Have you ever found yourself in a crowded restaurant on a Saturday night, holding onto one of those little gadgets that blinks and vibrates when it’s your turn to be seated? Next time, bust out the HackRF and follow along with [Tony Tiger] as he shows how it can be used to easily fire them off. Of course, there won’t actually be a table ready when you triumphantly show your blinking pager to the staff; but there’s only so much an SDR can do.
 Even if you aren’t looking to jump the line at your favorite dining establishment, the video that [Tony] has put together serves as an excellent practical example of using software defined radio (SDR) to examine and ultimately replicate a wireless communications protocol. The same techniques demonstrated here could be applied to any number of devices out in the wild with little to no modification. Granted these “restaurant pagers” aren’t exactly high security devices to begin with, but you’d be
Even if you aren’t looking to jump the line at your favorite dining establishment, the video that [Tony] has put together serves as an excellent practical example of using software defined radio (SDR) to examine and ultimately replicate a wireless communications protocol. The same techniques demonstrated here could be applied to any number of devices out in the wild with little to no modification. Granted these “restaurant pagers” aren’t exactly high security devices to begin with, but you’d be horrified surprised how many other devices out there take a similarly cavalier attitude towards security.
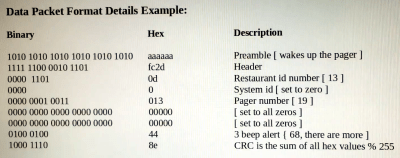
[Tony] starts by using inspectrum to examine the Frequency-shift keying (FSK) modulation used by the 467.750 Mhz devices, and from there, uses Universal Radio Hacker to capture the actual binary data being sent over the air. Between studying the transmissions and the information he found online, he was eventually able to piece together the packet structure used by the restaurant’s base station.
Finally, he wrote a Python script which generates packets based on which pager he wants to set off. If he’s feeling particularly mischievous, he can even set them all off at once. The script outputs a binary file which is then loaded into GNU Radio for transmission via the HackRF. [Tony] says he’s not quite ready to release his script yet, but he gives enough information in the video that the intrepid hacker could probably get their own version up and running by the time he gets it posted up to GitHub anyway.
We saw some very similar techniques demonstrated at the recent WOPR Summit security conference, so once you’re done hacking the local restaurants, you can take these same lessons and apply them to the rest of the Internet of Things. If you’re wondering, it’s even easier to eavesdrop on the non-restaurant pagers.

















To have such a convenience at a restaurant would possibly make the HackRF, a worthwhile purchase!
B^)
Shrink down to a watch, then we’ll talk.
You might need to donate funds for that.
I would spend double for a watch sized device if it had USB-C, and an antenna out that would allow more than one antenna and be switchable between channels.
If it told the time as well, even better.
you could use a smartwatch as a remote
“Granted these “restaurant pagers” aren’t exactly high security devices to begin with, but you’d be horrified surprised how many other devices out there take a similarly cavalier attitude towards security.”
Not really. Security costs, in design, implementation, as well as maintenance. Most are more curious about what happens on social media than what’s under their nose.
Make it portable and cheap : pizero + rpitx (5$) should do the trick.
Sure… But that necessitates attacking *only* those specific devices.
Just wait. I have a solution for that :D It … might… be hosted on HaD soon :) I guess you’ll have to remember the ‘CrankyLinuxUser’
And BTW, **THANK YOU** for writing Rpitx :)
But sheesh, I couldnt show that logo when I did a talk at my company :P ye’ ol’ reach-around!
Old joke https://www.youtube.com/watch?v=_jJEJUsdQ40
This could be used to intercept when another pager is being triggered and interfere with it.. that way they miss their table and you can scoop it up!
Making everybody’s pager ring at the same time
> tv b gone.
@Hackaday … more articles like this pls! Well done.
So because it’s not “secure”, that gives you the freedom to essentially inconvenience multiple people ? Great going azzhats ! Be proud, no wonder “hackers” are viewed with disgust by the ‘general public’.
Using that logic, stealing a car that the owner left it’s keys in the ignition should be a “pass” and the thief should not be charged with any crime.
eFF’ing disgusting scumbag ! hopefully “the man” will nail your pathetic sorry ass to the wall and make an example of you.
I see a great difference between causing a little inconvenience and stealing a car (which normally has a 4 to 6 figure value). This here is more like a prank.
hmmm… so what you basically are saying is that YOU think it is OK for big companies to sell expensive stuff with crappy locks on it. Because well… those locks are just for show, because stealling is illegal, so nobody will ever notice that some locks are crap or some security is not secure at all.
