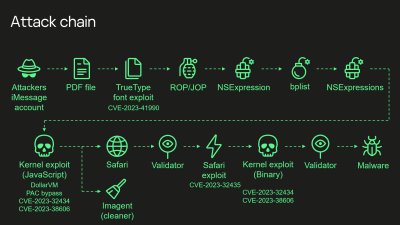
It’s not every day we get to take a good look inside a high-level exploit chain developed by an unnamed APT from the western world. But thanks to some particularly dedicated researchers at Kaspersky, which just happens to be headquartered in Moscow, that’s exactly what we have today. The name Operation Triangulation was picked, based off part of the device fingerprinting code that rendered a yellow triangle on an HTML canvas.
The entire talk is available, given this week at the 37th Chaos Communication Congress, 37c3. The exploit starts with an iMessage attachment, delivered silently, that exploits an undocumented TrueType font instruction. Looking at the source code implies that it was a copy-paste error where a programmer didn’t quite get the logic right for a pointer calculation. That vulnerability gives a memory write primitive that pivots into code execution. What’s particularly interesting is that Apple silently fixed this bug January 2023, and didn’t make any public statements. Presumably there were an uptick of crash logs that pointed to this problem, but didn’t conclusively show attempted exploitation.
The exploits then moves to using NSExpression as a next stage. NSExpression is an ugly way to write code, but it does allow the exploit chain to get to the next stage, running JavaScript as an application, without Just In Time compilation. The JS payload is quite a beast, weighing in at 11,000 lines of obfuscated code. It manages to call native APIs directly from JS, which then sets up a kernel exploit. This is multiple integer overflow flaws that result in essentially arbitrary system memory reads and writes. Continue reading “This Week In Security: Triangulation, ProxyCommand, And Barracuda”