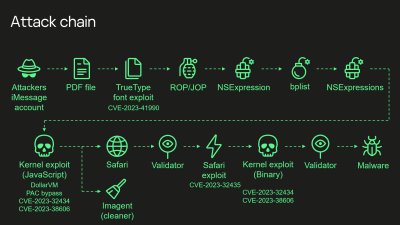
It’s not every day we get to take a good look inside a high-level exploit chain developed by an unnamed APT from the western world. But thanks to some particularly dedicated researchers at Kaspersky, which just happens to be headquartered in Moscow, that’s exactly what we have today. The name Operation Triangulation was picked, based off part of the device fingerprinting code that rendered a yellow triangle on an HTML canvas.
The entire talk is available, given this week at the 37th Chaos Communication Congress, 37c3. The exploit starts with an iMessage attachment, delivered silently, that exploits an undocumented TrueType font instruction. Looking at the source code implies that it was a copy-paste error where a programmer didn’t quite get the logic right for a pointer calculation. That vulnerability gives a memory write primitive that pivots into code execution. What’s particularly interesting is that Apple silently fixed this bug January 2023, and didn’t make any public statements. Presumably there were an uptick of crash logs that pointed to this problem, but didn’t conclusively show attempted exploitation.
The exploits then moves to using NSExpression as a next stage. NSExpression is an ugly way to write code, but it does allow the exploit chain to get to the next stage, running JavaScript as an application, without Just In Time compilation. The JS payload is quite a beast, weighing in at 11,000 lines of obfuscated code. It manages to call native APIs directly from JS, which then sets up a kernel exploit. This is multiple integer overflow flaws that result in essentially arbitrary system memory reads and writes.
We’ve now hit the really interesting part. Arbitrary read and write would normally be game over, but the iOS hardware has built-in mitigations to protect the kernel even from itself. The Kaspersky researchers refer to this as the “final boss” of hacking iOS. First off, keep in mind that there’s more than just ram locations in that system memory map. There are registers, video ram, peripherals, and more. Each of these have defined memory sections. There ends up being memory locations that aren’t used for anything — at least not anything documented. The Triangulation exploit writes seemingly magic values to these memory locations, and it’s suddenly allowed to write memory anywhere, bypassing the “final boss”.
Listening to the Kaspersky researchers, one might think that this is something resembling a backdoor, given that it’s enabled by a secret hash function, and uses undocumented memory locations. Our friend of Asahi Linux fame, [Marcan], AKA [Hector Martin], is something of an expert in reverse-engineering Apple hardware, and has thoughts on this. Namely, it’s debugging interfaces that weren’t intended to be accessible. The secret hash is actually ECC, Error Correction Codes. The Apple silicon has a design quirk, that the GPU section of the chip doesn’t have a dedicated Memory Management Unit, but instead depends on the main CPU to manage that shared memory. These memory locations were never intended to be accessible from CPU code, and probably map to GPU cache, which explains a lot about the behavior of this exploit.
Keep an eye on the Kaspersky blog for more detailed analysis of Operation Triangulation. It’s a fascinating look into work that likely belongs to a three-letter-agency, either from the US or another Western country. And for anyone interested, Kaspersky has released the triangle_check tool to examine an iOS backup for signs of this malware.
As a former NSA guy, watching the community reverse engineer this exploit makes me think of all the people who developed it sitting and crying somewhere as it’s secrets are spilled. https://t.co/HjwAbSPQ8V
— Charlie Miller (@0xcharlie) December 28, 2023
Don’t Trust That Hostname!
SSH has a nifty feature, the jump host. You can specify an intermediary machine to jump through, something like ssh -J jump.host jbennett@final.host. Your local machine can contain rules for specific hosts, to automatically use a jump server to access the remote host. And the problem there is that that’s usually done via the ProxyCommand configuration, which takes the takes the hostname as one of the arguments when building the command to run.
You may be way ahead of us, what happens if that hostname is from an untrusted source, and contains something nasty, like a command inside backticks? Well, until OpenSSH 9.6p1, that command would get passed through to the command line, and gets run.
