We’re less than a week away from the Hackaday Superconference, where we’ll be announcing the winners of the Hackaday Prize. The Hackaday Prize is a celebration of the greatest hardware the Hackaday community has to offer, and in the past three years we’ve been running this amazing contest, we’ve seen some awesome stuff.
While not every project entered into the Hackaday Prize has gotten off the ground — the lawnmower-powered killacopter of decapitation is still tethered to its test stand — there have been some spectacular projects over the past few years that have already had an incredible impact in industry, academia, and the security industry. For the next few days, we’re going to revisit these projects, see how they’re doing, and look at the impact they’ve had on the world of Open Source hardware.
The first project we’re taking a look at is the ChipWhisperer a tool created by Colin O’Flynn to look at the secret insides of chips and firmware despite whatever embedded security is enabled on said chip. The ChipWhisperer was an entry into the first Hackaday Prize where it won second place. Since then, the ChipWhisperer has become the de facto hardware tool for investigating clock glitching, side channel analysis, and other exotic magic tricks that make security analysis so much fun.
What is the ChipWhisperer?
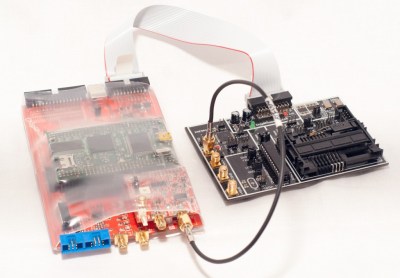 There is a problem with every crypto system on the planet. Crypto must run on real hardware, and with this comes the ability to analyze the bus, side channel attacks, and clock glitching. If you glitch a clock when a microcontroller is processing an instruction, something might go wrong. If you’re very good, you might be able to glean a little bit of information about what was happening inside the microcontroller at the time.
There is a problem with every crypto system on the planet. Crypto must run on real hardware, and with this comes the ability to analyze the bus, side channel attacks, and clock glitching. If you glitch a clock when a microcontroller is processing an instruction, something might go wrong. If you’re very good, you might be able to glean a little bit of information about what was happening inside the microcontroller at the time.
Clock glitching, side channel analysis and all the other tricks up the ChipWhisperer’s sleeve have been around for decades. The equipment to perform these attacks and analyses have been extremely expensive. The ChipWhisperer is the first low-cost, open source toolchain to enable these attacks. The low price and open source nature of the ChipWhisperer opens the door to research, in-the-trenches engineering, and even a few hardware hackers tinkering around on their workbench.
A Worked Example
If a device that does clock glitching and power analysis is a bit too esoteric, there are a number of publications and hacks surrounding the ChipWhisperer to use as a real, concrete example. A few months ago [scanlime] decided she wanted the firmware from a cheap Wacom tablet. This tablet included a processor with broken out debug pins, but everything was inaccessible; the firmware isn’t available online, and trying to pull the firmware off the microcontroller is an exercise in futility.
The solution to this problem of missing firmware came in the form of the ChipWhisperer. By desoldering the crystal on this Wacom tablet and sending power supply glitches when the device was starting off, the microcontroller would keep sending out bits of firmware. With a little bit of disassembling and reverse engineering, [scanlime] was able to completely reconstruct the firmware for the device:
Of course, dumping firmware from cheap Wacom tablets isn’t the only use for the ChipWhisperer. In two years, the ChipWhisperer has gotten a lot of traction in academia, with papers ranging from ECC cryptography on 8-bit Atmel microcontrollers to clock glitching secure platforms.
After the Prize
Second place in the first Hackaday Prize was only the start for the ChipWhisperer. Since that, Colin Kickstarted the ChipWhisperer Lite, and dedicated a lot of resources to a proper software stack for his hardware. An entire community has grown up around the ChipWhisperer, with a lot of work dedicated to refactoring the ChipWhisperer software, putting everything into a sane architecture, and making the software side of an Open Source project sane.
The ChipWhisperer is one of the most powerful tools we’ve seen in the Hackaday Prize. Sure, the equipment to perform these power glitches and side channel analysis have existed before, but the ChipWhisperer is a force multiplier. Previously, the equipment to perform these attacks cost as much as a car. The ChipWhisperer Lite is only about $300. That’s cheap enough for any grant an academic could apply for.
Of course, like all good projects, the ChipWhisperer isn’t done. Colin is working on the ChipWhisperer Pro, a version of the hardware with a larger FPGA for more robust experimentations. The Pro version isn’t out quite yet, but with the community Colin has built, it’s sure to be a very capable tool, and remains one of the best projects we’ve ever seen in the Hackaday Prize.



















“There is a problem with every crypto system on the planet.” – not exactly. The problem is with giving someone hardware containing secret keys (or data/firmware/whatever) and still keeping them secret.
Actually, the problem is not understanding these types of attacks and not designing your hardware to handle them.
I have identified the common flaw with every crypto system, it’s that frigging Bob and Carol, fortunately I have identified them both and have pictures of their kids getting out of school…. for future reasons….
Don’t forget Alice!
If this wins then I think [scanlime] should at least get a nod for her excellent videos on how to use the thing. I wouldn’t have appreciated it’s use without being educated.
RTFA?
Bet you $500 it doesn’t win this year.
No bet :-)
That was such a good video.
I learned a lot.