The WiFi adapter in your laptop has a special mode – monitor mode – that can be used to listen in on WiFi traffic and, with a little patience, can be used to crack a WEP password. Surprisingly, this monitor mode can’t be found on any Android device due in part to the limitations of the hardware. A group of three researchers, [Ruby], [Yuval], and [Omri], decided to spend their vacation adding monitor mode to their Android smartphones, allowing for a much more portable version of WiFi pwnage tools.
The phones used by the researchers – the Nexus One and Galaxy S II – used Broadcom chipsets that didn’t support monitor mode. To get around this limitation and allow the OS to see full 802.11 frames the team needed to reverse engineer the firmware of this Broadcom radio chip.
The team has released a firmware update for the bcm4329 and bcm4330 chipsets found in the Nexus One and Galaxy S II. The update may work for other phones with the same chipset, but don’t take our word on that.
There’s still a lot of work [Ruby], [Yuval], and [Omri] need to do. They’d like to add packet injection to their firmware hack, and of course create an APK to get this into the wild more easily.
If you have experience with kernel development and would like to help out, send the team an email. The source can be found at google code if you’d like to play around with it.

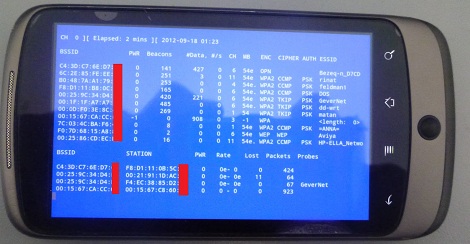














The first link is incorrect. Please fix it!
I can stand the “occasional” misspelling, but the first link–really?
Oh wow. Fixed now.
Embarrassing and slightly hilarious.
Yeah, that’s…interesting. I think this is the page it’s supposed to link to: http://bcmon.blogspot.com/
Nice project. Very useful!
Well you’d actually want it to link to
http://bcmon.blogspot.com/2012/09/working-monitor-mode-on-nexus-one.html
So that if they end up posting other random stuff on that blog, you still get a link to the appropriate article.
I was like XD
Then they said no packet injection and I was like
-_- uh…. Yeah I’m not going to use this.
I’ll keep an eye out for the update though
Awesome! I’ve been waiting for this forever. So much easier that waiting for my friends to try and remember where they keep that slip of paper with their dumb password on it.
I’m glad to see this isn’t just an aircrack port like that shitty iOS version where you need to capture on a laptop then use the iOS to analyse (totally lame).
Can I use it? I have bcm432x. Is it a kind of bcm4329?
[48028.238084] =========== WLAN going back to live ========
[48028.238701] bcm432x_sdcc_wlan_slot_status: 93 1
[48029.126377] wlan0: Broadcom Dongle Host Driver mac=5c:xx:xx:xx:xx:xx
[48040.612794] wlan0: no IPv6 routers present
Good luck cracking my password I use all 64 characters and change it every 2 weeks. And that is not my only defense.
In my neighborhood THere are so many wifi networks it is not funny. With just the pitiful antenna in my laptop I can pick up 15 nets and 90% of them are on cannel 11 . I use the 5ghz and have no problems. I am thinking of making a 1W 2.462ghz beacon to clear the congestion.
If you’re so security-conscious, why are you using WEP instead of WPA (serious question, my understanding is that WEP is deprecated due to vulnerabilities that can be easily accessed on simple (e.g., cellphone) hardware).
Maybe if you’re going to brag about violating FCC law and in general being a jerk (if you’re in the 5Ghz A/N band, why do you care who’s using 802.11b?), you shouldn’t do so with your ham license as your sig,
–EDITED– do not post other people’s personal information. even if they are being jerks. —
lolasaurus-rex
Wowzers… now that’s a burn.
This = win.
Wow, I don’t use this word often, but you deserve it:
EPIC slapdown!
ouch.
The beauty of FCC’s open license records search. I now know more about that guy then I ever cared about.
@S: Yeah, valiant! Steal my nick to be a jerk with jerks, it’s easy in had. :(
Good luck, Im behind 64 characters!
1W CW or noise jammer on wifi channel has very limited jamming range. Think 20m.
The ‘problem’ is that wifi detects if the channel is free by using energy detect (which you trigger with your jammer, but the threshold is quite high), wifi mostly relies on false carrier detect. A preamble is transmit before every wifi frame containing information about the following transmission (speed, modulation method, etc, it is always transmit at 1mbit/s btw).
