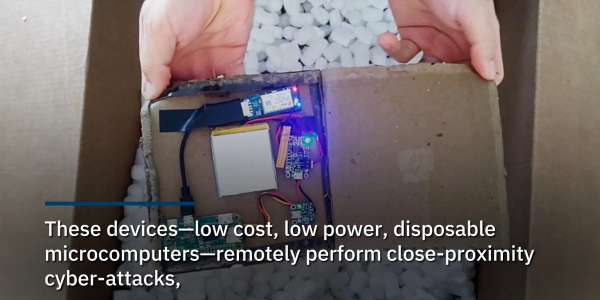
When WiFi first came out, it was a super exciting time. The technology was new, and quite a bit less secure back then—particularly if not configured properly. That gave rise to the practice of wardriving—driving around with a computer, looking for unsecured networks, often just for the fun of it. [Simon] has been examining this classic practice from a modern perspective.
He’s been at the game for a long time—from back in the days when you might head out with a thick old laptop, a bunch of PCMCIA cards, and dangly antennas. It’s much more advanced these days, given we’ve got WiFi on all different bands and Bluetooth devices to consider to boot. Heck, even Zigbee, if you’re hunting down a rogue house full of Internet of Things gadgets.
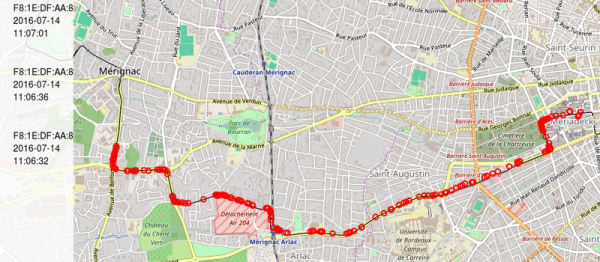
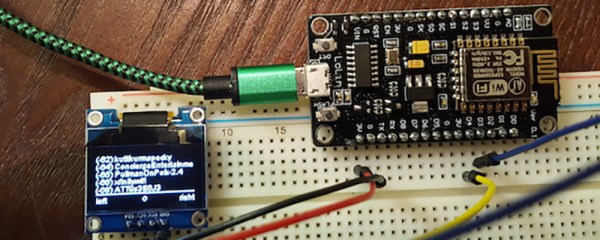
Today, when he’s out researching the wireless landscape, he uses devices like the Flipper Zero, the Raspberry Pi, and a Google Pixel 5 running the WiGLE WiFi Wardriving app. [Simon] notes that the latter is the easiest way to get started if you’ve got an Android phone. Beyond that, there’s software and hardware out there these days that can do amazing things compared to the simple rigs of yesteryear.
If you’re out looking for free internet these days, wardriving might be a bit pointless given it’s available in practically every public building you visit. But if you’re a wireless security researcher, or just curious about what your own home setup is putting out, it might be worth looking at these tools! Happy hunting.




 Enter the
Enter the 









