In recent years you’ve probably seen a couple of photos of tablets and smartphones strapped to the armor of soldiers, especially US Special Forces. The primary app loaded on most of those devices is ATAK or Android Tactical Assault Kit. It allows the soldier to view and share geospatial information, like friendly and enemy positions, danger areas, casualties, etc. As a way of working with geospatial information, its civilian applications became apparent, such as firefighting and law-enforcement, so CivTAK/ATAK-Civ was created and open sourced in 2020. Since ATAK-Civ was intended for those not carrying military-issued weapons, the acronym magically become the Android Team Awareness Kit. This caught the attention of the open source community, so today we’ll dive into the growing TAK ecosystem, its quirks, and potential use cases.
The TAK ecosystem includes ATAK for Android, iTAK for iOS, WinTAK for Windows, and a growing number of servers, plugins, and tools to extend functionality. At the heart of TAK lies the Cursor on Target (CoT) protocol, an XML or Protobuf-based message format used to share information between clients and servers. This can include a “target’s” location, area, and route information, sensor data, text messages, or medevac information, to name a few. Clients, like ATAK, can process this information as required, and also generate CoT data to share with other clients. A TAK client can also be a sensor node, or a simple node-Red flow. This means the TAK can be a really powerful tool for monitoring, tracking, or controlling the things around you.
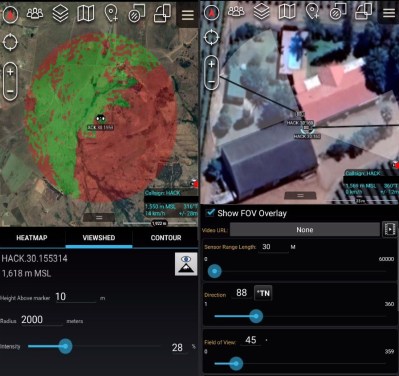
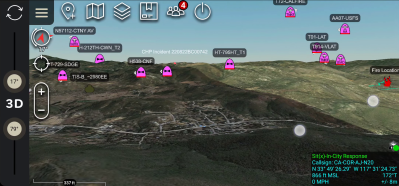
ATAK is a powerful mapping tool on its own. It can display and plot information on a 3D map, calculate a heading to a target, set up a geofence, and serve as a messaging app between team members. Besides using it for outdoor navigation, I’ve used two other built-in mapping features extensively. Viewshed allows you to plan wireless node locations, and check line-of-sight their line-of-sight coverage. The “sensor” (camera) markers are handy for planning coverage of CCTV installations. However, ATAK starts to truly shine when you add plugins to extend features, and link clients in a network to share information.
Networking
To allow networking between clients, you either need to set up a multicast network or a central server that all the clients connect to. A popular option for multicast communication is to set up a free ZeroTier VPN, or any other VPN. For client-server topologies, there are several open source TAK servers available that can be installed on a Raspberry Pi or any other machine, including the official TAK server that was recently open sourced on GitHub. FreeTakServer can be extended with its built-in API and optional Node-RED server, and includes an easy-to-use “zero-touch” installer. Taky, is another lightweight Python-based server. All these servers also include data package servers, for distributing larger info packs to clients.
Plugins
If an internet connection is not available where you are going, there are several off-grid networking plugins available. HAMMER acts as an audio modem to send CoTs using cheap Baofeng radios. Atak-forwarder works with LoRa-based Meshtastic radios, or you can use APRS-TAK with ham radios.
Plugins can also pull data from other sources, like ADSB data from an RTL-SDR, or the video feed and location information from a drone. Many of the currently available plugins are not open source and are only available through the TAK.gov website after agreeing to terms and conditions from the US federal government. Fortunately, this means there is a lot of space for open source alternatives to grow.
For further exploration, the team behind the FreeTAK server maintains an extensive list of TAK-related tools, plugins, info sources, and hardware.
Tips to get started
At the time of writing, ATAK is significantly more mature than iTAK and WinTAK, so it’s the best option if you want to start exploring. iTAK is actually a bit easier to start using immediately, but it’s missing a lot of features and can’t load plugins.
Opening ATAK on Android for the first time will quickly become apparent that it is not exactly intuitive to use. I won’t bore you with a complete tutorial but will share a couple of tips I’ve found helpful. Firstly, RTFM. The usage of many of the features and tools is not self-evident, so the included PDF manual (Settings > Support > ATAK Documents) might come in handy. There is also a long list of settings to customize, which are a lot easier to navigate with the search function in the top bar of the Settings menu.
No maps are included in ATAK by default, so download and import [Joshua Fuller]’s ATAK-Maps package. This gives ATAK an extensive list of map sources to work with, including Google Maps and OpenStreetMaps. ATAK can also cache maps and imagery for offline use. ATAK only has low-resolution elevation data included by default, but you can download and import more detailed elevation data from the USGS website.
To connect with others interested in TAK you can also check out the TAK Community Discord server.
Have you played around with anything in the TAK ecosystem? Share your experience and ideas in the comments below.
















I wonder if the US left any backdoors for themselves. I can see a strategic advantage to having people install their software.
Nothing is free.
Thinking the same. I would trust software coming out of the US military/government as much, as I would trust Chinese software..
What about tor?
..and google??
Google is a private company, and thus everything is centered around harvesting data
Nope
If it’s free and open source, I am fine with software from any country or government, especially if it’s audited by a big and diverse community of users and developers. Any standard corporate software from MS or Apple is less trustworthy than a piece if chinese FOSS software.
Bait and switch. The store app is not like the other
Almost certainly ….. I’m giving it 99.90 % true.
It’s opensource. So you (or a programmer if you aren’t one) can check the source code to find any backdoors. You can check the traffic too to detect information going to where it should not go.
