It seems I have made my tiny, indelible mark on internet security history, with the term “protestware“. As far as I can tell, I first coined this particular flavor of malware while covering the Faker.js/Colors.js vandalism in January.
Yet another developer, [RIAEvangelist] has inserted some malicious code (Mirror, since the complaint has been deleted) in an existing project, in protest of something, in this case the war in Ukraine. The behavior here is to write a nice note on the desktop, preaching “peace not war”. However, a few versions of this sample have a nasty surprise — it does a GeoIP lookup, and attempts to wipe the entire drive if it detects a Russian location. Yes, node-ipc versions 10.1.1 and 10.1.2 contain straight-up malware. It’s not clear how many users ran the potentially malicious code, as it was quickly reverted and released 10.1.3. Up-to-date versions of node-ipc still create the desktop file, and Unity Hub has already confirmed they shipped the library in this state, and have since issued a hotfix.
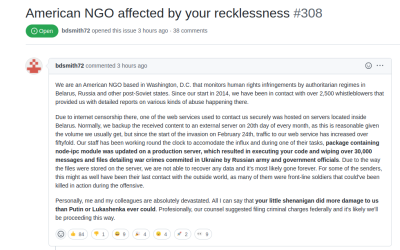
This story is continuing to develop, but there was also an issue raised by a node-ipc user who claimed to be associated with a human rights organization that worked with observers in Eastern Europe. The unsubstantiated claim is that node-ipc ran on their whistle-blowing infrastructure, and the malicious code in version 10.1.1 or 10.1.2 wiped a massive collection of evidence. While this could be a hoax — anyone can claim anything on the internet — there is a threat of legal action, which would give substance to the claim. If we catch wind of anything more developing, we’ll update you on it.
This recurrence of protestware is going to force the Open Source world to come to some conclusions about what sort of social and political commentary is appropriate in widely-used projects. Wiping hard drives is obviously way beyond the pale. It’s not entirely clear that code was intended to be rolled out to the public, as it was picked up in an unrelated changeset, suggesting either an accidental inclusion, or an attempt to smuggle it in. But what about the creation of a virtual pamphlet on the user’s desktop? I suggest that this, too, is unacceptable for a serious project. What about rhetoric in log output? The impetus behind protestware seems to be unchanging, so we’ll need to work out the answers to such questions.
Netfilter Not-An-RCE
Up next is the announcement of another Linux Kernel vulnerability, CVE-2022-25636, this one an out-of-bounds write in the Linux firewall code. If you’re suddenly having heart palpitations at the thought of Remote Code Execution, try to relax. This flaw is serious, but just like DirtyPipe we covered last week, it’s entirely limited to a local user account that can run shell commands. A pair of tricks allows any user the ability to trigger the flaw with any hardware, meaning that it’s a straightforward elevation of privileges.
Making this a more serious issue, there are at least two Proof-of-Concepts available: one in the disclosure linked above, and the second on Github from [Bonfee]. The problem was introduced in kernel 5.4, and fixed in 5.16.12, 5.15.26, 5.10.103, 5.4.182, and has landed in 5.17 which is due to be released very soon. Unfortunately, there are incorrect reports that this CVE was fixed in 5.6.10, including the NIST page on the bug. The problem is that 5.6.10 was released more than a year before the problem was found. Adjust your response accordingly.
How to Brick Thousands of Satellite Terminals
You may have seen the story of several thousand wind turbines in Europe suddenly lost their satellite link to their controllers. There has finally been enough information released to piece together an educated guess as to what went wrong. [Ruben Santamarta] combines his experience breaking satellite systems with the hints given in official statements, and presents a likely explanation. First, the outage corresponded with the war in Ukraine and was being investigated as a cyberattack. This could have been a simple DDoS, but a military official stated that “terminals have been damaged, made inoperable and probably cannot be repaired.” DDoS attacks don’t generally brick devices.
What does brick devices is flashing bad firmware to them. The most likely scenario is that Russian attackers either compromised a ground station, or spoofed it. They used this connection, and the TR-069 protocol, to send a malicious firmware update. This attack knocked out terminals in Ukraine, Czech Republic, Slovakia, and Germany.
