The computer security industry has made many positive changes since the early days of computing. One thing that seems to be catching on with bigger tech companies is bug bounty programs. PayPal offers such a program and [Yasser] decided to throw his hat in the ring and see if he could find any juicy vulnerabilities. His curiosity paid off big time.
Paypal is a huge player in the payment processing world, but that doesn’t mean they aren’t without their flaws. Sometimes the bigger the target, the more difficult it is to find problems. [Yasser] wanted to experiment with a cross-site request forgery attack. This type of attack typically requires the attacker to trick the victim into clicking a malicious link. The link would then impersonate the victim and make requests on the victim’s behalf. This is only made possible if the victim is logged into the target website.
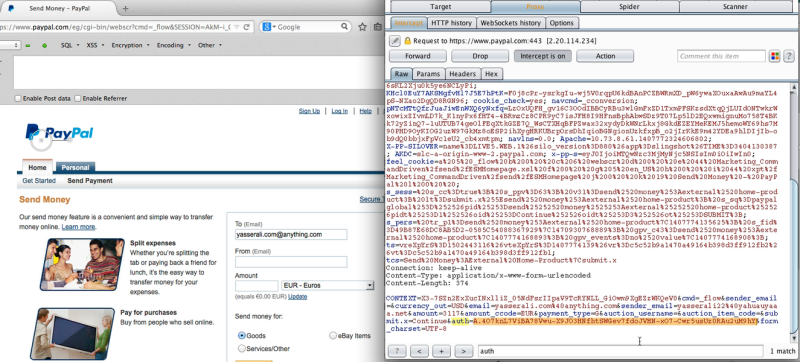
PayPal has protection mechanisms in place to prevent this kind of thing, but [Yasser] found a loophole. When a user logs in to make a request, PayPal gives them an authentication token. This token is supposed to be valid for one user and one request only. Through experimentation, [Yasser] discovered a way to obtain a sort of “skeleton key” auth token. The attacker can attempt to initiate a payment transfer without first logging in to any PayPal account. Once the transfer is attempted, PayPal will request the user to authenticate. This process produces an auth token that apparently works for multiple requests from any user. It renders the authentication token almost entirely ineffective.
Once the attacker has a “universal auth token”, he can trick the victim into visiting a malicious web page. If the user is logged into their PayPal account at the time, the attacker’s webpage can use the universal auth token to trick the victim’s computer into making many different PayPal requests. Examples include adding email addresses to the account, changing the answers to security questions, and more. All of this can be done simply by tricking the user into clicking on a single link. Pretty scary.
[Yasser] was responsible with his disclosure, of course. He reported the bug to PayPal and reports that it was fixed promptly. It’s always great to see big companies like PayPal promoting responsible disclosure and rewarding it rather than calling the lawyers. Be sure to catch a video demonstration of the hack below.
https://www.youtube.com/watch?v=KoFFayw58ZQ
[via Reddit]















Ahh… so thats why I just took delivery of 100,000 garden gnomes.. I was sure I hadn’t ordered any….time to check my paypal account ;¬0 … this shows some pretty smart thinking on the part of Yasser… and some rather dumb assumptions on the part of PayPal. good to see its been patched… worrying to think the vulnerability may have been around for a while.
It seems the attacker needed to intercept the traffic from the user being attacked to gather the information necessary to even start the attack, He uses burp side. As he says it was the only way to access the information because PayPal Uses SSL encryption. Hopefully he gets a good chuck of change for his findings from PayPal. ;)
My understanding is that he specifically needed to intercept traffic BEFORE a user is logged in. And that can be any user, including one that doesn’t exist. The reason is so he can obtain the “universal auth token”. This token is only presented when a user tries to send money before logging in. He doesn’t actually have to intercept the victim’s traffic. Once he has generated and collected the auth token himself, he just needs the victim to click on a malicious link. His attack then uses the auth token to trick the victim’s browser into submitting requests on the victim’s behalf.
That is what I find alarming; I often may payment via PayPal in this manner.
He got paypal’s max bounty $10,000 USD. Good thing, you really don’t want people to feel they could easily get much better on black market.
they should have tacked on another 0 and made an example of this bounty (set a new max), in order to show that playing nice can be lucrative. how much do you think this exploit is/was worth on said black market?
Forget the CSRF, the broken auth tokens is unba!
The biggest mitigating factor is, as was stated, that your browser would have to have been logged into PayPal already.
I know many people leave windows open continuously for days — I feel vindicated for logging out of Chrome at least several times a day (habit probably comes from early IE or Mosaic days when performance would tank after a while).
this *still* happens with IE… your precautions remain justified.
And other browsers (FF and Chrome for instance). Just have a look at heap-unclassified just growing in memory in FF and tell me that’s normal expected behavior from a web browser. Fragmentation and problems where memory isn’t reclaimed are all over the place.
Is there a modern browser that doesn’t suck?
No
Here’s one. Register a crap load of e-mail addresses for PayPal accounts and if anyone wants to send money to that address, you get the money. The actual owner of the e-mail address can’t even claim the PayPal account because they do absolutely no verification the person registering the address to the account actually owns the e-mail address.
If the government thinks that you are using those accounts to launder drug money they can feel free to make your life miserable. And you can also explain to the IRS where all of this “free” money is coming from and would you please pay taxes on it. Yes indeed this is a great way to make new friends, you can have nice chats with the government people who will show up at your door.
There was actually another vulnerability which i have included in the report, this vulnerability enabled me to change the “Security Questions” of the victim which is mandatory to takeover his account, Although it was password-protected!
Gr8 i know some people are selling Paypal Transfer in CHeap Price on this forum check this out http://unixorder.com
I saw a comment about kloviaclinks(.)com on the web and I decided to give it a trial. Just few minutes ago, they granted my application and added $70,000 to my PayPal. I am super amazed that it works for me.