Thanks to these “hacker” guys, who use harmless showcases like shown in this project, it is demonstrated that the world isn’t as secure as some people want the world to believe.
There are always real “bad guys” exploiding these crappy systems, but they don’t brag about it.
The “good guys” do brag about it and thereby force the manufacturers to come up with better systems.
So, please Bufford, say you are sorry and accept that the world isn’t as perfect as you’d like.
PS: the real problems would start is somebody decides to make a project like tv-be-gone and allows every kid on the block to pull these pranks, just for pranking not for technological progress. A good name would be meal-be-gone.
The world is as perfect as you make it.
Damn dude, take a breath. Did someone forget their Prozac?
Buford, your “quotes” makes me think you are a “Russian troll” trying to rile people up for no reason other than “the lols.”
You, “sir,” are the “eFF’ing disgusting scumbag” here.
You can steal a modern car with your smart phone and a soldered together antenna device.
I still can´t wrap my head around “waiting to get seated at a restaurant”. That is just non existent in my corner of the world,
if I had to wait to sit down; I´d just take my business anywhere else. If there is actually no table free, there will be one at a different place. + there is always the option to reserve beforehand.
Yes, other countries, other customs.
I know these beepers from a place at the riverside. A combination of restaurant and take away. Many people sitting outside of the place at the riverside sometimes order some take-away food like a hot-dog. This often takes a couple of minutes to prepare. So you get a beeper and go back to your friends instead of standing and waiting for 10 minutes. Very convenient and the range is at least 100m or 200m.
If you happen to walk in spontaneously and don’t have a reservation, it’s often not much of a wait after all. The better organized their “wait to be seated” area is, the better (often times you have access to a bar for aperitifs).
It’s common in many places, especially in the big cities, where you could certainly choose to take your business elsewhere but you may not opt to do so in the end because of quality reasons.
Perhaps, just perhaps, there is a tacit consensus among all of us that You Don’t Do It Just Because You Can (TM) — much like I don’t shit in front of my flat neighbour’s door “just because I could”.
Perhaps, just perhaps, there is a tendency in those of us dwelling on sites like Hackaday to nevertheless find out how those things work, and this involves finding their vulnerabilities.
Perhaps, just perhaps, you should think about why that triggers you that badly. Would you consider mis-using this knowledge for evil? Because most, most of us wouldn’t. After all, it is ridiculously simpe to bricolage a Molotov and throw it through the next window. Most of us Just Don’t — the world would be a hellhole otherwise.
Think about it. And oh, wipe that foam off your mouth, please.
Golden Rule kind of applies. We’re smart enough (hopefully) to know that if we start abusing our gifts, we’ll set up an environment where we no longer have nice things. e.g.drones, and/or get punished by society. Problem for some is recognizing were to draw the lines.
No, I will leave my nightmare drool where it is at.
If many of us are like me, there wouldn’t be anyway to stop us if we went on crime spree. Cars are easy to steal, Immobilizers are well understood and easy to replicate. Door codes can be hacked with a small screw driver and some common items.
Doing all of this is easy, it’s not any of this stuff is difficult. That’s like saying using a Kali setup and packet interception by an asshole to hypnotize and try to turn a grown man gay has never happened. We know it has, because it was done by other members of this very site to one of this site’s longest readers and contributors
This is working for years in Liège (Belgium) Brasserie Sauvenière (https://www.grignoux.be/fr/brasserie-sauveniere). In this brasserie, customer order on counter and is notified when the meal is ready. Men have to come and pick up the plates.
I found this post unexpectedly interesting and reproduced it based on [Tony Tiger]’s YouTube video and GitHub. I had to copy the GnuRadio model off his video. I’d used my HackRF One for a few trivial receiving things, but this was the first “transmitter” use of it. While I believe it might be amusing to trigger all the pagers in a restaurant at once (are you listening Cheesecake Factory), I’d never do it (that’s my story and I’m stickin’ to it). Apparently people have been listening to and spoofing pagers for years.
I got 3 pagers off of eBay (older and newer models) cheaply enough. And while these pagers have their pager ID usually affixed to them, finding the restaurant ID is trial and error (so far as I know). Thankfully, my first pager had a restaurant ID of 3.
Interesting example of extending capabilities of various devices. Unfortunately, article emphasized a dishonest use.