If you’ve ever purchased a new computer then you are probably familiar with the barrage of bloatware that comes pre-installed. Usually there are system tools, antivirus software trials, and a whole bunch of other things that most of us never wanted in the first place. Well now we can add Superfish spyware to the list.
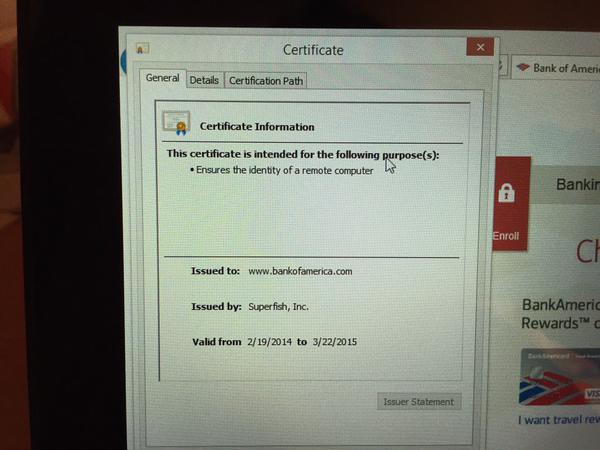
You may wonder what makes this case so special. A lot of PC’s come with software pre-installed that collect usage statistics for the manufacturer. Superfish is a somewhat extreme case of this. The software actually installs a self-signed root HTTPS certificate. Then, the software uses its own certificates for every single HTTPS session the user opens. If you visit your online banking portal for example, you won’t actually get the certificate from your bank. Instead, you’ll receive a certificate signed by Superfish. Your PC will trust it, because it already has the root certificate installed. This is essentially a man in the middle attack performed by software installed by Lenovo. Superfish uses this ability to do things to your encrypted connection including collecting data, and injecting ads.
As if that wasn’t bad enough, their certificate is actually using a deprecated SHA-1 certificate that uses 1024-bit RSA encryption. This level of encryption is weak and susceptible to attack. In fact, it was reported that [Rob Graham], CEO of Errata Security has already cracked the certificate and revealed the private key. With the private key known to the public, an attacker can easily spoof any HTTPS certificate and systems that are infected with Superfish will just trust it. The user will have no idea that they are visiting a fake phishing website.
Since this discovery was made, Lenovo has released a statement saying that Superfish was installed on some systems that shipped between September and December of 2014. They claim that server-side interactions have been disabled since January, which disables Superfish. They have no plans to pre-load Superfish on any new systems.















Yikes… Why didn’t they just call it like it is: Superphish.
Ha. Where is the *like* button ? ;)
Careful, you might accidentally click that report comment over there, it’s sneaky at times.
little known to people, there’s a CLI version of this exploit.
(wait for it…)
its called “shellfish”
LOL
Swordfish (groan!)
No, that was the password…
The password is “komodia”, actually :-) Weak encryption options don’t matter if a dictionary search can find the password, or if it’s hidden in the application, which somebody found that it was.
This is a lot worse than just more bloatware on the box – it means that anybody can create an SSL certificate for “Google.com” or “microsoft.com or “mozilla.org”, sign it with the Superfish cert, and anybody running one of these machines will believe it. Thought you were downloading a software update for FireFox from Mozilla or a security fix from Microsoft?
I just read this in the morning on BBC news. I wonder which models they preload this software on. I mean Lenovo has a lot of high-value corporate customers; I’d imagine HP, Dell, Toshiba, Acer, etc. are taking advantage of this revelation to steal some of those away.
BTW, if you’re going to install a spyware, at least come up with a less villainous name than “Superfish”. (c:
The did mention it was installed only on consumer systems. I’d imagine this includes any system with the term ideapad in the name. I seriously doubt they’re stupid enough to compromise business systems with this crap. It’s only the rest of us that they don’t care about.
I sure hope they’re not that stupid or they may have just sunk their laptop division.
Also, I think corporate customers have their own standard images that they flash onto their computers. IOW, they don’t usually use the stock factory images.
