Who doesn’t know the struggle? Buying an interesting piece of hardware for a song and a dance, and then finding that the device’s firmware and/or configuration file is locked down with various encryption or obfuscation methods. This was the experience [Ali Raheem] had when he got a TP-Link TL-MR3020 V3 for a mere 18 British Pounds, intending to use this 4G-capable router to increase internet reliability.
Naturally this can all be done when staying inside the vendor-provided marked lines, which in this case meant ignoring the encrypted configuration files. As the owner of the hardware, this was of course unacceptable and thus [Ali] got a firmware image from the TP-Link site to see what could be gleaned from it in terms of encryption keys and other hints.
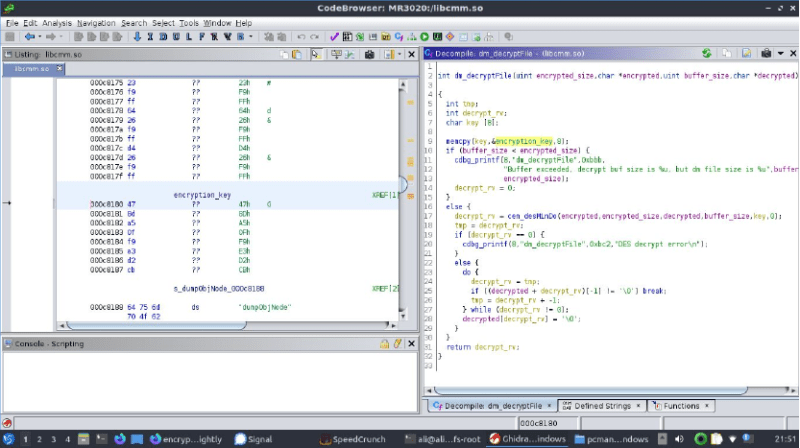
After obtaining the TP-Link-provided BIN file, the application of binwalk helpfully extracted the files embedded in it, followed by John the ripper decrypting the passwords in the /etc/passwd.bak file, and ultimately finding the encrypted /etc/default_config.xml file. Searching for this filename string in the rest of the extracted files led to /lib/libcmm.so.
Dropping this shared library file into Ghidra to disassemble its code, [Ali] found a function suspiciously called decryptFile. Inside was a reference to the global key string, which when tossed into OpenSSL and after some fiddling turned out to decrypt the XML configuration file in des-ecdb mode. From this point dropping in one’s own configuration files should be no problem after encrypting them to make the firmware happy. Nice work!















It’s a shame that OpenWRT has got too big to support this and the WR-703n – they’re nice little (with the emphasis on little for the 703n!) boxes.
I’m pretty sure you still can build your own image for 703n, if you drop WebGUI (and probably add USB storage support for extroot to install functionality later).
Or you can switch to MR3020v3 from the article, which is tiny bit bigger, but with 8MB flash and 64MB RAM it’s still supported (although that’s running out as well)
There are also Gl.Inet devices like GL-AR150 (same platform as WR-703n with 2 ethernet ports and 8/64 memory) and GL-MT300N-V2 (same platform as MR-3020v3, 2x ethernet, 16/128 memory), both supported by OpenWRT and, despite dual ethernet, smaller than WR703n (maybe a bit thicker)
+1 for the AR150 (and the entire GLI line). The 150 in particular is a sharp sharp multi tool if you know how to use image builder.
https://openwrt.org/toh/tp-link/tl-mr3020_v3 :P
MR3020, despite it’s marketing is in no way, shape or form 4G capable. It just has an USB port you can stuff a modem in.
It’s supported by OpenWRT (previous versions too, but you need to build your own image with bare minimum of packets due to 32MB flash), so while [Alis] approach is a nice experiment in breaking in, the practicality of it is limited.
TL-MR3020 v3: 8MB flash, 64MB RAM. Good enough for latest openwrt without any tweaks.
On this note: https://openwrt.org/toh/tp-link/tl-mr3020_v3
v3 yes, but v1 and v2 require careful package selection to fit in the 4MB flash
Sure, but this article is about v3 ;)
Correction: 4MB Flash, 32MB RAM
Great article. I like the description of what tools are available, and how they can be used. I might never need to do this, but if I did I’d find this article with a handy reference guide. Just like with textbooks it’s useful to have a worked example.
Am I the only nut job that wraps open wrt firmware updates in PGP? Sure the key is on the flash – but no one is getting it from the binary in flight.
Not sure these are strictly 4G Capable – They take a PPP / Serial USB or Ethernet CDC device and share it.
This may be illegal in the US per the DMCA
You bought the hardware. You should own it. Besides, Biden is currently making moves on right-to-repair that should also protect these kind of things.
What do you mean by “this? The article itself, the act of publishing it, the act of reading it, conspiring to do it, purchasing the parts to do it, making the modification, using the modified device, or selling the modified device? Please explain what you mean.
Why are more and more router vendors making it harder for people to make full use of the devices they purchased? Are they annoyed that people are taking cheap home routers and (through replacement firmware and other upgrades) adding features otherwise only available in more expensive models from the same vendor? Are they annoyed that people are taking old routers and adding features that you could otherwise only get by buying a new one? (thus extending the life of the device instead of making the company money by buying a new one) Are ISPs (who often ship these routers to their customers as part of their internet plan as was the case with the TP-Link router I got from my ISP) pressuring them to do it? Router vendors deciding that locking the whole thing down is the easiest/cheapest way to keep regulators off their back when it comes to routers being modified to transmit in ways they aren’t allowed to transmit?
Because their toolchain enables that by default or very easy, and they see it as a positive argument for security.
But if you don´t like that, there are also vendors selling hardware installed with openWRT like 8devices product, and some selling OpenWRT-supported SBC boards, like Olimex.
The question you should be asking yourself is, “why am I preaching to the choir on hackaday?” Maybe you should direct your complaints to your elected representatives who can actually do something about it.
It is because the telecommunications providers that these devices are being sold to for bundling with services are requiring protections against supply chain attacks, consumers “hacking” the devices which cause trouble on their networks and government organizations are requiring stricter rules for telecommunications gear (which is actually the biggest reason these things are being done these days).
This is not a ploy to refuse right to repair, in fact we/they would never actually “waste” the time to secure things unless forced to because there are always 100s of checkboxes on these products you have to check and the last thing on marketing and product management’s mind is security and making sure the box is secure.
People think malicious intent and it is quite the opposite; been working in this industry the last 25 years, no one is trying to remove your ability to repair…
How have you worked in this industry so long without understanding planned obsolescence?
The limited flag is a cost saving measure, sure, but it also means these current devices are often overloaded by mundane tasks. Many Monroe have extremely poor cooling, and prices maintain despite now being higher than the cost of DIY.
With pro gear the thing that lights my ass on fire is software throttled hardware. From security appliances that are limited to a set number of connections to devices that require more $$ to unlock more throughput. The worse is the stuff you pay for and it gathers analytics and phones home but costs you an annual fee to get the service part of the service.
TL-MR3020 is more trouble than worth when it comes to USB 3G/4G modems, constant drops, manual reconnects..
I had to do this to find the root password on an SGI system I was given. Luckily, it was Unix and the previous owner had left the “demo/demo” user active. I was able to read the /etc/passwd file and John the Ripper was used to extract the encrypted password from the encrypted string.
Several months later, the previous owner found his backup copy of the root password..