TLStorm
It’s a catchy name, a logo, and even a slick informational video. Is TLStorm more than a flash-in-the-WAN? Maybe — there are a trio of serious vulnerabilities at play. Researchers at Armis found these in APC Smart-UPS firmware.
Let’s start with the Firmware authentication problem. To really ensure that malicious firmware can’t be installed, devices use a signed and encrypted approach, where the signing key is held very securely by the manufacturer. Smart-UPS firmware was simply being encrypted with a symmetric key, meaning the same key is used to both encrypt and decrypt the firmware. The check done in the target device was to decrypt the new firmware, and sanity-check it, usually by looking for a magic value in the header. The problem is that every device that shares firmware compatibility is also sharing the same encryption key. Extracting the key from one unit allows an attacker to produce valid-yet-malicious firmware for all of them.
Problem two is a Man in the Middle TLS attack. This one takes advantage of state confusion in the nanoSSL library shipped with the APC devices. The client tries to communicate with the APC cloud, and the attacker interrupts the initial handshake. Now that the connection is in this state, the attacker can send a TLS resumption message, and the client accepts it, skipping the all-important verification of the HTTPS certificate.
The final exploit is an RCE, taking advantage of TLS fragmentation. The attacker sends a fragmented message, and then keeps sending fragments beyond the expected byte-count, overflowing the allotted buffer. This one allows for full control, and chains into the malicious firmware problem. Put together, these give an attacker a very wide range of options, from powering off downstream devices, to modifying the firmware to induce unsafe operations. The Hollywood trope finally comes true, where the hacker can make devices explode remotely.
Bits and Bytes
That nifty device you carry everywhere has a baseband processor and firmware on it, and that has historically been a very opaque component. There’s a new tool to get some insight into what that firmware is doing, FirmWire. It’s a baseband emulator, intended to let you fuzz, debug, and otherwise delve the secrets of your baseband firmware.
Is it just me, or has Google Chrome had an uptick of in-the-wild exploits recently? Apparently the trend is real, and researchers at Google have noticed. They point out a few reasons for the trend. Chromium is the biggest browser game in town, so naturally it’s the one being attacked. A counter-intuitive point is that better security artificially inflates the vulnerability count, as sandboxing requires a real attack to chain at least two bugs together to accomplish anything worthwhile. The post rounds out with a discussion of Google’s plans to keep ratcheting the code in Chrome/Chromium to a more secure standard.
Remember the impressive WordPress fuzzing tool we covered a few weeks back? A few commentors wanted to know where to find the source for the new tool. Wpgarlic has now been released, and is ready for you to use, improve, and unleash your hacking creativity upon. If you find something particularly interesting with it, be sure to let us know!
















So you’re saying that the “Netfilter RCE” is not an RCE?
*facepalm*
I am curious why one would use a satellite connection for a wind turbine…
Off shore I can reason it as somewhat logical, but on land?
Surely a wind turbine being typically 60+ meters tall to the hub would be able to just use GSM, LoRa, or just run a boring old DSL line or fiber to each tower together with the power cable.
Satellite connections tends to be fairly pricey compared to the other options.
Though, the connection method doesn’t really affect the attack surface much, the controller in the tower can still be bricked if it has such a vulnerability.
I’m not sure it makes any sense on the water either – the damn things have to be connected the grid at somepoint to do anything and you can send data down the power line if you really want to, and with how many of them would be in each little cluster with a direct line to the grid for that cluster it seems daft to use satellite…
I really want to know what the thinking was behind that now, as its so illogical on the face of it, but maybe there is a good operational reason – perhaps certainty of command and control if the lines get damaged?
One can always have 2-3 lines out to the farm, tapping into it at different sections and then do radio internally. So even for redundancy reasons I don’t see the logic of satellites in this application.
Though, the whole “they use satellites” is based on what is stated in the article. But according to the article linked to the statement is: “Germany’s Enercon moved forward and acknowledged that approximately 5800 of its wind turbines, presumably those remotely operated via a SATCOM link in central Europe, had lost contact with their SCADA server.”
