[Georges Gagnerot] has been trying to emulate iOS and run iPhone software in a virtual environment. There were a few choices, and qemu-t8030 had a number of interesting features that you can check out in his post.
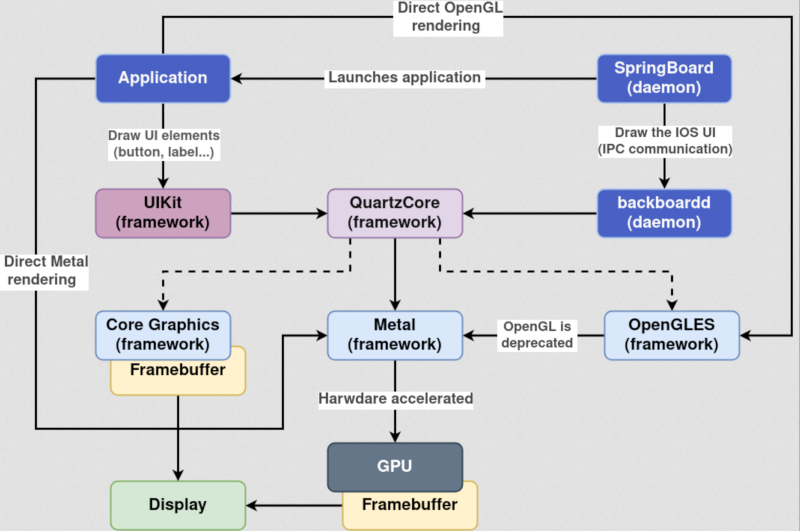
The project requires a patched QEMU, and [Georges] did some basic jailbreaking techniques. The real problem, of course, was not having the Apple Silicon GPU. Older versions of iOS let you select software rendering, but that option is gone on newer versions. However, it was possible to patch the phone to still use software rendering. There are still apps that directly use Metal or OpenGL that won’t run, but that’s another problem.
There is a plan to explore forwarding GPU calls to a real device. However, that seems difficult so it will have to wait for now.
That wasn’t the last problem, of course. But the post gives you a great view into the detective work. There is still work to go, but it looks like a lot of progress.
You can find the t8030 code on GitHub. Most of the iPhone hacking we see is hardware even if it means cutting the screen.















This is some next level commitment and crazynes!
Hats off.
It seemed peculiar to me as well but then I looked at the site it’s posted on and it makes sense now because they are part of a security firm. Their job is to investigate iPhone security, which includes system software, so it make sense to go to the greatest of lengths to simply “make it work” even if that means patching binaries.
With Asahi Linux having drivers for Apple GPU, it might be possible to use the information to create Apple GPU emulation.
I was studying iPhone security features like brute-force protection by wiping itself after a given number of attempts, and realised that it could be thwarted by disk snapshots and rollbacks. But I don’t know if iOS has something to detect virtualisation, or if virtualisation even exists for it. I knew that enough emulation exists to test apps in x-code, but I don’t know if that’s low-level enough to run an image taken from a real device, nor do I think it’d be built for that.
I imagine some three letter agencies (NSA et al.) may already have an emulator so they can brute-force PINs of disk images taken from iPhones. Then again, they maybe don’t need an emulator if they have access to enough hardware/software backdoors. Nor would I put rubber-hosing past them.