There’s a bunch of simple WiFi-enabled outlets on the market today, and all of these blister-pack goodies seem to have something in common – crappy software. At least from the hacker’s point of view; there always seems to be something that you want to do that the app just doesn’t support. Stuck in this position, [scootermcgoober] did the smart thing and reflashed his cheap IoT outlets.
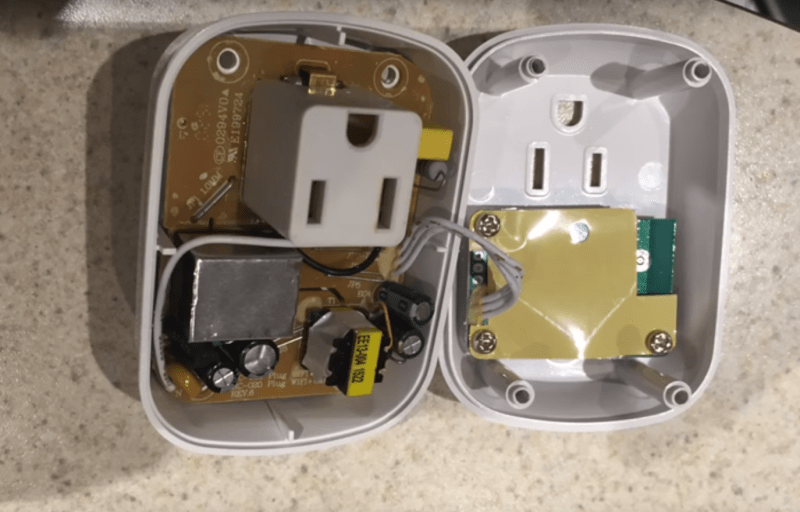
Although [scooter]’s video is very recent, and he says he got his plugs at Home Depot, we were unable to find them listed for sale at any store near us. Walmart lists the same device for a paltry $15, though, so the price is right for repeating his experiment. The video after the break shows his teardown, which locates all the major components, including a mystery module that was revealed to be an ESP8266 upon decapping. Pins were traced, leads were tacked to his serial-to-USB adapter, and soon new firmware was flashing. [scooter]’s new app is simple, but there’s plenty of room for improvement once you’ve got the keys. All the code is up on GitHub.
WiFi outlets like this and the WeMo have proved to be fertile ground for hacking. Of course, if you’re not into the whole blister-pack thing, you could always roll your own WiFi outlet.















I mean if i was tasked to do this that’s what i would use as well
Why are so many tear downs and product hacking projects all YouTube videos now. I only read HaD on mobile and don’t watch the YouTube videos.
Shame no one writes pages about things anymore >:[
You must have missed the first link in the post, which was to [scooter]’s blog.
He probably hit the read-more link only to reply and missed the rest of the article. HAD front page is clearly designed to hide any links contained in the articles, or better, the articles are designed without any links in the first paragraph so they are never displayed in the front page forcing the user to click deeper.
Would be really neat to find a source of the ones that are fully populated with energy logging abilities, does anyone know of a source for them?
They probably aren’t using that chip.
After making the video I did more digging; the depopulated parts provide the ability to measure the power factor voltage and current via the esp8266 using external DACs (also unpopulated). So the version with those parts populated should be able to be flashed as a data logger.
Work better as a logger with ADC not DAC.
Heh yeah I’m dumb. Working on finding an ADC compatible with the footprint/layout.
I purchased two from Walmart (http://www.walmart.com/ip/46721978) and they have the parts populated. Unfortunately the chip U2 has no markings on it… Have you seen anyone working on a current/voltage sense enabled firmware?
I popped the HV board out and took a look at the bottom. It appears current sensing is via a 2 ohm resistor/shunt. The voltage and current sensing is handled by a chip (U1 on HV board) labeled HLW8012. I found the following website which has a detailed explanation: http://www.tlola.com/en/Industry_Knowledge/2015/0828/64.html
I can’t read the datasheet (anyone want to translate)? I think it outputs a frequency relative to the quantity measured, and that there may be a pin (SEL) that sets what measurement is pulsed to the two output pins? I wonder if the unlabeled chip on the control board (U2) is an opto-isolator?