When the card can receive such a frame, it assumes the channel busy for the duration specified in a frame.
Thus a jammer spamming these pre-headers (google PLCP header) would have a jamming range equal to its reception range, while still being invisible to 802.11 sniffers.
This is a by far more dangerous attack against Wifi as for example a 1W jammer connected to a proper antenna would jam in a circle of more than 500m. Completely blocking the communication (as the cards voluntarily stop communicating since they think the channel is busy!) while being undetectable to trained ‘cisco enterprise wifi specialists’ and such. Detection with a spectrum analyser is obviously possible, but at least the signals looks like a legit wifi signal so it isn’t as obvious as broadcasting noise.
Another more stealthy approach is to estimate the transfer function from you to the access point (which you can do, since it periodically broadcasts beacons and data). Simply interpolate the phase and amplitude of the pilot tones using fft interpolation. Since the access point and jammer don’t move the transfer function changes only a little due to the environment changing (which LMS will track without problems). Using a tracking filter such as LMS is optional, it will improve the transfer function estimate while the jammer is operating, making it work better against distant stations.
Now whenever your jammer hears a packet from a client, it calculates the transfer function client->jammer in the same way as with the access point. Again a tracking filter may be used for better performance in bad SNR situations.
The next step is calculating the inverse of the pilot tones sent by the client and transforming them with the inverse of the jammer->ap transfer fuction and the client->jammer TF. This will result in the AP receiving the OFDM frame with the pilot tones being zero, making demodulation impossible. You only transmit a very short time during the transmission of the client, just enough to corrupt the packet and you do so in an optimal way. This approach easily gets 15-20dB (especially against single antenna routers and clients) of processing gain. Rhis is because the pilot tones are used for equalising the channel, if the signal on these few frequencies is damaged, the other frequencies cannot be used. You do not even have to make the pilot tones zero, it is enough to make the demodulator channel estimation fail, you can remotely observe the amount of packets dropped and adjust your signal.
You need a very fast digital spectrum analyser to see the extremely short jamming bursts (in a band already crowded with burst type signals), since your transmit signal only uses the theoretical least amount of power necessary to jam the current transmission (you will transmit less for a distant client, since you have actually estimated the channel between client and AP)
You best leave beacons alone as not doing so will make the list of received networks empty and then the jamming is obvious. Also they are broadcast traffic so your jamming will be less optimal since the final signal will be a compromise made by combining a jamming signal for every AP->client TF.
I think this type of jamming in a commercial environment would take a very long time to be found and taken care of.
BTW: When looking at a channel estimation of a wifi channel and the access point is moved (or someone moves nearby), the changes are quite large. You could stop jamming for a random time after the access point has been ‘tampered’ with to make it just seem like bad reception that was fixed by moving the router a little bit.
Hey dojo; ur comments on the wifi cracking post sound like u kno ur junk! Any other adv I ce for us novices? How about step one; for the beginner; and laymans terms?
Then we’ll just have to crack that password every two weeks.
If 90% of them are on Channel 11, that’s easy to work around :-) Go find a quieter channel. If your equipment will all do Channel 13 or 14 it’s usually pretty quiet over there. Otherwise, stick to the US channels, and use a signal strength monitor to find whether 1 or 6 has less total energy on it (which is different from “number of networks”, because distances also matter. I’ve had good luck with Android apps for signal strength.)
Also, what’s your threat model for the security key? Other people have pointed out that WEP is useless if crackers actually want to get in and you should use WPA2, but do you care more about preventing unwanted guest users, or about eavesdropping on your connections? They’re independent problems – I’m fine having “guest” as the password for authentication, and if one of my neighbors wants to leech off my internet connection occasionally, that’s not a problem.
You might want to change your username, dude. Using your callsign as your username means your full name and address are literally a google search away.
By the way, how’s the weather down there in Dixie?
Also. . . he uses a mac. Hahaha and not a really good one.
What exactly is 90% of 15? How are there 13.5 networks on channel 11 in your neighborhood? U counting at&t DSL service as half a network or something? JW
ONG burned so hard!!!!!!
Why not just connect wifi USB dongle to the phone? they all have usb hosts now.
