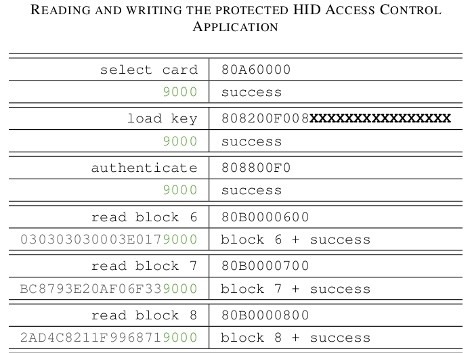
iClass is a popular format of RFID enabled access cards. These are issued to company employees to grant them access to parts of a building via a card reader at each security door. We’ve known for a long time that these access systems are rather weak when it comes to security. But now you can find out just how weak they are and how the security can be cracked. [Milosch Meriac] delved deep into the security protocol for HID iClass devices and has laid out the details in a white paper.
The most invasive part of the process was breaking the copy protection on PIC 18F family of chips in order to read out the firmware that controls card readers. This was done with a USB to serial cable and software that bit-bangs its own implementation of the ICSP protocol. After erasing and attacking several chips (one data block at a time) the original code was read off and patched together. Check out [Milosch’s] talk at 27C3 embedded after the break, and get the code for the ICSP bit banging attacks from the white paper (PDF).
[youtube=http://www.youtube.com/watch?v=mZNSYw9oH4Y&w=470]















Very interesting read and nice idea on how to extract ‘copy protected’ PICs.
I worked with Milosch at The Last HOPE for the RFID tracking project (AMD). It was a lot of fun. I was surprised but delighted to see his name show up here working on some more RFID research. Both he and his wife were awesome people to hang out with at HOPE.
Great read. Amazing how simple the strategy for breaking the PIC code protection turned out to be too. I didn’t quite get the part about reading the fuse bits though. I take it these just don’t get obfuscated in code protect mode.
This is a fairly major fail on Microchip’s part but equally the iClass folk are to blame for entrusting their global DES keys to a single line of defence.
I’m curious if they use the same keys for their Proximity line of badges (125kHz I think?). Our entire enterprise uses HID Proximity badges for access to everything. :-/
Proximity cards are far worse than iclass cards. The 2 are not the same, and actual Proximity HID cards can be cloned with a single device sold on Amazon for less than $35
Whoops, just watched part of the video and apparently HID Prox = no encryption! :-(
If anyone has the iClass keyfob, I’m looking to purchase one. Shoot me an email.(my username) at pihack.com
So if I’m looking at putting in a keycard system somewhere, which one IS actually secure? :)
thanks!
We have just upgraded to HId’s new SE technology, which uses 128 AES. we can use any cards we like which is great, but we opted for their SIO,