We tend to think of elaborate electronic conference badges as something limited to the hacker scene, but it looks like the badgelife movement is starting to hit the big time. Now even the “big boys” are getting into the act, and pretty soon you won’t be able to go to a stuffy professional conference without seeing a sea of RGB LEDs firing off. We’ll let the good readers of Hackaday determine if this means it’s officially post-cool or not.
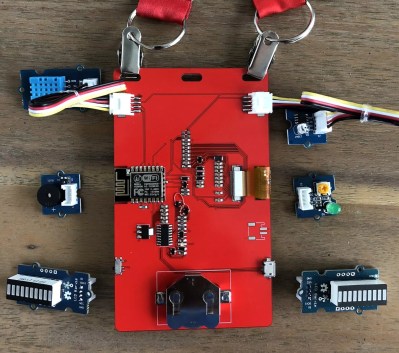 [Noel Portugal] writes in to tell us about how he created the “Code Card” during his tenure with the Oracle Groundbreakers Team. Featuring an ESP8266 and an e-ink screen, the Code Card serves not only as swanky way of identifying yourself, but as a real-world demonstration of physical devices pulling content from Oracle’s Cloud. Gotta keep those corporate overlords happy.
[Noel Portugal] writes in to tell us about how he created the “Code Card” during his tenure with the Oracle Groundbreakers Team. Featuring an ESP8266 and an e-ink screen, the Code Card serves not only as swanky way of identifying yourself, but as a real-world demonstration of physical devices pulling content from Oracle’s Cloud. Gotta keep those corporate overlords happy.
The Code Card is a fairly simple piece of hardware as far as badges go these days, but then the goal was never to be flashy. It does feature dual four-pin Grove System connectors on the backside though, so you can plug in additional sensors and gadgets for the customary badge hacking sessions.
To maximize runtime on the rechargeable coin cell battery, the Code Card only turns on the ESP after the user has pressed one of the buttons on the front. Once the ESP has finished performing whatever task the user requested, its powered back off completely rather than put into standby. Combined with the e-ink screen, power consumption while the device isn’t actively updating the display or pulling down new content is negligible.
[Noel] really went all-out on the software side, going as far as developing a web application which let conference attendees configure their Code Cards from their smartphones. Different functions could be assigned to short and long presses on the badge’s two buttons, and users could even select icons for the various functions from a list of images included in the firmware. A feature where attendees could upload their own images didn’t make the cut, but that surely won’t stop people from hacking around in the published Arduino source code and figuring out how to do it manually.
If you think the Code Card looks a bit familiar, it’s perhaps because it was designed in conjunction with Squarofumi, creators of the Badgy. So even if you aren’t hitting up any of Oracle’s upcoming conferences, you’re not completely out of luck if you want an e-ink badge to play with.