Selling power banks these days isn’t easy, as you can only stretch the reasonable limits of capacity and output wattage so far. Fortunately there is now a new game in town, with ‘smart’ power banks, like the Anker one that [Aaron Christophel] recently purchased for reverse-engineering. It features Bluetooth (BLE), a ‘smart app’ and a rather fancy screen on the front with quite a bit of information. This also means that there’s a lot to hack here beyond basic battery management system (BMS) features.
As detailed on the GitHub project page, after you get past the glue-and-plastic-clip top, you will find inside a PCB with a GD32F303 MCU, a Telink TLSR8253 BLE IC and the 240×240 ST7789 LCD in addition to a few other ICs to handle BMS functions, RTC and such. Before firmware version 1.6.2 you can simply overwrite the firmware, but Anker added a signature check to later firmware updates.
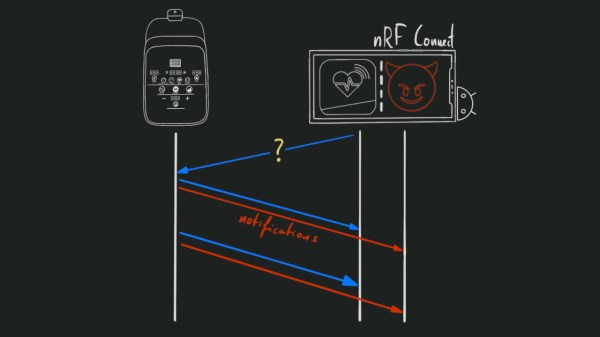
The BLE feature is used to communicate with the Anker app, which the official product page advertises as being good for real-time stats, smart charging and finding the power bank by making a loud noise. [Aaron] already reverse-engineered the protocol and offers his own alternative on the project page. Naturally updating the firmware is usually also done via BLE.
Although the BLE and mobile app feature is decidedly a gimmick, hacking it could allow for some interesting UPS-like and other features. We just hope that battery safety features aren’t defined solely in software, lest these power banks can be compromised with a nefarious or improper firmware update.
Continue reading “Hacking The Bluetooth-Enabled Anker Prime Power Bank”