The affected models were from roughly October-December 2014. If you look in the Control Panel Programs&Features (or whatever Win8 calls it), you’ll see Superfish there if you’ve got one of the compromised systems, in which case you not only want to remove that, you need to go clean up the SSL certificates as well. Otherwise you’re fine.
Our corporate Lenovos aren’t affected, because the IT department installs their own build of Windows with all the company applications, MS Office, etc. pre-configured, rather than adding stuff to the consumer shipped images.
OK, I finally got around to reading Lenovo’s statement. So, the corporate-oriented Thnkpad line isn’t affected.
Still, it’s very naughty of Lenovo.
“OK, I finally got around to reading Lenovo’s statement. So, the corporate-oriented Thnkpad line isn’t infected.”
FTFY
I would imagine the whole company will be affected. :)
It is well known in every secret services department that Lenovo computers are fully infected with softwares used for spying purposes (thanks China). There was a big story about this when the French Defense changes all their computers for Lenovo computers. Superfish is just for customers. You can guess that a lot of spying softwares are still installed in some firmwares of some components in computers for businesses. It’s not even like businesses care about this. There’s still a lot of businesses that are completely strangers when it comes to informatic security….
I know every single US owned or made software or hardware has/creates backdoors. And I know all sony software and devices do.
And of course any european soft or hardware GHCQ/NSA can get near in any way.
yep got it…it loads some script into google chromes rrs plugin…go in yourself and disable it and add some host file site blocking.. if you use inspect elements in chrome you will see the superfish js script in local ..im sure it dose more but thats as much as i figured out
It installs a self-signed root certificate authority in the user’s certificate store. Worse, it is the same certificate for all Lenovo installations. Even worser still, this certificate has been cracked , meaning anyone can carry out man-in-the-middle attacks on affected systems.
Users should *absolutely* uninstall the service according to Lenovo’s instructions but should also go the extra step of removing the certificate.
Better idea is to trash the Lenovo and send it to their CEO with a little note on why you will never buy their product again.
Trash it? Were are on HaD, we don’t need to trash things, we re-use.
Also, once the class action starts to pay out you want to have evidence to be able to collect.
Ain’t lenovos made in China and Years ago there were reports on the news that many Chinese made computer systems “may” be shipping pre-loaded with skyward ect. Anyone who is in the know at all and buys a new pc and doesn’t do a system wipe on it out of the box is had kinda got whatever they have coming to them..
This is nothing compared to the bull$hit the Americans are pulling anyway. when there is spy soft written directly into the firmware on the chips that operate the high and low level functions of your hard drive there isn’t much you can do to protect your data.
Reference to the firmware in hard drives accusation please.
Kaspersky made the claim. http://www.cnet.com/news/nsa-planted-surveillance-software-on-hard-drives-report/
The “Equation Group” variety of malware hides in WD, Seagate, and some other HD firmware. Kaspersky believes it came from the NSA:
http://mashable.com/2015/02/17/equation-group-what-to-do/
Firmware in the following hard disks for sure:
WDC
SAMSUNG
Hitachi
Maxtor
Seagate
Toshiba
Ref: http://arstechnica.com/security/2015/02/how-omnipotent-hackers-tied-to-the-nsa-hid-for-14-years-and-were-found-at-last/
http://www.computerworld.com/article/2885069/theres-no-way-of-knowing-if-the-nsas-spyware-is-on-your-hard-drive.html
Any article that makes any references to Steve Gibson as a, “security researcher,” is automatically full of garbage. Any article that refers to Gibson as a Software Engineer ought to have the writer dragged out and hung.
superfish is american
well shit.
People actually run pre-loaded bloat infested laptops without first scrubbing them and doing a fresh (customized) install?
PT Barnum was right.
Some people don’t have ANY choice. I bought a brand-new Asus laptop just last week. There is no optical drive, and therefore no factory software in the box, aside from what came pre-installed on the HD.
This was exactly what I did:
downloaded & installed chrome (under windows)
downloaded & installed uTorrent (under windows)
used uTorrent to download the latest version of ubuntu (10.14)
downloaded an md5 checksum tool to verify a good iso image
installed the drivers for the external optical drive (for & under windows)
burned ubuntu 10.14 to disk
got online in order to figure out how to get into BIOS
installed ubuntu 10.14
So, I didn’t completely get rid of windows, but it is there more for games than anything. But, back to my initial comment. 1) My brand-new laptop does not have an optical drive, period. 2) Even if it did, I was not provided with any software that WASN’T pre-installed. I purchased an external drive because it was necessary in order to install my preferred OS.
