During these last weeks we’ve been talking a lot about the ESP8266, a $4 microcontroller based Wifi module. As the SDK was recently released by Espressif a lot of cheap Internet of Things applications were made possible.
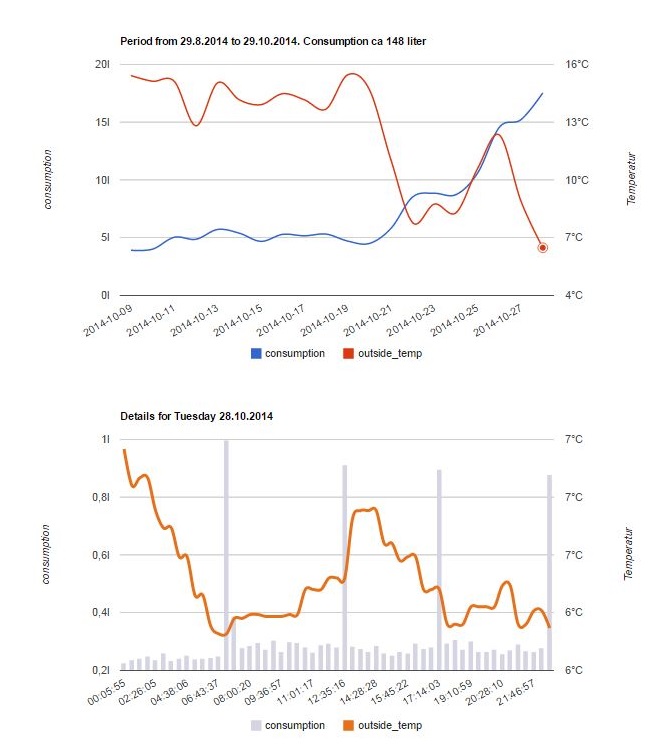
[Thomas] used one module to make a simple smartmeter measuring the active time of his heater together with the outside temperature. He added 2 AT commands starting/stopping the logging process and used one GPIO pin to monitor the heater’s oil pump state. The measurements are then periodically pushed via a TCP connection to his data collecting server, which allows him to generate nice graphs.
In the video embedded below you’ll see [Thomas] demoing his system. On his hackaday.io project page he put up a very detailed explanation on how to replicate his awesome project. All the resources he used and create can also be downloaded on the project’s GitHub page.















Good work!
So it begins! *grin*
So, it has come to this
I just recieved a few of these. Can’t wait to get started using them. First up, web controlled garage door.
I was thinking the same thing.
One thing you guys should think about: security.
Make sure that you have the sources for the firmware so nobody has implemented a backdoor. As nice as the ESP8266 is, I think we also should think a bit about security especially when talking about applications like you mentioned.
You seriously think that someone wanting to open a garage door would use a hidden backdoor in ESP8266 SDK?
no thats not what I meant :P
its not about the garage door as this is way too specific, but its about credentials and if you use the device to secure parts of your house its not a good thing that all you need is WiFi access.
I thought a bit about it and it is actually even worse.
Someone posts a IoT FW with some fancy stuff, maybe a small webserver running on it to toggle GPIOs or whatever. It sends the SSID, PW and MAC (plus maybe the “title” of the IoT, something like “garage door opener” to the attacker. The attacker is now having the WAN IP which he can use in a first approach to get the approximate location. After filtering interesting victims the attacker can use the google localization to get the exact Position of the victim. The rest you can think of your own… So as I said, be aware of Firmwares you find on the web. I dont say this is going to happen but there is the risk.
If you use bin file without read source and compile it you basically bringing a trojan horse inside your local network.
Could someone implement RFC2324 (HTCPCP) on one of these in an open source manner?
RFC 2324 is outdated, instead you should refer to the replacement: RFC 7168
personally I recommend RFC 1149 instead
I love parts like the ESP8266, they just come out of nowhere and revolutionize stuff.
Actually, it begs the question why more parts like this don’t exist. I guess it’s because the hobbyist-hacker market is so sadly small.
they do, they just cost ridiculous money, like CC3000 at >$20
all because corporations are GREEDY and will charge as much as they can get away with for $0.50 part
Pretty neat, but I’m a bit confused.
Is the USB-TTL connection to the server only for setup/programming?
If it’s permanently connected, then the Rx line on a USB-ttl adapter is all you need to poll an input (no esp8266 needed). Rx low = brk, Rx high = idle.
The USB-TTL is only for setup/programming.
If I would use the USB-TTL to measure the heater then I would need to have a PC in the basement next to the heater ;)
This is very possible and very little people are sharing source codes which mostly not working. Beware.For some even offering cloud update. A hacker could post bin file that before any response it configure and send your access point info. Nothing more stupid than this. Hah