The last question is, how would an untrusted SSH command get run on a local system? The way suggested by [Vin01] in this disclosure is when cloning a git repository that has a submodule. It might be worth starting a habit of taking a look at the .gitmodules file before doing a recursive clone.
Barracuda Pushes Patches
Barracuda pushed an automatic patch to all the Email Security Gateways it could, last week. There was an active zero-day campaign, attributed to to UNC4841 out of China. Once again, the problem is a vulnerability in part of the virus scanning capability. The Perl module Spreadsheet::ParseExcel is vulnerable to code execution when parsing number format strings.
Bits and Bytes
The relatively popular MajorDoMo home automation has a severe RCE in the thumbnail generation module. A base64 encoded value is directly used to generate a command, making for absolutely trivial compromise. After an initial missed communication attempt, the project’s developers responded and got a patch out within a few days.
You may have seen renewed coverage of the teenager that hacked a Rockstar with nothing but a Firestick and TV — oh, and an Android phone. First, refer to our earlier coverage to cut through the hype. And then we’re genuinely sad to share that the young hacker in question has been turned over to a secure hospital to be institutionalized indefinitely.
And finally, we leave you with the saga of [Tomaž Zaman] working through one of the fundamental freedoms — actually controlling his own hardware. Gigabit Passive Optical Network (GPON) fiber Internet is a bit rough to work with. You can’t just take the provided SFP module and plug it into your own hardware. To find the answer, [Tomaž] rooted the ISP router, found the needed information, and then paid for a specialized GPON SFP adapter that was set up to support this use case. Enjoy!
















Could someone familiar with these SFP sticks explain why they contain a SoC with a full-blown OS and network stack? One would expect that these serve as a simple electrical-to-optical interface…
Sadly a lot of SFP modules are not plug and play, they only work in specific proprietary environments.
Putting an OS with a full network on the SFP is probably the ultimate method to ensure compatibility with almost any device but retain additional proprietary features (that you have to talk UDP/TCP to configure)
As to why there is this culture: I don’t know for certain, but I suspect it’s because the primary market of SFP modules isn’t home users (who expect everything to be compatible) or small business (who learn quickly that proprietary stuff is bad) but instead bigger users that have a culture of contracting groups to do their networking for them (where big & proprietary are tolerable).
As I understand it *normal* SFPs don’t *usually* contain such a SoC but the GPON stuff may be a special case.
We have by law (thankfully) the right to chose our own router – meaning the active *termination* on our xDSL lines (maybe cable too? dunno) can be any router we want to use.
But with GPON (which I’ll hopefully get some time next year) the ISPs are again trying to force the end user to use a device they choose and control (TR-69 I assume).
During a presentation from the company that’s building the GPON network here I asked when I could use a router with integrated fiber or SFP module – the answer was not very specifc, more squirrely… :-/
-> Maybe they’re *developing* GPON SFP’s with their own OS on a SoC inside to retain some control?
Ok, I did some reading, and it seems “GPON” is the key term. (hackaday, hint hint, maybe write an article on this technology, or more generally fiber optic networks?)
GPON is a ISP-friendly technology that utilizes passive splitters to make a one-to-many link between the ISP and multiple subscribers. On the customer’s receive path, the SFP module needs to filter out (and presumably decrypt) only the traffic destined to the customer. The send path uses a complex time-slot allocation scheme to allow the subscribers to share one physical link.
This means that one consumer with non-conforming hardware can disrupt upstream traffic for all others sharing the same link. It’s understandable that ISPs want to avoid such scenarios, although the technology is not capable of preventing this entirely.
It’s my understanding that all of this is somewhat outside the original use envisioned for SFP, that’s why the additional logic is shoehorned into the “plug”.
It wouldn’t surprise me if the custom router and SFP for the GPON connection is so that only an authorized paid-up customer can connect to the GPON network and send/receive data and so that said customer can’t see data belonging to other customers.
NSA requirement in the 1980s was that no software other than their app allowed on hardware platform.
c/c++ industries changed these requirements in ~1991?