Most people aren’t concerned enough to bother, and if I didn’t PREFER Linux, I probably wouldn’t have bothered to change it. And, in the large majority of cases, the omission of that DVD-ROM just means less clutter in desk drawers and less material to fill a landfill. The last few brand-new “company” computers I have seen haven’t come with a “Genuine Microsoft Windows” disc anyway. They come with a HP/Dell/Gateway/Packard-Bell Windows install disc, which includes the drivers that the company deems necessary to bundle. So, you are STILL screwed, unless you buy a “Genuine Microsoft Windows” package, or can somehow get same sent to you from the company that made your computer.
And, ultimately, there is the issue of trust. You trust your doctor not to inject you with ebola or HIV when you go for a checkup. If anyone who has read this far, I recommend reading this wonderful little ACM classic: Reflections on Trusting Trust, or this version [pdf].
Install from USB:
http://www.instructables.com/id/Install-any-linux-from-a-usb-the-easy-way/
Probably best to avoid Ubuntu if you can, I hate that anything I type into the search box (looking for a local file) is sent to the parent company to be stored for life. Maybe move over to Mint ?
I am aware of being able to install from a flash drive, but I also wanted to be able to burn CDs & DVDs, and I got a blue-ray drive in hopes that I will be able to watch blue ray movies (I haven’t tried it out yet).
As to Ubuntu, it was just the last distro that I ran (that has been several years ago), and I liked it then, and didn’t have any compelling reason to switch. Before Ubuntu, I ran SuSE, and Slackware before that. That was back when Slackware was considered a major-league distribution. And back then, you could count the major distros on one hand (Corel, Debian, Red Hat, Slackware, & SuSE). Yggdrasil was still around, but it was being eclipsed by the others. I am not completely sure that I am happy with Ubuntu now, but that may just be my rust.
Are you referencing canonical or is there some other spyware I should know about?
http://www.theregister.co.uk/2014/08/07/ubuntu_passes_ico_data_smell_test/
There is a workaround @ https://fixubuntu.com/
“If you’re an Ubuntu user and you’re using the default settings, each time you start typing in Dash (to open an application or search for a file on your computer), your search terms get sent to a variety of third parties, some of which advertise to you.
Ubuntu should protect user privacy by default. Since it doesn’t, you can use the code to the left to disable the parts of Ubuntu which are invasive to your privacy.
Note: This privacy problem only affects Unity. If you use GNOME (sudo apt-get install gnome-shell) or any other desktop environment, or if you run an Ubuntu derivative like Linux Mint, Xubuntu, Kubuntu, etc., you won’t have this problem.”
Why use an optical drive at all? Basically any OS can be installed off of a 4-8GB flash drive these days.
Not on every computer.
Most definitely on a brand new Asus without an optical drive :)
Flash drive microcontrollers have been cracked to allow unlimited access to the attached computer with no means of detecting the exploit prior to installing the flash drive.
That is almost completely false. The usb drive does not magically get full access to the conputer, it can’t read files off the computer. What it (Badusb) does do is most commonly emulate a HId device to enter in commands, but this can be easily stopped. Various hacks using the badusb framework, like editing files that cross it, are, as far as I know, still theoretical.
Normally USB does not allow unchecked DMA to the host memory. You would need an exploit in the USB stack to compromise the machine.
Other standards such as FireWire and Thunderbolt do allow directly writing the host memory AFAIK.
@Maxwell: What is “false”? Who said anything about “Badusb”? The problems go much deeper down the rabbit hole than that.
USB flash drives, SSDs, and SD cards contain microprocessors to manage write wear leveling and other things. According to Bunny Huang (and others), many of these mass storage devices can to hacked to run arbitrary code on the processor INSIDE the storage device (allowing MITM attacks, which CAN access and modify data, including code, on the host computer):
http://www.bunniestudios.com/blog/?p=3554
And of course, in the news lately is a report that hard drive firmware has been hacked too. Kapersky reported that many hard drives contain a stuxnet-like firmware virus that monitors network traffic, compliments of the NSA… This is beyond reports in past years of network jacks and other embedded components on motherboards containing NSA hacked components. Privacy? What’s that?
