[Thice] discovered a vulnerability in encrypted portable storage a few years ago. He’s just pointing about the exploit now. He mentions that he notified manufacturers long ago and we’d guess the wait to publish is to give them a chance to patch the exploit.
He calls it the Plug-Over Attack and for those who were involved with original Xbox hacking, this technique will sound very familiar. The Xbox used hard drive keys to lock the device when not in use. When you booted up the console it checked the hardware signature to make sure it was talking to the right motherboard. But if you booted up the device, then swapped the IDE cable over to a computer without cutting the power you could access the drive without having the password.
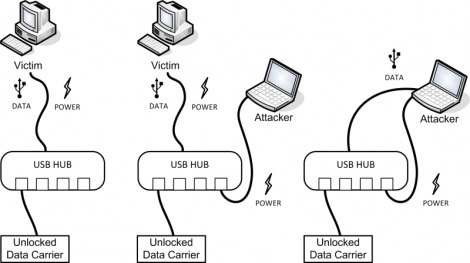
This attack is pretty much the same thing. Plug in a drive, unlock it on the victim system the normal way, then replug into the attacking system. In the image above you can see that a USB hub will work for this, but you can also use a hacked USB cable that patches a second jack into the power rail. For some reason the encryption system isn’t able to lock itself when the USB enumerates on the new system, only when power is cycled. Some of them have a timer which watches for drive idle but that still doesn’t protect from this exploit.










