In a slight twist on the august pursuit of warwalking, [Mehdi] took a Raspberry Pi armed with a GPS, WiFi, and a Bluetooth sniffer around Bordeaux with him for six months and logged all the data he could find. The result isn’t entirely surprising, but it’s still a little bit creepy.
If your WiFi sends out probe requests for its home access points, [Mehdi] logged it. If your Bluetooth devices leak information about what they are, [Mehdi] logged it. In the end, he got nearly 30,000 WiFis logged, including 120,000 probes. Each reading is timestamped and geolocated, and [Mehdi] presents a few of the results from querying the resulting database.
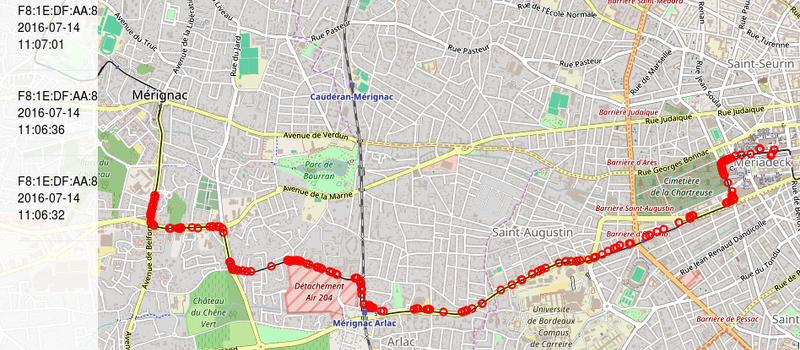
For instance, one person who shared a train commute with [Mehdi] got on at Meriadek and got off at Lycee Dagin on July 14th, and was never seen again. Another fellow train rider’s WiFi sent out probes for a Dominos pizza WiFi BSSID. [Mehdi] points out that you could even figure out which riders knew each other because they often connect to devices with unique IDs, which could be used to correlate them.
Now, all of this is actually more telling about [Mehdi] than anyone else he meets. You can easily tell which train lines he rides and when. But if there were a network of these sniffers scattered around the city, especially if they were made cheaper out of something like an ESP8266 or a used cell phone, one could play NSA on a human-scale budget. (Local laws allowing.)
Is this horrible, creepy, illegal, or yesterday’s news? Hash it out in the comments!
















Isn’t this basically what Google does with Android location services? With every Android phone everywhere (which has it enabled of course)?
The point of this is that you can track individuals without having to plant special hardware on them or software in their phone. You can even use this to prove associations between people. And it can be easily done by, say, government agencies without needing any special privileges from Apple or Google.
Well, that is what cellular base station triangulation is used for. In cities where the network is dense it could be accurate down to tens of meters and all the police/spooks/etc need to do is to serve a warrant to the network operator (unless they have a pre-established “backdoor” already, then they don’t even need to bother with that).
The stuff from the article is more about data mining, what you can recover from correlating data we are constantly leaking like sieves, not tracking individuals by state actors. For that simpler solutions exists that do no require deploying extra infrastructure.
I smell an ESP32 project a brewing!!!
LOL
DNS evasion and wifi localization based on this same project:
https://github.com/mehdilauters/esp8266-wifiScanMap
Well, IF I were that person on the subway I would never know or imagine someone was logging my wifi/bluetooth. And I would never care, because I have bought an Android phone, logged in @ google play AND CLICKED “I AM AWARE YOU ARE USING MY DATA AND I AGREE WITH IT”, otherwise I would have never been allowed to even have a funcional cellphone at all.
I mean: me and you are just another number, right?
“otherwise I would have never been allowed to even have a funcional cellphone at all.”
And yet my Nexus 6 with Cyanogenmod and zero Google apps (no Play store, no Play services, etc.) functions even better than it did when it had stock Nougat installed. I get twice the battery life, more security granularity and truly private browsing, complete control over the phone OS since it’s rooted, all the apps I used before are available or have as-good-or-better equivalents, and Google has zero knowledge of or control over the device.
And you are still susceptible to tracking as anyone else by the virtue of your phone logging into the cell network which can trivially triangulate your position. You are only feeling safer, even though you are not really.
All that your Cyanogen will do is that your data won’t be sent to Google. Oh and are you sure that none of your apps is “phoning home” regularly? Most “free” apps do.