Also, you can usually find the windows image files online hosted by Microsoft. I believe they have a simple means of recovering the software. Then you just need the installation keys that are usually on the bottom of your laptop
Windows 8 uses UEFI/Secureboot in stead of the old BIOS. This means the Windows key actually gets encoded in the firmware of the laptop. No more code stickers that people forget to install. When you do a fresh install of Windows, it automatically detects the key on installation and activates automatically too! It’s quite nifty. If you open the “BIOS” on such a computer you will see somewhere a Windows product key written there.
This is why it’s a bitch to do dual-boot with Windows 8. I gave up. Most linux distros still have piss-poor support for UEFI and it’s best to disable it all together. Then you have to provide your own key for Windows if you want to dual install it.
Install Arch Linux and grub-uefi
Yep but what do you do when the heat from your computer and the friction against a surface removed a part of your poor-quality sticker (own experience) ? Plus, they are not always delivering a windows CD with your computer. If you don’t want to spend weeks trying to get one from the company, you just unlock Windows with some software…. They are pushing you to pirate it !
Any media/rescue partition included with the laptop will be infested with the same bloatware that came installed on the laptop. You need a clean OS disk/image to install, and then get the drivers (and only the drivers) from the manufactures website. No optical drive – $20 to get a USB DVD player from NewEgg (or just install from a USB flashdrive).
There really isn’t an option sometimes, I tried to install Ubuntu on a laptop I recently purchased, and it was impossible. It’s just a little 10 inch netbook with a touchscreen that I use for browsing in bed or when laying about the house. But I tried really hard, lol. I tried USB install, not happening. I tried putting the necessary files on a separate partition, no dice. I even tried burning it to a CD and using my USB disc drive to load it, still it refused. I’m sure I’m just not 1337 enough, but the moral of the story is they locked this thing down pretty hard. Luckily I don’t use it for anything important, so it’s not bad. I just really wanted some Linux to play with occasionally…
You can disable UEFI and SecureBoot in the BIOS and it should work. I had similar problems with a Windows 8 laptop. They made it really hard to dual-boot. Google how to disable UEFI and the like and you will be ace. Also, try using a new flash stick/one you trust. In my experience things often get corrupted on older hardware and then the installation fails.
Why 10.10 and not something that still has support? 12.04 ,14.04 or 14.10?
You seriously think nobody can infect hash checkers for their own benefit? Or intercept a download initiation and replace the software for that matter. I mean the NSA for instance is known to intercept actual commercial DVD/CD in shipping and replace them with identical looking infected ones, so doing it through software is just so much easier.
Oh you bought that Toyota model that had the faulty accelerator pedal and didn’t take the whole car apart just in case. Jeez, ain’t you stupid and deserve what you got.
I had this installed on my Lenovo Y-50, how I discovered it, was that all socket IO connections got disrupted, and this happened the beginning of this month (4 feb), so it actually didn’t get disabled and still spied around.
Its actually been around for over 6 months at the least, going by forum topics/replys on lenovo forum, so lenovo is just trying to cover their asses in the released statement, and they prolly still ship with superfish
A comment I read on one of the articles about this said the original press release said October to December before the forum post mentioned seeing it in September. Now the statement reads September to December. I would lay good odds it has been installed even before September.
Usually the rat bastards who create this kind of crapware will take care to place an installer in “scheduled execution” in widows (and often a backup system service cloaked in “svchost” to block deletion of “files in use”) to re-infest the computer. The installer is normally called something different like “UpdateManager” or even just a hex string. They will also place it at several time intervals and to trigger on different conditions (yes … the windows scheduler “language” is probably turing-complete).
One of the worst offenders is Snap.Do or indeed anything from ReSoft LTD – may they all rot & die from a multi-resistant strain of flesh-eating clapp! That little piece of filth will also sometimes hijack the “program manager” and “windows search”, and it burrows into everything;
After removing the crapware, it is wise to delete *everything* scheduled except things owned by Microsoft (like the disk optimiser and whatnot).