This page (https://sites.google.com/site/tgmaxx/energy-enviro-monitoring/smart-life-wifi-plug) also appears to have some good info.. It’s definitely not the same hardware, but the info on the HLW8012 chip is useful.
Typical tunnel vision geeks. More concerned about the ‘software’, then the fact the poorly engineered (translation: cheap azz) electrical outlet side of the picture will burn your friggin’ house down ! (plenty of pics out there of these cheap imports with melted, charred plastic sorrounding the outlet). Prudent folks would not be using one of these vandal engineered time bombs in their homes (maybe as a present for the ex-wife, hated coworker, or other person that did you wrong).
Please share links of this exact device melting and burning houses down. because from the photos it looks to be actually decently designed, and it has a UL certification on the box in Home Depot.
I’m thinking along the same lines as Sofinc. I’ve ordered 2 plugs and I’ll see what they’re like. Not sure how much trust I can put into them.I don’t see anything about a CE or UL listing so I’ll assume it’s not.
UL label?
My company once received a box of outlet strips (Made in China); the Hot and Neutral wires were reversed on all of them. UL label right on the back!
To be honest, I would rather trust these than the various hacker wall outlet projects that I have seen on HaD. Most of the duct taped together projects do not even understand basic isolation nor creepage clearance requirements. e.g. on an optoisolator, the empty space between the sides are for creepage requirement and not supposed to run traces between them.
Do not mail order from China directly. When a company like Homedepot or Walmart import from China, they are liable for these type of “accidents”. Depending on the local laws/regulations, the device have to have safety certification e.g. UL or local hydro before they can be sold. Using them won’t void your home insurance.
As OP mentions these seem pretty well made. They use normal screws, the relay is in a metal shield, and the RF module is also shielded and looks FCC certified. It seems unlikely that that’s faked since they re selling them in big-box stores in the US. I don’t like the Chumby-like reliance on an outside server but reflashing and doing your own code on it fixes that.
The Home Depot ones are made by KAB, they have a whole line of them http://www.kab-cable.com/product.php?CNo=26 they are also sold under the “Woods WION” line of smart switches.
Good hack
KAB web page lists all models with an “Advanced” option that has the power monitoring. They have the same part number though as the non-power-monitoring versions. At HomeDepot, only the indoor surge/power strip at $50 is listed to have the power management feature. At WalMart, search under WorkChoice WiFi… and state: “Compute the electricity consumption and electric bill”. If this is true, and not an oversight, $15 is a great price.
http://www.walmart.com/ip/Generic-CT-063W-WorkChoice-1-Ol-Wi-Fi-Indoor-Switch-White/46721977 does seem to be an energy enabled one for $15. Wonder if it actually works
I can can now confirm that this version does have the energy logging functionality, and uses a hlw8012 as described at http://www.tlola.com/en/Industry_Knowledge/2015/0828/64.html
I bought 2 modules for $7 2 months ago at home depot. They connect to some Chinese server in China.
Man that is scary; have the wire shark capures it would be interesting to investigate in detail.
More worry about your US and “allies” spy agencies than a server in China as their government do not do thing to you under pretense of national security and affect you *where you live*.
There are security reliability issues of relying on external server e.g.hackers can control your toys. A decent router (e.g. with open source firmware) can firewall the wifi devices.
@tekkieneet:Hmmm, in your other comments, you don’t seem so naive to believe Chinese access to your Lan is better than domestic spying.. That’s foolish;wise up!
I can get into hot water much faster with domestic spying for saying the wrong thing or being mistaken for the wrong person. Just taking a flight or walking into a government building would requires some security check point. Whereas for Chinese spying, they are PI * 10,000km away with a 12 hours time zone difference. I don’t have too many thing that are useful to them.
I do value my privacy and as such would not use anything “in the cloud” because I am lazy. I am one of the few without a cell phone, facebook or have selfies. Yes, I use a router with Tomato firmware.
The stock firmware sends your SSID and password in plaintext to that foreign server. Not much of a stretch to get from that to a botnet or a driveby user trading child porn. The CP charges will get you absolutely crucified, the botnet is just a nuisance to the rest of us. You really need to re-evaluate your threats. Also, get a cell phone and set up a public profile so you don’t stand out as one of “those tinfoil hat guys”. Play the heuristics!
this is really part of Russia’s plan for global dominance to setup a distributed network to broadcast NTSC TV signals to deliver the message for revolution. Unite proletariats! Long Live ESP8266!
