Bluetooth Low Energy (BLE) is everywhere these days. If you fire up a scanner on your phone and walk around the neighborhood, we’d be willing to bet you’d pick up dozens if not hundreds of devices. By extension, from fitness bands to light bulbs, it’s equally likely that you’re going to want to talk to some of these BLE gadgets at some point. But how?
Well, watching this three part video series from [Stuart Patterson] would be a good start. He covers how to get a cheap nRF52480 BLE dongle configured for sniffing, pulling the packets out of the air with Wireshark, and perhaps most crucially, how to duplicate the commands coming from a device’s companion application on the ESP32.
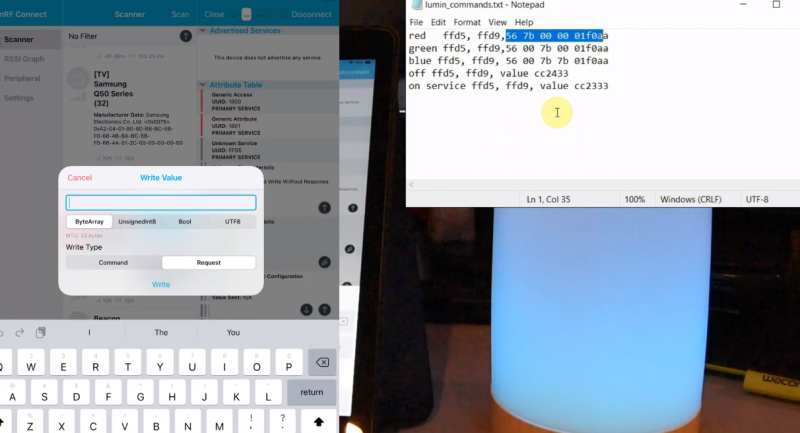
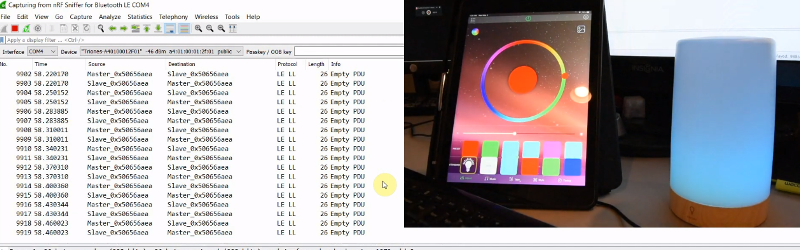
The first video in the series is focused on getting a Windows box setup for BLE sniffing, so readers who aren’t currently living under Microsoft’s boot heel may want to skip ahead to the second installment. That’s where things really start heating up, as [Stuart] demonstrates how you can intercept commands being sent to the target device.
It’s worth noting that little attempt is made to actually decode what the commands mean. In this particular application, it’s enough to simply replay the commands using the ESP32’s BLE hardware, which is explained in the third video. Obviously this technique might not work on more advanced devices, but it should still give you a solid base to work from.
In the end, [Stuart] takes an LED lamp that could only be controlled with a smartphone application and turns it into something he can talk to on his own terms. Once the ESP32 can send commands to the lamp, it only takes a bit more code to spin up a web interface or REST API so you can control the device from your computer or other gadget on the network. While naturally the finer points will differ, this same overall workflow should allow you to get control of whatever BLE gizmo you’ve got your eye on.















thanks! I put it on my watch list
Fantastic tutorial. I’ve been down this road before a couple of years ago reverse engineering a product for a client (previous R&D engineer left no documentation).
Creating an A/D-to-BLE that would have the lamp react to music would be cool.
Also, there are BLE compatible Star Wars ‘droids that are controllable w/ BLE. They are mobile and have sound/visual reactions based on BLE commands sent to them. I reversed engineered one of them back in early 2020 (bought it at the Disney World Galaxy’s Edge exhibition) and had it singing and “dancing” using BLE techniques similar to what you present here in your fantastic set of tutorials.
*This* is how you do a tutorial.
Hmmm, just this week I downloaded Wireshark (on da Linux) and played around with it, but not for any particular reason.
Was cool to see the exchanges between a client and wifi router.
Yeah, I have good memories on learning Wireshark. Thanks for bringing those back.
Definitely going to watch this. I bought a BT LE sniffer thing from Adafruit a while ago trying to sniff signals between a BB8 and my phone. Their learning guide walked through sniffing an RGB LED lamp’s commands but I never really got anywhere with my BB8. Maybe this series will help. Thanks!
Shameless plug here.
I built a web page server for RasPi that allows the user to interactively explore the BLE landscape using a browser. The interface is ‘sorta like the file manager, in that it lists all the BLE devices, and you can open them like directories to see the services, open the services to see characteristics, and so on.
If the characteristic is known or in a known format (vendor ID, serial number, &c), it will format and show the values as well.
Useful as a first step in BLE reverse engineering, to find the device address and list of services/characteristics to explore.
Unfortunately, my javascript/web-fu is weak, and I stopped after the reading/showing characteristics step. Link below for anyone who wants to use it. I have a design in mind for managing the r/w attributes and tabulating/showing old values so you can write characteristics and see what changed, but it’s starting to hard press my HTML/javascript ability to show it.