So get off your high horse …
I work for a major wireless provider and that’s all I do is look at signals between towers and devices. True some locations can be done accuratly, however terrain can play a roll, as does the type of tower. Omni directional towers will only give a general distance from the tower and cannot pinpoint location only a radius say 5 miles out from the tower but could be any direction. Even with directional towers accuracy is not always there, if the device goes into a building that degrades the signal the network has no way of knowing this and it will often though the distance mapped by several miles. Cellular location is only good in perfect scenarios. The farther you are from a tower the worse it gets.
Maybe with older non smart phones, but with today’s smart phones they actually do send wireless signal levels back through the enode b (base station) to the MME (mobile management entity).
Better is better than worse. “”Perfect is the enemy of the good”. And so on.
Re-read my post: When did I mention tracking by cell towers, or tracking at all for that matter? Cell tower tracking is a given, even with a dollar store flip phone. My point was that you can have a functional smartphone without being tied to Google, as a counterpoint to [Clovis Fritzen]’s assertion that you cannot.
Perhaps you should measure your own steed.
Don’t you love when the troll’s change the narrative to match their own agenda, [kaidenshi]? They grab the one thing and run with it without even understanding why you posted the comment. Then you have this guy [RF Engineer] who has completely forgotten that there is GPS in smartphones and with e911, your location can be discerned. What about triangulation? “Perfect scenarios” …. WOW he must live in the 60’s before all this tech stuff came out.
I digress [kaidenshi], seems all these comments have lost sight of why you posted about Cyanogen. (as a response from a clueless smartphone user.)
Oh yes, because Cyanogen IS VERY SAFE AND PRIVATE with its super user root access. right
It can be made safer and more private than stock Android because the user has full root access, yes. But hey, if you don’t trust the CM team (and who knows, maybe you shouldn’t), you can always grab the source and roll your own AOSP image. You’re still not going to have 100% control over the device since that’s impossible with any technology you don’t build yourself from the board up, but it’s a damn sight better than trusting Google.
And if you’re truly paranoid, you can eschew phones altogether and carry an old-school receive only pager, and call folks back from a landline. The rabbit hole goes as deep as you want it to.
Well they licenced android for the device so they’ll know the mac address, making this type of data harvesting possible (and not anonymous).
But then again, as you’re rooted you could just install Pry-Fi
“…I would never care, because I have bought an Android phone, logged in @ google play AND CLICKED ‘I AM AWARE YOU ARE USING MY DATA AND I AGREE WITH IT’”
Which most people ignorantly don’t realize how this allows tracking or simply don’t care.
The point of this method is, however, from the article and a comment above:
“one could play NSA on a human-scale budget” AND/OR “it can be easily done by, say, government agencies without needing any special privileges from Apple or Google.”
Imagine if delivery drones had this built into them so that they were constantly mapping an entire city on behalf of the drone operators, or a third part paying for the data. What if they disguised it as simple a navigation aid for the drone in case of GPS problems?
Google used to log that wi-fi data with their street-view recording cars, but I think that they got sued…
Yes, but if they had just passed it on to other people and not stored it?
They were sued for grabbing network traffic along with the SSIDs and MAC addresses.
They got sued and nothing happened to them, because they said “oops, it was a bug”, I wonder if that excuse would work for Volkswagen or any other industry.
The fact is that Google, Apple, and many internet or software companies always get away with saying “it’s a bug”, even if they don’t even fix it (like the many Android vulnerabilities that nobody cares to fix…)
Imagine Google doing this years ago.
Randomize the MAC for each scan and much of the tracking would be impaired.
Only for devices that use the broadcast probe.
iOS 8 apparently randomizes the MACs when certain conditions are met, but they aren’t met very often (sleep screen, wifi on but location services off, etc) by the average user.
If you track the SSID probes (still the android default AFAIK) and different MACs are screaming out the same dozen SSIDs it would be trivial to correlate those. If it’s not the same person almost certainly share intimate details.
Why do you think, that the conditions are not met very often? I normally have WIFI on and locations off (I switch location on only if I really need it). But I do not use Apple devices.
Because the average smart phone user doesn’t go around reading tech and security blogs. People want convenience, getting to work or a coffee shop 2 minutes faster is worth leaving location services turned on. They don’t see the cost in privacy, or see why they should care about their wifi SSID privacy.
And then there’s articles like this one:
http://www.geomarketing.com/overwhelming-number-of-smartphone-users-keep-location-services-open
Android does randomization of Wi-fi Mac Addresses since 6.0 and iOS since 8.0.
