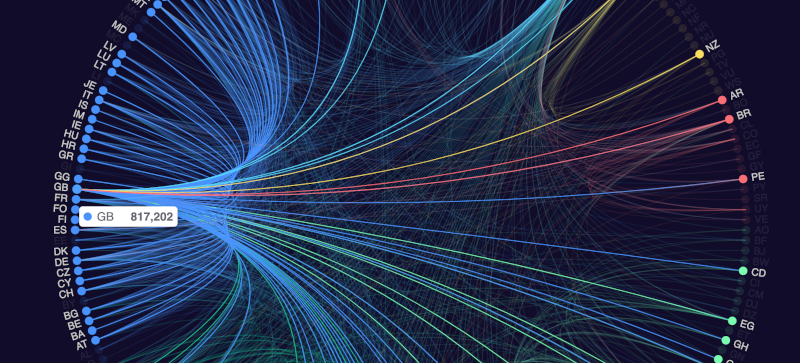
Have you ever noticed that some websites can figure out, at least roughly, where you are? Sometimes they use it to find you a closer content provider. Or they might block you from seeing certain things while offering you other things specific to your location. This is possible because there are databases that map IPs to locations. [Mark Litwintschik] looks at using those databases from an API or downloading them into your own database. He also shows some very large database queries, which is interesting, too. He uses IPInfo, although there are other providers. Some only provide a limited number of lookups, but there are plenty of free tiers for low-volume usage.
The database changes every day. Of course, each provider has a different way of getting data, and so there are differences. [Mark] compares the IPInfo dataset against MaxMind’s also free database. That involved comparing over 3 billion records! Actually, the 3 billion are the number of IPs that matched up in both databases. There were an additional 118 million that didn’t match and 34 million that were not in the MaxMind database.
Of course, of the ones that didn’t match it is hard to say which one was correct. As [Mark] mentions, IP address get sold — they are worth about $45 each, he says — so an IP that is in Texas one day might be in Johannesburg tomorrow.
What would you do with this data? Beats us. Maybe your home automation system wants to reject IPs from outside your country. Perhaps your robot needs to show a different user interface based on the remote requestor’s location. Tell us your thoughts in the comments.
We are surprised the value of the vanishing IPV4 addresses isn’t higher. Of course, that’s partly because your IP address isn’t always the one the rest of the world sees.
















Considering how leaky browsers are a lot can be found out.
IPv4 has gone from being quite useful from a website management standpoint, back in the day one could just IP block users from making new accounts and such. VPNs and Proxies have though partly made that practice irrelevant.
However, a lot of websites still blocks IPs to get rid of unruly users. Even if this practice is effectively inept these days, since IPv4 addresses aren’t really all that stuck to a specific home/user like it used to be just 10 years ago.
If anything, banning IPs is likely more detrimental than beneficial these days. Since one do stop the scrum for a few minutes, but for more popular websites one would end up blocking ones legitimate users that ends up with the IP address the next hour, day or week. (statistically speaking this becomes less likely the smaller the website is, but at some point the negatives outweighs the positives.)
I don’t have a fixed IP and sometimes gets a warning on Wikipedia that the IP address is blocked from editing. Even if I do have an account, at least the IP ban doesn’t “infect” the account and in turn “infect” new IPs as the user’s ISP lends them new ones over time, imagine how fast that would become a problem.
In the end, banning IPs to keep unruly users at bay is frankly rather inept these days.
However. Geo-restricting access is though a different debate and still applicable. Even if VPNs do poke holes in this practice as well.
Partly wonder how IPv6 stands in comparison.
I still block IP’s, but I wouldn’t permanently block an ipv4 address from anywhere a valid user could be. I’d prefer to add a captcha or other verification requirement if possible, and in either case the block would be temporary and conditional on anything relevant. My only permanent blocks have been when a foreign ip is spamming me with invalid authentication requests at a high rate, and I block their whole ip block because I don’t have any users in those locations and if I leave it alone they might eventually find a valid login if their guesses are any good.
(While IP’s do change hands to an extent, a random AS4134 address or really most APNIC addresses I’ve blocked probably won’t randomly be given to ARIN and be handed out to Joe Smith by his ISP.)
A high number of sources of such traffic (that I’ve detected) don’t bother using a VPN; at most they tend to work through addresses out of their ISP or hosting provider’s pools and then give up. Some of them only use a VPN if they see they’re not getting through the normal way. Out of that category, they usually send slower when on VPN, which is enough for me that they shouldn’t get a valid login before the password has changed.
Remember, there is no guarantee that the returned location info is actually correct ( https://arstechnica.com/tech-policy/2016/08/kansas-couple-sues-ip-mapping-firm-for-turning-their-life-into-a-digital-hell/ )
Is there any way to thwart this? What If I don’t want web sites I visit to know where I am? How can I turn this off?
Using a service like Tor is about the only way. You NEED an IP address to do anything on a network using TCP/IP, which is every network nowadays, so the only way to combat the databases is to use a different IP address.
There are a ton of commercial VPN services that would let you choose an exit in other parts of the US or other countries to throw off geolocation (though it’s a bit of a cat and mouse game as some sites/services specifically block IPs associated with commercial VPNs – you could also set up your own using TrailofBits’ Algo, which has worked well for me).
Honestly, there is no legitimate reason* for geoblocking. Either something should be open to everyone, regardless of who and where they are, or should only be open to a select group of people with the relevant password, or paid account or what have you. Access to a home automation system needs much better security than trusting geolocation (and you might go abroad anyway), setting a website’s language or local options can be done by the user with a selection of flags and country names to click upon (maybe that webpage visitor from Indonesia is a tourist on holiday would rather see things written in English) defaulting to english (the search engine they used to find the site was probably in english anyway) until told otherwise by the user clicking a different flag.
*”legislation” and “licensing” are not legitimate reasons, both are only created by government-aligned corporate cronyists to prop up corrupt monopolies which would instantly collapse if exposed to a proper free market
Definitely these databases can give interesting results to satisfy ones curiosity, but the number of actual use cases that are both practical (afterall most IPs are dynamic thesedays) and legitimate is pretty slim.
P.S. James Reed Feeney, look in to VPNs or Tor (for use as an entry-and-exit IP cloak rather than for accessing creepy .onion domains), either will let you beat illegitimate geoblocking
For an example, if you’re hosting a website for your small dry cleaning business in the middle of nowhere, Nebraska, there will be no legitimate users in some faraway country. But there will be plenty of malicious traffic coming from a number of countries, including false login attempts if there’s a password, and it makes a lot of sense to block that traffic.
Gee, my ISP gives me a /56 prefix, so I have 2**72 IPs of my very own. At the claimed $45 per, I’m apparently pretty wealthy. I must be a slaacer, as I haven’t even thought of cashing in.
These are not the IPv4 addresses you’re looking for.