Actually, The fastest is probably to go back to a known good system restore point from before the filth was installed. Then immediate install an anti-malware tool (malwarebytes or similar) – because something dragged that in and that sucker is still sitting there in the web-cache (java-script) or in … /appdata/roaming/
You make some very good points but fall down when you suddenly show a weird trust in microsoft.
If you install windows and check the scheduler you will notice that MS actually has several things running to report all your private info to them, which they spin by calling it ‘customer feedback service’ or ‘user satisfaction feedback’ or ridiculous euphemisms like that.
Same with IE which at some point started to ‘assist people’ by reporting every URL entered in the address bar to MS. To ‘help’ the people don’t you know.
So in fact even a plain default windows install is full of crapware really.
So no word on why this was installed? Dishonest employee? NSA watching us? Or something sinister?
First line of their statement:
“Superfish was previously included on some consumer notebook products shipped in a short window between September and December to help customers potentially discover interesting products while shopping.”
So they did it to earn extra money from ad revenue.
Normal reason is money, someone offered them money to install crud. They probably keep half the money and use the other half of the money to sell the hardware at a lower price.
Lawsuit? It’s completely unacceptable, and businessmen need to be taken to court when they meddle with their/a company’s product offerings.
Lenovo ThinkPad Edge E545 with AMD A10 APU assembly date September 8 2014. It came with Superfish installed. Thankfully I did a complete scrubdown of ALL non essential software and started fresh.
Dammit Lenovo. It’s a good machine but crap like this will make me hate you as much as I hate Acer…
I love their laptops. To bits!
But yeah. I don’t even bother booting up a brand new laptop any-more. It gets reformatted immediately.
Can we lose the apostrophe? The plural of PC is PCs.
Could we also get an editor or proofreader at hackaday? Or better copy writers.
+1
You volunteering, chum?
Gladly. What does it pay?
This just reaffirms my decision to build my own computers and never buy one off the rack. Since I don’t need a laptop and likely never will, this works fine for me.
I feel bad for the folks taken by scams like this. Most people using laptops these days (current crowd excepted, of course) aren’t computer literate enough to know how to identify and remove crap like this. Lenovo should be ashamed of themselves.
MOTH R FUNGER
“If you’ve ever purchased a new computer then you are probably familiar with the barrage of bloatware that comes pre-installed.”
If you’ve ever purchased a new windows computer, that is. OSX and Linux don’t ship with tons of bloatware.
This.
I’m surprised it took this long for someone to say that.
You can make the claim that you’re simply trading one set of evils for another when you buy a mac, and Apple’s history is not completely blameless. But Apple of late has cut way back on the (already quite sparse) selection of third party software preinstalled, and all of it is applications that do nothing but take disk space until and unless you run them. And any all of them can always simply be dragged to the trash.
I cannot speak for OSX, but I can say something about Linux in this regard. While I wouldn’t use the term ‘bloatware’ for any particular program (I am sure that there are, and (x)emacs could potentially be considered), but sometimes the distributions themselves seem a bit bloated. I have seen several different distributions, and all of them have wanted to install a good half-dozen DIFFERENT window managers. Or more than eight different shells. I know that nowadays drive space is not a serious issue, and I DO like to have a choice in the programs I use, but who needs a dozen-odd music/multimedia players installed? Not me. I would like to have one GOOD music ripper/player/organizer. I don’t mind each of those functions beings in the form of different tools, and have done that in the past. But when my player has a good-enough ripper, and so does every other music or multimedia program installed, I think I can stand to be a little-bit choosier. I don’t need all dozen multimedia players installed, especially when I am unlikely to ever have more than two or three other people with accounts on my system.
In other words, while I like to have options, I don’t like to be overwhelmed by them either. And most distributions want (or at least did want) to either install absolutely EVERYTHING, or have you go through each and every group, and decide yes/no on each individual program.
What are you talking about? Which distribution(s) installs “a good half-dozen DIFFERENT window managers. Or more than eight different shells”? Or “a dozen-odd music/multimedia players”.
Are you making this up?