A false sense of security. I’m sure changing the MAC frequently does a little bit of good, but not when facing a surveillance minded adversary.
True.
Some security folk advise turning off WiFi except when you need it – i.e. only have it on at home and work and rarely otherwise. It takes a couple of seconds to turn it off and a little more to turn it on and connect. I’ve gotten into the habit some time ago… I just don’t want to advertize my WiFi presence, MAC address swapping notwithstanding.
Apparently Android 6.0 does this according to their change list
https://developer.android.com/about/versions/marshmallow/android-6.0-changes.html#behavior-hardware-id
AFAIK , some devices do randomize the MAC when they send probe requests, an interesting read here : http://blog.mojonetworks.com/ios8-mac-randomization-analyzed/
[Brendan O’Connor] Did approximately this on a slightly larger scale and presented at Defcon 21
https://www.youtube.com/watch?v=ubjuWqUE9wQ
I was about to post this :)
Newsflash for you. It’s already being done on a widespread basis by certain unnamed governmental agency.
Done months ago – ESP8266 +GPS + SD
http://euerdesign.de/2016/04/16/wigpsfi-esp8266-gps/
Heh… youse guys are funny…. there’s not a thing you can do unless a few thousand of us pledge our budgets to this cause.
Sit back… watch the blinkin’ lights….
Capturing the probe is yesterday news. It’s done around the globe at universities (I know that there were at least 2 thesis based on it done on my eastern european polytechnic).
Mozilla Stumbler (https://www.mozilla.org/en-US/contribute/task/stumbler/) is an open source Android app that collects Wifi and cell tower information for MLS (mozilla location service). Please install and contribute.
You are quite a simpleton if you advertise something under an article that is exposing all the tracking possible as scary and overly intrusive.
And I think we all know about Mozilla and its two-faced approach to the world, on the one hand constantly announcing you need privacy and on the other hand constantly adding more tracking with unique ID to all their stuff.
At least one tracking/spying/privacy-issue i don’t have to worry about – no wifi, no bluetooth, no smartphone. :-)
Still a damn pity though that they ruined that tech with all their spying and tracking, conceptually it’s nice to have a powerful portable mini computer like that with wireless stuff and the ability to place calls. But the motherfuckers ruined it all.
This scanner is OK if you’re concerned about weight but very weak. You get much better scans with high gain antennas to cover more area and multiple USB wifi interfaces to support simultaneous channels; it still fits in a bag and wouldn’t look out of place on a train. I’ve been able to run 4 interfaces on an rpi3 with good resutls. I added some voice capabilities so it reads out the stats because the hardware and OS can be flakey; if it goes silent or the interfaces get stuck, that’s how you know it needs a reboot.
Of course, you can also do a lot of deauthing with that setup :)
Try pyLCI if you have accessibility problems, it’s a neat interface that allows you to see, reboot and control all kinds of things. It’s quite suitable for stuck interfaces, controlling your scripts etc.
Definitely creepy. So many people don’t know how much information is sent out from their device. They assume that because it has a password it’s safe. Another reason internet of things could be bad. Someone could know all of your habits based on information sent out from devices if it’s not secure.
Security has nothing to do with it. It’s built into the design of the protocol.
Some security is being put around the latest mobile phone devices but they still need to communicate over the air to function, and that can be used to track anyone.
Old News really.
I’ve got a project running at the moment where I can spend 2 minutes within 5 meters of a person and over a period of a small number of days, locate that person’s residential address.
Obviously this is only going to be truly effective against people who live in the monitored area (I’m not going to be able to work out where someone lives if they’re interstate), but the concept is there and has been used as method of Intel collection for over a decade.
This is already in place in many cities and stores. Here is one of many example providers: http://www.bumbeelabs.com/
Here’s another ESP8266 based tracker – http://www.phreakmonkey.com/2016/08/towl-telemetry-over-opportunistic-wifi.html
Would some of the creepiness go away if you monitor for probe requests at a fixed location, say, your house? It might be handy to have data available after an event (say, a burglary or vandalism) that shows which MAC addresses were in range in the event’s time span.
…and here is such a setup: http://www.lanmaster53.com/2014/10/wifi-user-detection-system/
… you don’t need to be paranoid at all to use such tools. Think about a homeless person, which have to give up his phone – could happen faster as you think.