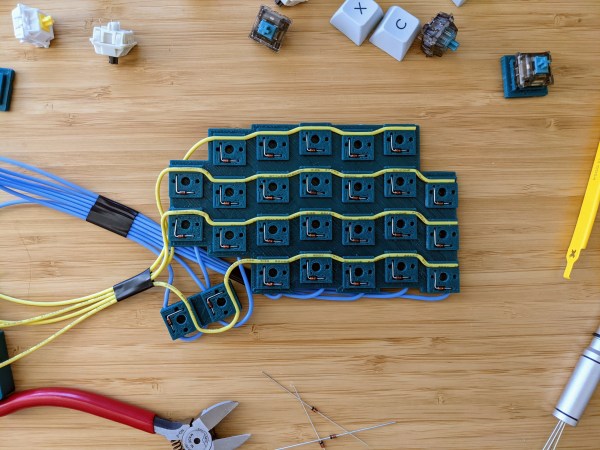
Maybe we’re biased, but we think everyone has a use for a macropad. It’s just a matter of time before a highly personalized set of speed controls starts to sound like a great time-saving device to have around.
 Trouble is, macropads are usually kind of expensive to buy outright, and not everyone feels comfortable building keyboards. Okay, so what if you didn’t even have to solder anything? That’s the idea behind [Jan Lunge]’s hand-wired macropad.
Trouble is, macropads are usually kind of expensive to buy outright, and not everyone feels comfortable building keyboards. Okay, so what if you didn’t even have to solder anything? That’s the idea behind [Jan Lunge]’s hand-wired macropad.
You will still want to open a window for ventilation if you build this one, because this macropad requires a lot of 3D printing. What it doesn’t require is glue or screws, because everything snaps together.
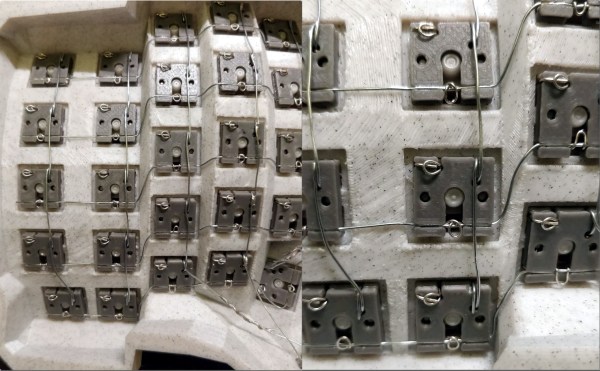
Of course, the star of this build is [Jan]’s hot swap socket design. We especially love the little clip that holds the column wires in place while also providing a spacer between those and the row wires. Everything is connected up to a Pro Micro with non-insulated wire and held in place with bends at the ends and the magic of tension. Be sure to check out the build video after the break.
Thirsty for more than a six pack of switches? This design is easy to scale up until you run out of microcontroller inputs. At that point, you might want to add screens to keep track of all your macros.
Continue reading “Snap-Together Macropad Does It Without Solder”