The oldest one, Slackware. Its from before online package repositories were easily accessible so it includes many ways for the users to customize it.
There’s plenty of spyware-ish bloat ware on the distros that get shipped with laptops.
Take the good old example of unity Ubuntus DM (when it first came out at least) which passed *all* your search terms to amazon for ad purposes!
I remember getting a opensuse netbook a few years back which had similar barrage of crap pre-installed.
You might get a bunch of similar programs on *nix distors, because the mentality that each program should do one thing well and one thing only. You shouldn’t get a multimedia suit, you should get a movie player, a music player and a cd imager these should be seperate.
Branded Linux are the worst I have ever seen. Most of the time they are locked and ugly (looking at you Linpus Linux Lite) or if you are lucky enough (well, I don’t know if “luck” is the good term) to have a branded Ubuntu, it can be a few years old and won’t update until you find a way to unlock it (I’ve seen 2007’s Ubuntu versions on 2010’s computers). No wonders why lots of people think Linux is shit when they are just using branded Linux on freshly bought computers.. I don’t want to buy preconfigured computers anymore. Just going to Sager or a brand like this, make your own laptop and install your own system is the best solution I’ve ever seen.
This is one of my pet peeves about people boasting how Linux doesn’t get virsues, etc… Linux can get virsuses just like any other OS as long as people write them for it. And they are NOT inherently more secure unless you know what you are doing and do all the appropriate set up. There are plenty of security holes in a non-optimized distro. And people hack into linux systems all the time because of improperly set up security or exploits.
The REAL problem is the same as it is with Windows. If the user doesn’t really have the knowledge (or will) to properly secure their system, it is unsecure. Regardless of which OS is used.
Linux is not generally targeted for a typical generic computer users and the distros that are pack them full of crap just like this.
The bottom line is that the user is the best and only real protection of security of their computer and network. When you are looking at mainstream boxes for the average generic computer user, all operating systems have the same problems. Granted there are more viruses written and exploit research done specifically for Windows because that is what most people and businesses use so you have a much bigger pool of victims. If Linux were it, then the same effort would be placed towards linux.
I am operating system neutral. I use whatever does the job.
Linux distros ship with “systemd” – which kind of balances the scales, Me Think
Locked down android phones make up the majority of Linux installs in the wild. When your strategy is to ignore that which is inconvenient to you, you will not see the thing that will inevitably devour you.
Various Linux distros have been including crap for a while now.
“oops, they caught us, I guess we can never do that again.”
Does anyone know if PC Decrapifier cleans this up?
PC Decrapifier, is a fantastic, quick and easy way to clean up a new Windows PC without needing a reinstall.
“without needing a reinstall”
That’s highly debatable.
My Decrapifier is a reinstall.
I’m a lenovo customer, I have two of their ideacentre pc’s as my main desktops with a 3rd big box one belonging to a corporate paymaster. I like them because they’re small, and the q190 has more than enough punch for what I need, which almost amounts to run a browser, wm and a terminal session most days.
Happily the first thing I did with my two was to unscrew the hard disks, put them in the cupboard and install gentoo.
It does not surprise me in the least they have done this though. But, before we rant about chinese spyware, lets not forget other major MITM attacks a lot closer to home. Eg Phorm (mitm half the uk’s internet and sent it off to 3rd parties in the usa to datamine), nsa etc.
They’re all just playing the same game.
It is a shame that Motorola is now owned by them. With lack of bootloader and root support in these devices, we may never know.
Well I for one would like to thank Lenovo, before I had to spend veritable minutes on the internet before I my computer was infected with spyware, not it comes infected out of the box, what a time saver!
You mean before it was infected with THEIR spyware.
Avast Anti-virus also hijacks SSL certificates. Check this out…
http://oi61.tinypic.com/2jewk0h.jpg
Why doesn’t hackaday have a ssl? Where’s the https?
Have a Lenovo and got curious?!
http://www.cnet.com/how-to/lenovo-superfish-adware-uninstall-fix/
Why care? All CPUs and communications chips have HARDWARE backdoors designed into them by their respective governments!!! ;)
But really being this clumsy and wide open to the lowest hackers is embarrassing.