But why one would use satellite in central Europe is also a bit weird. Since there is literally land as far as the eye can see. And anyone who has looked at a map of Europe knows that there is villages and smaller towns literally everywhere. (except nature reserves and national parks, but one don’t build wind turbines in those areas.) So getting a GSM connection should be trivial. And in Europe one can get quite decent xDSL connections as well. (a friend of mine living in a rural village in Hungary gets 50+ Mb/s all day long on xDSL. Not that a SCADA interface needs many kb/s to work.)
Oh I agree entirely it seems quite odd, but maybe there is a valid reason, and the only one I can think of that seems vaguely plausible is having a very reliable and safe connection for control, as a satellite link is very hard to crash the HGV into or have a tree drop on – all the stuff that happens and takes out peoples internet or power for a day or two (perhaps longer if its a big storm), as nothing on the ground should be able to accidentally damage that link…
Most wind farms to what I have seen bury their cables bellow ground. So trees, vehicles, etc shouldn’t be a problem.
Personally I just can’t see a particularly good reason. Redundancy isn’t that hard to get via terrestrial links either. Nor is it expensive in most areas, especially for a larger wind farm that already looks at installation costs in the many millions and above.
I think it is mainly engineering laziness and little else.
Throwing in a satellite modem just means that one don’t have to pay for an engineer doing a more suitable solution that isn’t having 1 point of failure. (we see similar trends in programming these days as NN/AI is getting used for simpler and simpler tasks that isn’t hard to just program.)
Thanks for the link to wpgarlic!
About protestware: Software has to be political neutral. If its not, then it will only bring bad to the people that use it. Why should I want to use software that will bring anything bad to anyone. Politics have nothing to search into software or software development. Fuck you people that can’t divide between their projects and their own political sight. Oi!
I completely agree, now that they’ve done this many people will have lost trust in them and consider them and their projects unreliable from now on. I know I wouldn’t want to run software that at a moment’s notice could delete my files based on how someone is feeling that day and their political opinions. I don’t know what this software does but if it’s used by ordinary people or businesses in Russia then it’s them that will suffer not the government and depending what they store on the computer/server, it could be the end of their business, if it’s on home computers or a NAS then important documents and maybe family photos etc that have been deleted, nothing that will effect the government, just cause suffering to the people. They trusted that software and it’s creator to develop good, working, safe software and they have just completely broken that trust. Even putting a message on the desktop is going way too far and breaching the boundaries of what the software should do, if I’m using someone else’s code, I want it to do what it needs to do and nothing more, if it does anything like this or puts a political message on my desktop then I would seriously consider removing it and looking for an alternative.
I say find the person who wrote it and arrest them for computer misuse charges and for creating malware, if it was actually distributed then charge them with distributing malware too. It looks like that may happen though if this goes to court. This sort of behaviour has no place in open source development which is primarily built on trust.
one word: google.
google has constantly screwed over everyone time and time again for both profit and their political ideals.
they need to be regulated.
case in point, search suggestions.
case in point, how they regularly destroy competitors by delisting them, eg: all the websites that were price aggregates to find the lowest price on any item. they dropped them down several pages and would always recommend “Google shopping” which sucked and never found the lowest price, but instead directed you to a paid advertiser.
case in point, try to set up your own email server. google will block it.
case in point, they kicked practicing doctors off of youtube for sharing how they had success in treating covid, not to mention various other illnesses, or anything they deem unfit.
screw google.
Using software without auditing it has become the norm in lazy software deployment. So if you business is doing that then it purely down to the business for not having a decent software deployment standards, quality control and auditing.
“conclusions about what sort of social and political commentary”
Any sort of COMMENTARY is appropriate, full stop, that is a simple free speech issue. Malicious code to wipe computers because it doesn’t like their geolocation* isn’t commentary though. Spftware itself really must stay neutral, whether the develoerp wants to have a few printfs of “f*** putin” in places where printf won’t break a user’s workflow is of no consequence, but refusing to work, or taking malicious actions isn;t ok for software. Software is supposed to be infrastructure for all, it isn’t right to make it discriminate on political lines.
*remember it is afterall Putin who is, among many other leaders, guilty of war crimes, it is not ordinary Russians to blame