No drivers maybe. Also some USB network cards need lots of mAh, and a phone’s USB won’t be able to supply that much. (I think)
nah, drivers are arch agnostic (realteks,ralinks etc)
Great! The one thing I could do with my Nokia N900 3 years ago that I haven’t been able to replicate on the GSII. Looking forward to its completion…
I just bought a N900, it’s amazingly open. Nokia has a web-page explaining how to enable root access, the aircrack-ng ARM Debian package is in the default app-manager. (and for everything else, the gnu C complier runs fine on the phone itself)
For anyone wondering which other phones use those chips, the Galaxy Nexus uses the bcm4330 :) http://www.techrepublic.com has a few GREAT teardowns of different phones where they usually investigate every chip on the board
I am secure enough that I don’t have to hide.
And anyone that has tried to test me has failed.
You crazy.
n900 guys n900!!
but that’s old caveman tech we have androids now :( sure it works (but I just can’t stand using the resistive touchscreen)
Yep. And it does it far better. Walsh/reaver/WPA bruteforce. Then you’ve got tools like ssl strip and YAMAS. N900 is still miles ahead of droid :P
Yes, Maemo is a tiny bit more advanced than Android for network penetration-testing. For about another month.
By simply installing Complete Linux Installer (an Android app from the Play Store), one can grab Backtrack on any rooted device that supports a loop filesystem in the kernel (most ROMs do, including AOKP). Thus, wash, Reaver Pro, reaver-wps, aircrack-gui-m4, sslstrip, and many other tools are instantly available.
Note that is also possible to run wash on a pcap file, so in theory even iOS supports detection of active WPS on reachable APs.
Because Android is Linux, I find it silly to argue about this, but I do like the N900 and Maemo, especially the Cleven project. Perhaps a similar app can be ported to Android?
Doesn’t every modern phone have USB drive capability built into it by now? :-) (Well, anybody who’s following the micro-USB power cord standard, anyway.)
Sweet, more drivers. The G1 and G1 can do monitor and packet injection with the WL1251 chipset (same as the N900) but the Nexus One and the SII are much faster. I hope more stuff like this happens.
*G1 and G2
Is that going to require custom ROMs to be installed or is it going to work fine with official firmware, too?
what about phones using qualcomm atheros chipsets since those usually have monitor mode in there pcie/usb chipsets.
thx men
how do you install that cm build? what commands are used? (sorry for asking but i’m a noob), how well does it work? and is an apk out?
Hi, this is my first time here and I love the thread, and even more love the site. I wanted to ask a purely noob question, so please don’t call me a moron, lol.
I just wanted to know if the Samsung galaxy s2 must be rooted in order to bypass security on a WEP router signal.
Not doing anything illegal, just sick of crappy 4g connection out here on the acreage and my parents won’t let me use their wifi.
They think I’ll use up their data on a phone! So you see what I have to deal with?
The only reason I don’t want to root my phone is because I have no experience and I don’t want to crash the OS or anything like that.
Any ideas?
Real ?
Samsung galaxy tab 2 7.0 p3100 can use?
my phone wifi is connect but want to see my wifi password how its possible
Is not supported by the Galaxy S3 is it? cant make it work, getting error….
can made the aditional device using through usb or data cable?
You can easily hack into computers with this new and advanced app for android, just watch the video to find out how to get it.
https://www.youtube.com/watch?v=BCBzkcqaCN4
Hello everyone stop searching for wifi hacker because i have got it. I had bought a wifi hacker from famous hacking team with $100 secretly and now i am easily hacking wifi near my house in less than 2 min. The cost of this software is very high. But,you don’t need to be worry,i am providing you absolutely free. Just download it from below link and start hacking your neighbour wifi very easily.
http://bit.ly/1e12hyB
Enjoy!!!
Only a nearby-network of your Mobile it is able to crack
fake and fuck it its not working wastage of mobile data nonuse don’t use this it blackmail to u
Hacker wifi
Is this still in the works?, im sure by now it would have spread to more devices, I have a Sprint HTC M8 HK edition please let me know. Thank you.
Stop spreading bullshit …try this method!
NOTE : YOUR DEVICE MUST BE ROOTED AND ANDROID VERSION MUST BE 4.2+.
1. In play store Search WPS Connect and install it.
2. Open it GRANT SUPER USER ACCESS and hit refresh button at top and AP’s will be listed.
3. Click one AP name and something opens up hit try pin and voila youre done.
NOTE : IT MAY OR MAY NOT WORK ON ALL AP. THE ONES WITH WPS ON AND WITH GREAT SIGNAL STRENGTH WILL WORK.
HAVE FUN!
Plz I need source code of it