It’s Open Source, you can check the source for that. UNLESS it has some closed source software that is needed for it to work.
Otherwise, it doesn’t matter if it’s there, by the contrary, it it is open source, they would probably be giving up secrets on how they do it, not a good policy!
And frankly anyone using it without thoroughly checking for back doors deserves what they get.
The “backdoor” lies in not making it intuitive for someone without the training, then not including any training, or any specialized military plugins, or high resolution real-time data.
Hello! The FreeTAKserver can be easily installed with our Zero-Touch installer, and training for the ATAK and WinTAK app suite is freely available on the TAK Community Discord server, as well as https://www.tak.gov if you make an account there.
Hello! I can’t speak for the original Raytheon server, but our codebase for FreeTAKserver is freely browsable on Github. Let me know if you have any questions!
Ghidra was opensourced…
It’s open source. If there are back doors, the community would find them. Then they would fork the software, remove all tracking and use their own version. That’s how open source works. That’s why it’s secure and safe to use.
How come people still don’t understand this?
In theory, theory and practice are the same, in practice they are not.
Open source has not worked as Stallman theorized and you derp. There aren’t infinite eyeballs.
This is partly true.. requires a lot of work, people going through each line and verifying, that no “secret” code can be executed. There are even competitions in writing “secret” code, which looks innocent..
Sounds like it might be useful for large open field events also, hacker camps, rally marshalling, festivals.
You’re right, in fact, I gave a presentation on this at the TAK Product Center TAK Offsite 2022 in August: https://www.youtube.com/watch?v=QaVy15l2mxM
I was building a very similar kind of system 12 years ago to manage several art cars at Burning Man. We ended up not having more than 1 art car so the system was never completed. But I could see this software working very well if I bring back the idea of multiple linked art cars.
I was thinking it could make for a good base for a GPS based android/iOS war game (considering what it was originally made for it’d be pretty fitting 😛), there’s already a fairly decent albeit basic one on the play store called “counterforce” but imo this would make a far better base for one since it has all the important stuff done already, you would just need to add the actual game specific mechanics and you could probably leverage a lot of the pre existing systems to do that too
“At the of TAK lies…”
I think you are missing a heart.
Heart ATAK
Seems like an obvious thing for Burning Man.
Check out my YouTube channel for more info…https://youtube.com/channel/UCwQGzHkLVJiNzJJvh3lLGmA
Very cool, but I wouldn’t take a cellphone into a warzone lightly. Spoofed towers malware, or even just rdf could reveal your position.
It seems like the kind of thing whatwouls be most useful against low-tech foes; but against equals it could be quite a liability.
I think the point of CivTAK was really for non-military operations where those wouldn’t be an issue.
On the military side the US military has been using these cell phones for quite some time. I’m sure they take into account when they need they need to go silent and reduce signals, go passive, local only, and so on…
We saw the Russian’s fall prey to the opposite when they failed to go silent in Ukraine.
Just saying this software is glowing …
Having used it before some, TAK is really good. Not intuitive by any means but I’ve found it good for even just as soon as I get off the paved road for location data. Much easier than trying to find trail data on some regular apps sometimes and makes it a little easier to be spontaneous in where I go on a hike.
Taktischer Überfall Krempel
Some additional notes from a plugin community developer:
For all who are concerned about backdoors, the source code is something of a mess. If they had indeed put some in, they would have put more effort in hiding them than into writing the rest of the entire code.
For those who are otherwise interested in the TAK environment, be prepared because the public documentation is ehm, lacking, and the code is barely commented. But there are way more features than one would guess at first glance.
On the plus side, most of the features are modular and can be used/reworked through your own plugins.
There are also many features in the source code that are not configured or directly enabled, but rummaging through the code you can find lots of interesting stuff. So be brave and take a deep dive into the code (or the scarce public doc) to find hidden gems useful to you.
In conclusion, TAK is a much interesting project than what it may appear at first glance, and there are dozens ideas one could toy with, explore, develop.
Last but not least, a moment of shameless self-promotion: I’m currently working on OpenTakNavigation, a plugin for offline routing using graph-hopper and OSM data.
Feel free to check out my repo on github, right here: https://github.com/L-Belluomini/OTN
The plugin Hammer (which is apparently made by Raytheon’s open source department) seems a little odd – isn’t it illegal to do data transmissions over CB bands, which some walkie-talkies work on? AFAIK it’s legal to do data on MURS, which other walkie-talkies are on (but without repeaters).
I think your right. Seems like I remember in the amateur radio exam training you can tranot without license, but anything “encrypted” isn’t allowed. Now the caveat here may be that the data is “encoded” and not encrypted. In the other bands there are bamd and that have parts of each band that are dedicated to data. However the name plans aren’t law, just a “gentlemans agreement” set at some point in time. In theory as long as your transmitted isn’t putting out spurious transmissions on parts of the band that aren’t dedicated to amateur use or interfering with other transmissions, you could transmit right up against a voice channel/frequency that a current convo/call is happening. On the CB band there are dude with ultra wideband amplifiers that are illegal as hell. And they have been using them for decades and not hiding it. So, it’s a bit of area the FCC doesn’t have the resources and/or probably don’t car about much as is.
Baofengs (UV-5r, UV-9r, etc) transmit on ham bands, not CB. Data modes are permitted, so long as they are not encrypted. GMRS (UV-5G/X, BTech GMRS Pro) allow data transmissions with certain restrictions. MURS is indeed effectively “no holds barred” but the few channels and limited options for legitimate radios tamp that pretty hard. That and the 2 watt limit.
For the love of God, has anyone figured out how to turn on the Grid Lines in WinTAK [MGRS specifically]?
Thx