automated discovery of debug interfaces. Target voltage selection and input protection is built in to prevent you from frying your target board. Right now, it can find JTAG and UART interfaces across 24 unknown channels. [Joe] demoed the device by discovering the UART and JTAG ports on a WRT54G wireless router.
DEF CON 21 wraps up tomorrow, and I’ll be sharing more cool stuff from the conference.

















really happy to see this, maybe i was wrong but i felt Schuyler’s talk on this subject (last year, i think) wasn’t as well received as it should have been.
i can say that the common zip tie used to hold wires together is not a good tamper evidence device since.
1. it can be replaced with a new one (unless it has a logo or name or serial number on it).
2. a pin can be placed under the ratchet tooth and lift it up and pull the end out and re attach it.
same goes with the ball chain style cable tie that uses 3 prongs as the ratchet tooth.
the sticker is better because it leaves a piece behind that shows tampering usually found on warranty or vhs rentals though it may be possible to peel and replace without initial evidence.
the lead and wire crimp on seal used by power co to seal the electrical boxes is probably the best since tampering cant be hidden.
there are plastic and wire versions now but the wire can be cut and pushed up into the plastic so it initially does not show tampering.
me personally i rather know that something has been tampered with than to stop it.
if you have any secrets like copyrighted code you could use a dremel and grind off the numbers on the rom chips so they cant be traced back and get rom dumping info.
“”if you have any secrets like copyrighted code you could use a dremel and grind off the numbers on the rom chips so they cant be traced back and get rom dumping info.””
Just x-ray and ID the die inside the package. Then you know the chip mgt and reduce the number of possibilities to download info and reprogram if needed. X-ray will not erase the original info if done properly.
“me personally i rather know that something has been tampered with than to stop it”
Is that the point of tamper evident devices?
They are designed to be easy to spot when something has being messed with rather than a way of keeping someone out…
They are a sort of lock of morality. Simple to bypass if you wanted to, but with the physical presence of a tamper evident device, in my experience people are less likely make an attempt in the first place.
The better option is to put the sensitive stuff inside a MCU and blow the security bits so it cant be read out. Then again, if its sensitive enough that
Then again, if its sensitive enough that someone really wants to read it, someone will find a way to read it out even if it means decapping the chip.
Still no word on a cure for tamper-resistant “security screws” on consumer devices that I own outright ….. :-D
How about buying a set of security bits? Again, these arnt designed to detect tampering, only to make it harder to tamper with in the first place so people dont bother
i think you mean “so normal people don’t bother” ;)
You can use a drill press to drill out the entire screw, then replace it with a normal one of the same threading.
The worst (as in, difficult-to-defeat) security fasteners I’ve ever seen were in a hotel room, suicide-proofing the window: It was a regular Phillips, with a pin sticking out of the middle. I wasn’t able to get these out with common hand tools. (We just wanted the window open a bit wider because it was hot, and we were drinking, and there were lots of us.)
The easiest are, by far, are stainless “security” Torx. Stainless is usually malleable enough that you can just hammer a regular Torx driver in there with the palm of your hand. This squishes the pin down and/or folds it over, leaving plenty of room to engage the fastener (which doesn’t take much: that’s one thing that Torx interfaces inherently excel at…which makes them somewhat self-defeating in this role).
Of course, there’s always the cold chisel, or the needlenose pliers with a built-in force multiplier, or the pocket screwdriver which has been ground down just-so…
They are just Legal Underwear! CYA.
another tamper device comes in the form of the tabs on cardboard boxes.
i just bought a http://www.scotbycycles.co.uk/accessories-c4/computers-c49/bontrager-trip-1-6-function-cycle-computer-p1228
from my local bike shop today and the box had a tab that looks like a mushroom and the side tabs are folded over and when the tab is placed into the slot the tabs open up and hold the main tab into place.
removing involves tearing the tab and bingo there is your tamper evidence.
as of xraying the chip yes that can be done but the average person does not have access to xray.
If you are describing what I think you are, some flat item will defeat the “tamper evident” part of the box.
(Working in datarecovery: a client wanted his data on an external drive. So we bought an external drive, opened it up, put his data on and closed it back down. Next day he calls: Where’s my data? He couldn’t believe we had put his data on the drive in the unopened box-with-tamper-evident-stickers). :-)