Scoring an interesting bit of old gear on the second-hand market is always a bit of a thrill — right up to the point where you realize the previous owner set some kind of security code on it. Then it becomes a whole big thing to figure out, to the point of blunting the dopamine hit you got from the original purchase.
Fear not, though, because there’s dopamine aplenty if you can copy what [Buy it Fix it] did to decode the PIN on a used generator control panel. The panel appears to be from a marine generator, and while it powered up fine, the menu used to change the generator’s configuration options is locked by a four-digit PIN. The manufacturer will reset it, but that requires sending it back and paying a fee, probably considerable given the industrial nature of the gear.
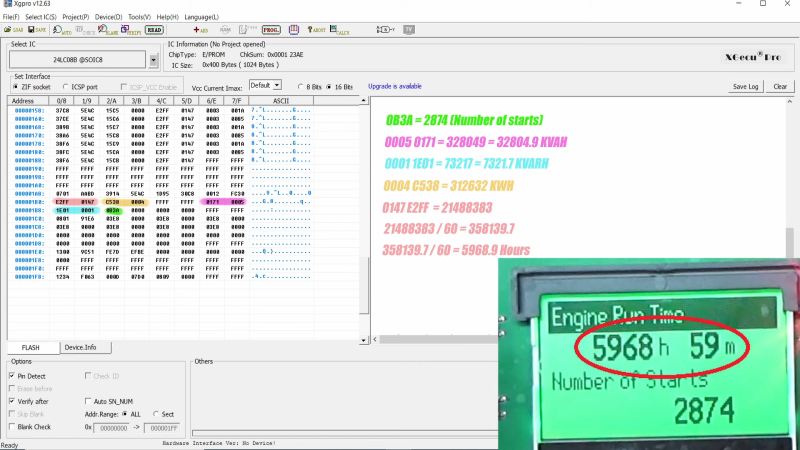
Instead of paying up, [Buy it Fix it] decided to look for a memory chip that might store the PIN. He identified a likely suspect, a 24LC08B 8-Kb serial EEPROM, and popped it off to read its contents. Nothing was immediately obvious, but blanking the chip and reinstalling it cleared the PIN, so he at least knew it was stored on the chip. Many rounds of soldering and desoldering the chip followed, blanking out small sections of memory each time until the PIN was located. The video below edits out a lot of the rework, but gives the overall gist of the hack.
To be honest, we’re not sure if the amount of work [Buy it Fix it] put into this was less than taking a couple of hours to punch in PINs and brute-force it. Then again, if he hadn’t done the reverse engineering he wouldn’t have stumbled upon where the generator parameters like running time and power figures were stored. And it’s not really his style, either; we’ve seen him perform similar heroics on everything from tractors to solar inverters, after all.















This is a neat write up.
The panel is an older unit made by Deep Sea Electronics in the UK (pre-2012, by the looks of it). They’re incredibly helpful when I’ve had tech support questions on some units I own.
This issue aside; they’re one of the Good Guys of modern hardware.
It would’ve taken a lot longer to brute force it than what he did. This was a nice glimpse at how things are stored in EEPROM on various devices. Working out where the metrics were stored on the EEPROM was a nice ,interesting little extra.
He did another good one not so long ago, also featured on HAD, where he pulled his tractor control panel to pieces, dumped the EEPROM and sent the contents to a guy in Australia so he could get his own tractor fixed.
These things may seem quite simple to some people but they are the prime definition of a “hack”. Kudos to BuyItFixIt. I know I certainly learnt a few things from that video, and others on his channel.
If the button contacts are easily accessible, the brute forcing could be automated using a cheap USB relay board. With about 10 seconds per PIN using that slow input method, it would take about 30 hours.
But he didn’t brute force it. He did a binary diff of two different EEPROM dumps to locate the code.
Admittedly, the first time he wiped the EEPROM completely and managed to wipe the code that way, but that would’ve permanently knackered any calibration settings that were stored.
This is how I expected it to go. But I believe it would be easier said than done. How to detect success? Webcam + open CV? Yuck…
just get it to run half the codes and come and have a look, then either run the other half, or divide the codes window by 2 and repeat it 3 times.
sorry, repeat about 10 times, to give you a possible 9 numbers to try manually.
I swear that HaD is monitoring ever every article / video that I read / watch, because it always shows up here a day or two later!
Was just about to post the same sentiment.
Although for the life of me, I still can’t figure out why Youtube thinks I’m also interested in model railways, Australian drain unblocking and Phil Collins and continually recommends them no matter how many times I click on the ‘not interested’ thingy.
Search for enshittification
Well, now I know I’m not the only one who gets the Australian drain-unblocking guy now. It’s like it profiles HaD readers into a specific content set.