GitHub is an incredibly powerful tool for sharing source code, and its value to the modern hacker can’t be overstated. But there’s at least one downside to effortlessly sharing your source: it’s now much easier for the whole world to find out when you screw up. Back in the day, if you accidentally left a username or password in a tarball hosted on your site, you could pull it down before anyone noticed. But push something like that up to GitHub, and you’ve got a problem on your hands.
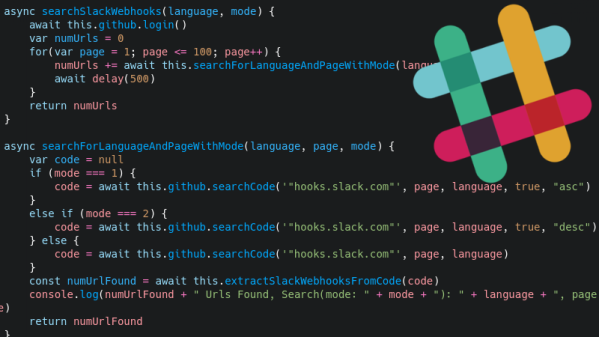
For an example, look no farther than this tool that crawls GitHub for Slack webhooks written by [Michele Gruppioni]. Exploiting the fact that Slack webhook links have a predictable format, the tool searches repositories to find code that erroneously includes the authentication token. With the token in hand, an attacker now has the ability to send unsolicited messages into that channel.
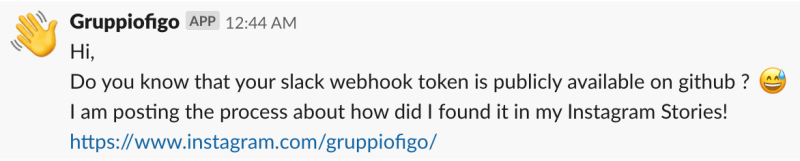
But [Michele] restrained himself and didn’t Rickroll the over 6,500 Slack channels he had access to after searching GitHub with his tool. Instead, he sent them all a friendly message explaining their webhook tokens were available on GitHub, and gave them a link to where they could get more information about his project.
Most of the people who contacted him after the fact appreciated that he sent a gentle warning and not something unsavory. Still, we’d recommend caution to anyone looking to expose a vulnerability in this manner. While [Michele] had honorable intentions, it’s certainly not unheard of for an embarrassed administrator to blame the messenger.
When used properly, webhooks can be a very handy way of pushing data into your chat platform of choice. We’ve previously looked at a practical example of a weather station that pushes current conditions into a Discord channel. Just try not to accidentally commit your authentication token to the world’s largest database of open source projects, or you might receive more than you bargained for.