[q3k] got tipped off to a very cool problem in the ongoing Pwn2Win capture-the-flag, and he blew it out of the water by decoding the metal interconnect layers that encode a password in a VLSI IC. And not one to rent someone else’s netlist extraction code, he did it by writing his own.
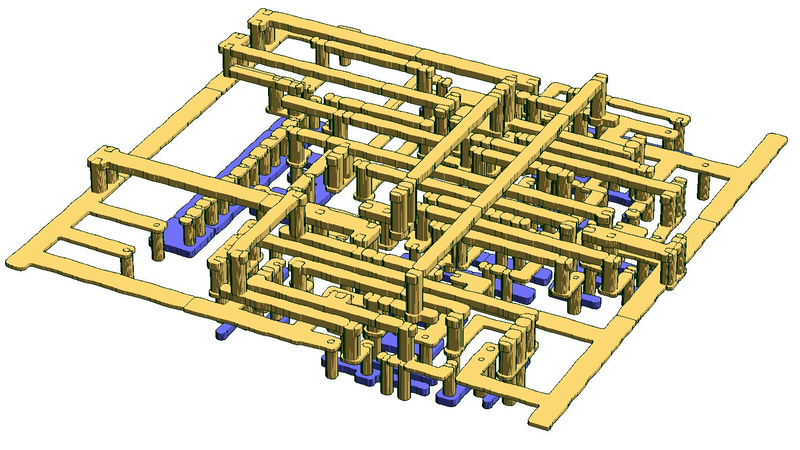
The problem in the Pwn2Win CTF came in the form of the design files for a hypothetical rocket launch code. The custom IC takes an ASCII string as input, and flips a pin high if it matches. Probably the simplest way to do this in logic is to implement a shift register that’s long enough for the code string’s bits, and then hard-wire some combinatorial logic that only reads true when all of the individual bits are correct.
(No, you don’t want to implement a password-checker this way — it means that you could simply brute-force the password far too easily — but such implementations have been seen in the wild.)
Anyway, back to our story. After reversing the netlist, [q3k] located 320 flip-flops in a chain, suggesting a 40-byte ASCII code string. Working backward in the circuit from the “unlocked” pin to the flip-flops, he found a network of NOR and NAND gates, which were converted into a logic notation and then tossed into Z3 to solve. Some cycles later, he had pulled the password straight out of the silicon!
This looks like a really fun challenge if you’re into logic design or hardware reverse engineering. You don’t have to write your own tools to do this, of course, but [q3k] would say that it was worth it.
Thanks [Victor] for the great tip!
Featured image by David Carron, via Wikipedia.















Hardcoded password? That’s the kind of thing an idiot would have on his luggage.
almost as dumb as the post-it under your keyboard. (if you freaked out a little right now, you may want to re-think your security choices.)
If someone is at you keyboard, they kind of have physical access anyway. But with a post-it, you just made their jobs much easier.
Unless the password is deliberately wrong…
… and starts ordering his kids the sugar free gummy bears from amazon…. no that’s probably too far.
Those are some good ideas……
It’s a CTF stage. You wouldn’t complain about the clues in a crossword puzzle, would you?
Yes, you buy one of those crossword books and there’s only about 300 unique clues total, by the time you’ve done the first 10 puzzles, the only thing stopping you filling them in faster is writers cramp.
Can any care to explain how this functions?, even though such implementations might be archaic, but still quite important to understand core concepts of Electronics.
Im propably cutting corners here (not even read the source). But a shift register gets the key presses in sequence, puts em on a bus(databus) and apparently some nor and nand gates result into either no(low) or succesfull (high) trigger pin. Ttl login, 40xx or 74xxNN primers might give you an idea.put those yellybean parts in silicon and you got yourself a custom chip. Why use an arduino when a 555 timer and some 74ls?? Coild do it? Or even more crazy, just some transistors?
If I understand things correctly, he solved a puzzle in an online fantasy game.
> Probably the simplest way to do this in logic is to implement a shift register that’s long enough for the code string’s bits, and then hard-wire some combinatorial logic that only reads true when all of the individual bits are correct.
That isn’t the simplest route. Have a 9b counter which counts through the sequence, and as each digit is entered, sets a buried flop to “mismatch” if bit N is wrong. Once the counter gets 320 bits, if the mismatch bit is not set, then output “match”. 10 flops total, instead of 320.
The shift register is the easiest solution if your chip accepts a continuous string of bits and wants to output a signal if there is a matching substring anywhere in that sequence.
To me “pulling passwords out of silicon” would mean someone decapped a chip and started looking at the layout….
Same. From the thumbnail, that’s what I thought someone did.
I like the other post better about the guy who pulled a password a magneticly held password with a crt, when he plugged a hard drive into an old Pc and did a sector read and read the password off his screen