When you think old school handheld games, you probably imagine something like Nintendo’s Game Boy line or the Sega Game Gear. But outside of those now iconic systems, there was a vast subculture of oddball handheld games vying for a chunk of an adolescent’s weekly allowance. Many of these were legitimately terrible and frankly aren’t worth remembering, but a few offered unique features that were arguably ahead of their time.
One such game was Hasbro’s short-lived P-O-X. As explained by [Zachary Ennenga], the game didn’t spend much time on store shelves as its core concept of defeating undetectable alien invaders hell-bent on destroying our way of life proved to be more than a little problematic when it launched in September of 2001. But that doesn’t mean it didn’t have some cool ideas, such as a wireless ad-hoc multiplayer capability that let your game autonomously battle it out with other units that got close by.
Fascinated by this feature since his youth, [Zach] set out to study how this relatively cheap kid’s toy was able to pull this off back when even the flagship handheld consoles were still using physical link cables for multiplayer. He was aided in his quest by a particularly helpful patent, which not only gave him clues as to the frequency, data rate, modulation, and encoding of the RF signal, but even explained the game’s logic and overall structure. A lot of what was in the document seemed wishful thinking on the part of Hasbro, but reading through the marketing speak still uncovered some salient technical details.
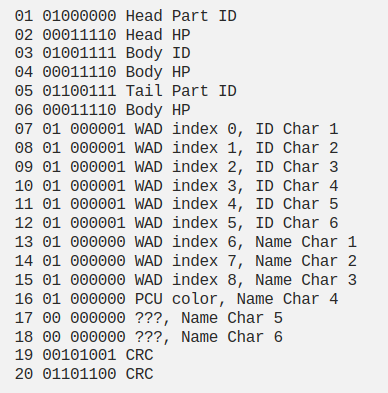
Armed with an RTL-SDR, GNU Radio, Inspectrum, and a bit of Python, [Zach] was able to identify the signal and begin the process of decoding it. This is where things get really interesting, as the details of his reverse engineering process are widely applicable for all sorts of unknown RF signals. Even if you’re like most people and have nearly zero interest in failed handheld games of the early 2000s, it’s well worth a read. The same techniques he uses to figure out the name and physical characteristics of the invisible foe his game is transmitting could one day help you figure out how to manipulate the data from that wireless weather station you’ve got in the backyard.
Once he figured out the major parts of the protocol, [Zach] moves on to creating his own packets and broadcasting them out in such a way that the real hardware will recognize it. He even comes up with some code that will automatically battle games which wander within range of his Yardstick One, which may come in handy during the inevitable P-O-X Renaissance.
While this might seem like a lot of effort to put into a game that most people have never even heard of, we’ll remind you that some of the greatest hacks to ever grace these pages have been born of similar pursuits. Even if you’re the only person in the world to directly benefit from your current line of research and experimentation, there’s still plenty of like-minded folks in this community that are all to happy to cheer you on from the sidelines.
















The stars must have just aligned, because not even a week ago i went to ebay to find one of these. I remembered loving them as a kid and wanted to see if i could somehow dump the ROMs and emulated it. Crazy to think someone else in the world also got a hankerin’ for this thing.
I had the green one!
Yeah this is weird bc I had a green one and I just was looking for one a month ago….
I just thought about POX when browsing tomagatchis recently. I doubt this is coincidence… Those RF signals must have done something to our brains.
You’d think he would have implemented P-O-X over LoRa to bridge the hundreds of miles to the next person that owns one. ;-)
Or alternatively it would be rad to do what stacksmashing did with GB Tetris and bring these things online with some sort of internet enabled adapter and matchmaking. Feels like not a terrible leap.
Shouldn’t line 06 in the packet description above read “Tail HP”?
I forgot about these things. Man that’s crazy. I was obsessed with mine but I’m not sure if I even actually liked it.
Kudos. That’s real hacker spirit! ^^
Wow! Core memory unlocked. I had one of these and loved it.