We had a discussion about these outlets on the Parallax forums too:
http://forums.parallax.com/discussion/162862/wifi-controlled-outlets
Well, good thing I bought 5 before this got on hackaday. No, this won’t burn your house down, and no, your coffee pot’s control is not interesting to the Chinese government or the us spy agencies. I find it so strange that people come here to comment about how they would never use things like this because they’re paranoid about X, Y, and Z but there’s never anything bad that happened because of it. If you remotely turned on my gas stove, all my soldering irons and my steam iron my house wouldn’t burn down (although my energy bill would go up a bit, boo hoo). Of course they go through a chinese server, a chinese company built these and that’s how the cloud works. My skybell goes through a server I don’t control, as does my garage door opener, they just happen to not be chinese companies.
oh so short sighted…. the ability for someone else to power on your soldering iron isn’t of interest to them, but the fact that someone has a device on your network, connecting to them, provides them with direct access to your home network…
of course, if every device on your network is uber secure, then that’s not a problem… but that’s highly unlikely…
I’m pretty sure you’re doing security wrong if this device let’s someone break into your entire home network. That sounds a lot like security through obscurity, and unless that’s the hostname of your firewall you have other issues.
Thing is, if you reflash them as OP and I did, the security issue goes away anyway.
I saw this post and went right to home depot, could not find these at all, My walmart doesn’t have the other brand in store either. St Paul MN if you’re wondering
Seems to be an ‘online only’ in my area. The Home Depot and Walmart don’t have them in the stores in NJ.
The window at Home Depot was very short. When I found out about the deal I went online and only one of the four nearest stores had any, and I paid for them online to pick up at the store later. I suspect if I’d waited to go to the store and shop the next day they’d have been gone.
I think Home Depot probably stocked these things for christmas, as both gifts for the Dad who doesn’t like anything, and to turn on and off christmas lights. That’s why they were on clearance at the beginning of the year, and gone now.
I wonder if there is a possibility to make it work if IFTTT?
Since it’s pretty much an ESP8266 and we can replace the firmware it should be able to be accessible to IFTTT. My intention is to get it to talk to my local MQTT setup but going further is just a matter of programming.
Well I just picked mine up from Walmart and it has a UL label embedded in the plastic (okay, seems real) and the power circuits. Cool!
Same here. Just got mine today and has the Watt measurement stuff. Haven’t powered it up yet. Wish we could download the original firmware just in case.
You might be able to, the processor uses SPI flash which should be able to be sniffed it with a bus pirate
Thanks for reminding me I have a bus pirate. The app that comes with it isn’t too bad. I think the hard part is going to be figuring out how to keep the power usage measurements since the IC is not marked
For those that are interested in the power monitoring, I have posted some example code that reads at least the watts used on the original site in the comments. In general, for the units that have the power monitoring (Walmart had them), there is a chip that does analog to frequency reading of the current, voltage, and wattage. That goes to a unlabeled 8 pin microcontroller that counts the pulses and provides those counts via I2C as 16 bytes of data, those counters are cleared every time they are read. That seems to consist of 4, 4 byte long words – high byte first. The first value (first of the 4 bytes) appears to be watt count. With some simple measurements of loads I was able to make a simple formula to map readings taken at 10 second intervals to a watt value. I haven’t tried to map the other 3 values as I don’t have much need for that in my application.
I hope that helps anyone who is experimenting with the power measurements for their own projects.
Thank you so much! I can finally get around to this project. I didn’t want to start till I knew I could get the energy data.
Hey David, I know this comment was a while ago, but do you happen to have a code sample for reading the watts? I am having some issues with decoding the bytes, is it just a 4 byte little endian?
I’ve seen claims in several places that these devices phone home to China with cleartext SSID & password. Anyone able to demonstrate or substantiate that claim?
Yes, I have and you can also, just grab wireshark or tcpdump and sniff the network. I watched as the setup from my phone had the SSID & Password in clear text and the video stream packets also contain the same information I think of you search on the Funlex camera topic you’ll find some of the packet info posted (without the SSID & Password though)
Oops, sorry that was related to the Funlux camera specifically. Not sure about the ESP8266 sockets (but I wouldn’t doubt it).
Interesting stuff, few turning up at various auctions,
might grab a few and mess with them, thanks for posting