(Would anyone conversant in javascript and html like to join me in this endeavor? I can readily code or fix the BLE interface as needed, but formatting the HTML results in javascript is difficult at my level of experience. With a collaborator, we could knock out a full project in a week or two and release it open source for others to use. Ask to join the project, or contact me on .IO (link in title) to discuss.)
https://github.com/ToolChainGang/BLEServer
For anyone interested in this protocol be aware different mobile phones work differently. Something went wrong with this standard (too complex?) and there is not agreement on how this is supposed to work. I tried this my self and about 50% phones fail to connect to my raspi. Also a friend of mine has a ethanol unit in his car which connects via bluetooth LE. It works only on some phones.
This is so exciting! What a great post! I want to use BLE for indoor/outdoor positioning and this looks very applicable. It’s too bad that the startups/companies that were selling small BLE stickers seem to have dried up. I found out recently that Apple is planning to release Appletags which I think are going to use UHB, and BLE. It would be nice to be able to weave several systems together like wifi and ble to get super accurate positioning. Maybe some of this stuff is the beginning of this.
you can get the nrf52840 dongle cheaper, there is $7-$9 E104-BT5040U device on aliexpress (e.g here
https://www.aliexpress.com/item/1005001529756677.html ) which is fully compatible with original nordic dongle so you can flash it with nrf ble sniffer firmware with nordic tools in few seconds over usb
It would be interesting to sniff some BLE “smart home” devices like the newer Philips Hue bulbs and decode the commands.
Example bulb link here: https://www.philips-hue.com/en-us/p/hue-white-and-color-ambiance-2-pack-br30-e26/046677548582#specifications
The following article says the bulbs use BLE not older bluetooth.
https://www.androidpolice.com/2019/06/27/philips-introduces-new-bluetooth-hue-bulbs-that-work-without-a-hub/#:~:text=Unlike%20traditional%20Hue%20Bulbs%20that,phones%20but%20also%20smart%20speakers.
Awesome timing! I just got some app-controllable lights which I think use BLE. I guess this is another project for the pile now!
You can probably skip the sniffer if the app is on an android phone: you can probably enable developer mode on the phone, enable HCI snoop log, use the app, pull the logs with `adb bugreport`, extract the packet dump from the log in that with `btsnooz.py`, and open that with wireshark
Though those dongles are very cool, and are an extremely powerful BT dev platform
Also if the gadget uses a standard BLE protocol like GATT, you can probably just figure it out with an app like nrf connect or lightblue
I think getting the phone to follow a connection (like Nordic BLE Sniffer does), by listening to the connection establishment and basically stepping in sync with the peripheral, might be hard.
Great post. Thanks for sharing it. Are these techniques working with old blu3etooth devices too ?
Just now starting this project to hack the commands for a wireless TENS unit (transcutaneous electrical nerve stimulation). I’m at the end of video 2 stage trying to get the various Characteristics. In my case, there is, naturally, only one Service UUID but there are separate Characteristic UUIDs. I will be using the nRF connect shortly to test some of the commands. After that I will try a simple program in C++ Visual Studio using the Windows BlueTooth API. I would have never even gotten this far without your videos….thanks a million
Great tutorial !!!!!
How about reading servcice and characteristics ? Would it be the same ? What if they are encrypted ? I am trying to read values from a water analyzer BLE device .
Hoping this technique will yield some results in pulling raw data from Oura ring.
Thanks! it worked well for my fireplace.
Hi Celik,
I’ve found that you have the same Dimplex CAS400LNH as mine !!!! (reading the reviews of this fireplace shop where you said that you have controlled by ESP32 CPU)
Would you share the commands you have found, please ?
I want to control it with an ESP32 like you and then with my Node-Red domotic system.
Thanks in advance !!!
Would you share de ESP32 code for DIMPLEX 400 control ???
my email is jm8513@gmail.com
I followed your steps trying to reverse Tuya drawer lock but it din not work. I can connect for a while to the device via nRF Connect (for mobile and for desktop versions), i know devices’ name and adress, but it does not show in Wireshark. Even if I try to add the LE adress (according to NS’ infocenter) it does not help.
Any idea how I could sniff this communication between the Tuya’s app and the device?
I am going to use the Circul+ ring (https://bodimetrics.com/product/prevention-circul-wellness-ring/) to monitor heart rate and body motion so as to detect REM sleep. I previously did this with a fingertip pulse detector (https://pulsesensor.com/) and micro-accelerometer connected to an Arduino microcontroller, and I was able to reliably detect REM sleep, but my device is rather bulky and awkward to wear while sleeping. I really enjoyed Mr. Patterson’s 3 tutorial videos on hacking BLE, and I was wondering if he (or anyone) could recommend a good, current sniffer (hopefully with its firmware already installed) for using with Wireshark. I was having trouble identifying exactly which sniffer he used and where to find it. Thanks.
I will order an nRF dongle, already have Wireshark installed but just one question: what is a “windows box”.
What if the device responds to written commands in the nrf connect app, but does not respond to the same commands in the esp32 code?