I just realized that we’d never covered the classic amateur radio antenna hack – known as the mobile electric screwdriver antenna. I was looking for a decent writeup, and ran across this interesting tunable indoor antenna. [W2BRI] put together a 5 foot cube loop antenna built from copper pipe. The tuning mechanism uses an electric screwdriver to tune his giant PC Board tuning capacitor. Looks like a nice solution if you’re into radio and have pesky neighbors.
Misc Hacks4193 Articles
Mega8 Logic Tester
[Ast] sent in his time sampling logic analyser (in German, so use the fish) based on a Atmel Mega8 and a FT232 USB interface and several logic chips. It can store time captures in memory, then upload them to a PC via USB. Looks like a great tool for advanced logic testing.
Silvia PIC Controlled PID Looped Espresso Machine

Last night I rebuilt my ECM Giotto with a new boiler. I’ve seen PID controlled machines before, but today I stumbled across this modded Rancillo Silvia. [Tim] replaced the internal brain with a PIC controller, added a NES control pad for input, a VFD display and a custom laser cut acrylic top. He used the PIC to provide PID control and PWM heater control with the usual solid state relays. I was leaning towards using a PIC for PID control myself, but then I scored my Giotto. (The heat exchanger and larger boiler makes it a bit of a moot point, but I’m still tempted to add PID boiler controls.)
A123 LiIon Battery Pseudo Extra

Every so often I have to slap myself in the head. I’m surprised that we haven’t covered these things by now. DeWalt’s been selling a LiIon 36 volt battery pack that’s full of the latest A123 cells. These are the same ones that were used in the Killacycle. (I think they’ve got a new batch of cells now).
A while back, [Jeff] sent in a circuit for using multiple packs, leaving the internal BMS in place. [The link is fixed now]
[Robert] sent in a scooter that’s been designed to run these same cells. The custom fabrication and machine work looks fantastic.
O-Scope Pong

[Dylan] sent in this amusing use for an O-Scope. The entire thing was implemented using six chips – four logic chips, 2 op-amps and 13 pots. Hit the video after the break or check out the project page.
NSA@home (DIY Shared FPGA Cracker)

[Skylark] converted a pair of defective HDTV processing boards into his very own FPGA SHA-1 hash cracker. After two months of evening work, he ended up with 15 Virtex-II Pro FPGAs and 5 Spartan-II FPGAs to do his bidding. (FPGA’s aren’t cheap, so this rocks) Eventually he’s going to give it a web interface to allow cracking submissions on request. Great find on the boards and fantastic work [Skylark].
UClinux Based Embedded Asterix PBX
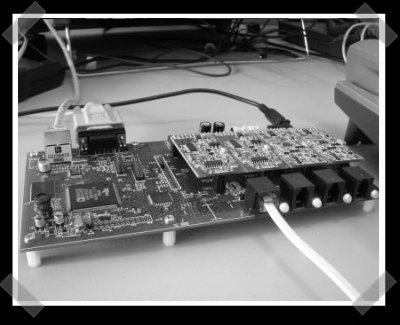
In my quest for a new VOIP setup (I’m hunting for a new sip provider – got suggestions?) I ran across an excellent project that’s been put together by [David]. It’s a four port open source asterix PBX that runs under UClinux. He derived the design from a BlackfinOne (A dedicated UClinux board). He covers building the IPO4 in four parts series that starts here. It’s probably one of the more intense open source hardware derived projects I’ve run across.










