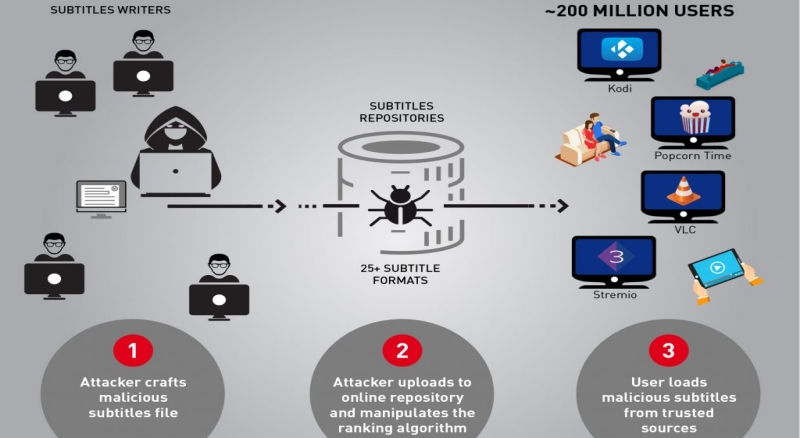
CheckPoint researchers published in the company blog a warning about a vulnerability affecting several video players. They found that VLC, Kodi (XBMC), Popcorn-Time and strem.io are all vulnerable to attack via malicious subtitle files. By carefully crafting a subtitles file they claim to have managed to take complete control over any type of device using the affected players when they try to load a video and the respective subtitles.
According to the researchers, things look pretty grim:
We estimate there are approximately 200 million video players and streamers that currently run the vulnerable software, making this one of the most widespread, easily accessed and zero-resistance vulnerability reported in recent years. (…) Each of the media players found to be vulnerable to date has millions of users, and we believe other media players could be vulnerable to similar attacks as well.
One of the reasons you might want to make sure your software is up to date is that some media players download subtitles automatically from several shared online repositories. An attacker, as the researchers proved, could manipulate the website’s ranking algorithm and not only would entice more unsuspecting users to manually download his subtitles, but would also guarantee that his crafted malicious subtitles would be those automatically downloaded by the media players.
No additional details were disclosed yet about how each video player is affected, although the researchers did share the details to each of the software developers so they can tackle the issue. They reported that some of the problems are already fixed in their current versions, while others are still being investigated. It might be a good idea to watch carefully and update your system before the details come out.
Meanwhile, we can look at the trailer:















It’d be better if you didn’t rush to get page views and waited for actual details of the exploit. Without it, there can be no meaningful discussion.
I agree that there can be no meaningful discussion without further details. There are probable different exploits since they talk about different file formats and different players, but we can only speculate (not very meaningful). As for the rushing, I think would rather help to warn our readers now so they can upgrade and revisit the subject if the exploits are interesting than the other way around.
I think it’s just one exploit but code sharing makes it affect multiple players.
I know for a fact that strem.io is based on VLC code (illegally, since they aren’t open source) and I’m guessing the other applications listed use VLC code as well – but legally, since they’re all GPL projects.
It seems to me, that it would be important to reveal the code behind the exploit, so as to allow the readers to demonstrate it on their own time and to devise their own paches for the exploit.
Better how and for whom?
So, disable auto-subtitle retrieval and fix the plug-ins right?
So it’s a handful of Subtitle Renderer plugins that have the weakness with those fancy HTML tag features well durr, https://news.ycombinator.com/item?id=14408859
VLC and Kodi already have updates for this. Some others as well.
Who ever thought it was a good idea for a subtitle program to do anything other than display text on a video in the first place?
+1 Im scratching my head on this one….must have been some marketing gurus idea…
The problem, as it says in the linked article, lies in the lack of standardization of format for the subtitles. At a guess, up until now the players just asked the repository what MIME type the subtitle file was and ran with whatever the answer was, while the new patches add some code to reject any types the are executable.
An they don’t.
In the case of Kodi is a directory traversal exploit in the zip manager. This means that a malicious zipped subtitle could potentially overwrite any system file!
For VLC are several Heap out-of-bound and buffer overflow memory exploits (CVE-2017-8310, CVE-2017-8311, CVE-2017-8312 and CVE-2017-8313)
Anyway, while the latest downloadable VLC is already patched, for Kodi only sources for Krypton and Jarvis are.
Kodi downloadable binaries like OpenELEC neither are even for the latest 8.0.3 Krypton. And many people running it in a Raspberry can’t upgrade and are stuck with 7.0.1. (dropped LIRC supoort, missing TVHeadend, samba shares access problems, …) So they may be forced to switch to LibreELEC to fix the issue.
Popcorn time was incredible for about a week and then it totally screwed up my whole win7 environment. I can’t help thinking it was via the subtitles. It was, in reality, completely untrustworthy software anyway. There never was a worse nightmare for the film industry than popcorn time. It was free Netflix but with ‘every’ film ever.
Further proof that dubs > subs.
Dubbing kills movies. Lips move out of place and it is like watching a movie with sound out if sync.