Small Office and Home Office (SOHO) wireless routers have terrible security. That’s nothing new. But it is somewhat sad that manufacturers just keep repurposing the same broken firmware. Case in point: D-Link’s new DIR-890L, which looks like a turtled hexapod. [Craig] looked behind the odd case and grabbed the latest firmware for this device from D-Link’s website. Then he found a serious vulnerability.
The usual process was applied to the firmware image. Extract it, run binwalk to find the various contents of the firmware image, and then extract the root filesystem. This contains all the code that runs the router’s various services.
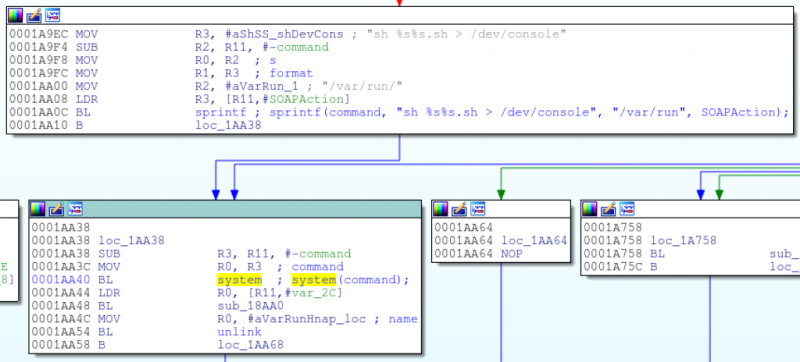
The CGI scripts are an obvious place to poke for issues. [Colin] disassembled the single executable that handles all CGI requests and started looking at the code that handles Home Network Administration Protocol (HNAP) requests. The first find was that system commands were being built using HNAP data. The data wasn’t being sanitized, so all that was needed was a way to bypass authentication.
This is where D-Link made a major error. They wanted to allow one specific URL to not require authentication. Seems simple, compare string A to string B and ensure they match. But they used the strstr function. This will return true if string A contains string B. Oops.
So authentication can be bypassed, telnetd can be started, and voila: a root shell on D-Link’s most pyramid-shaped router. Oh, and you can’t disable HNAP. May we suggest OpenWrt or dd-wrt?
















s/Colin/Craig/g
Wow, sorry. Fixing that.
Note he used /g.
That means you should have scanned the entire text.
In other words, one Colin remains.
There can *be* only one!
I buy all routers with the express purpose of putting an open source firmware on it. if I can’t do that with the router, then I will not buy it. Even then I don’t totally feel safe anymore.
Same here, OpenWrt FTW.
Still it’s a shame we don’t always get best performance out of the hardware (HNAT for example). 802.11ac support is still quite wonky (few atheros devices, maybe some blob drivers for broadcom).
I got an Archer C7 for OpenWRT and then stuck with stock because of the HNAT :(
What’s the big deal with hardware NAT? I’ve toyed with it, and I immediately convinced myself that it’s not a thing that I’m interested in: Immediately gone was all of the QoS goodness that I’ve been using for aeons to keep the household happy, whether gaming or Netflixing or torrenting — all at once. (Yay Tomato!)
Maybe if I had Google Fiber I’d be looking seriously at hardware NAT (since the bottleneck would almost always be very far downstream and completely out of my hands anyway), but at the moment I get better real-world performance without it.
That said, I’m still confused as to why it matters about security flaws in New-Hotness router: Why is it routing at all? As long as WPA is secure and the thing is firewalled, who cares?
Step 1: Buy a router to route, and let it do its NAT routing thing using a somewhat-trustworthy open firmware and let it do 802.11b/g if it suits you (2.4GHz 802.11n is almost always a mistake). It’s easy to find a very fast router with good open third-party firmware, if all you care about is routing performance and 802.11b/g. (An old WRT54GS or GL will do fine on for these roles on my 18/1.5Mbps VDSL, even with QoS rules, and my current Asus RT-N16 hardly even notices that it is routing. YMMV.)
Step 2: Buy an 802.11ac access point, and let it be an access point, using whatever firmware, and keep it behind the firewall implicit in step 1.
Please note: Step 2 might involve a COTS thing that calls itself a “router,” but which becomes an access point once its own DHCP server is disabled. Bonus points for plugging it into your somewhat-trusted (step 1) router and hiding it in plain sight. Start by putting it on its own logical subnet, VLAN, or physical subnet — be creative.
Is there an OpenWRT available for it? Because it’s always about 900X better than anything Linksys’s programmers can come up with.
I doubt OpenWRT works properly with this router. 802.11ac support is still pretty bad and the driver they do have doesn’t work 100% yet according to the forum.
Pretty much all consumer routers aren’t actually designed by the companies that sell them. They’ll buy in a premade design for hardware + firmware from somebody like Sercomm and then put it into a fancy case + brand it. The original firmware will have horrendous code + flaws and then whoever is contracted to mod the firmware for the company will add their own screw ups. It is also why they tend not to have glaring issues and flaws fixed.
There’s already a sequel: http://www.devttys0.com/2015/04/what-the-ridiculous-fuck-d-link/
that’s laughably bad.
It looks like a dead stinkbug, stinks like one too!
I think I’ll rename all the dlink’s on my network to be ‘strstr’ and ‘sprintf’. just in their honor.
wait, honor is not the right word.
What is the application/script used in the article to generate those “code flow” boxes?
IDA
Why doesn’t he just sign a contract w/ Cisco or D-Link sometime and remove all these sprintf bugs? That would be a funny awkward meeting to see. Jesus, I bet he has a picture of both companies in his room like Ray Finkel lol “laces out! die dan die!”.
Kidding, routers are too important for closed source firmware w/ most likely forced backdoors (even though practically no one will read it and actually understand it all).
And really that’s the same reason open source has it’s flaws as well. 9/10 people will simply download the open source software and install it with a script having no clue what is in the code. So all it would take is for someone to insert nefarious, but clever backdoors into the code and you are worse off than D-Link because at least you can sue D-Link for doing it.
And trust me, open source has holes and flaws just like anything else. You could argue that, yeah, but it’s open source so people will close them. And so will D-Link and the rest when they discover them. But with open source, again, 9/10 would have no clue how to even re-compile the firmware themselves so they will have to wait on others to patch the holes.
The truth is with Linux even, 9/10 simply install it COTS from a script. Most linux users have no clue how to create a kernel or even secure their systems after the install and instead rely on the default settings.
It boils down to an elitist attitude and that’s all. The only reason Linux is more secure is because nobody really writes viruses for linux because it isn’t installed on 99% of the computers in the world. If it was, it would be the target. Common sense.
I am pretty happy with my Asus AC66U (iirc). Apparently ASUS took open source router software, customized it, rebooted the user interface and released it open source.
There’s even an open source derivative firmware called Merlin that patches in advanced functionality on top of official firmware. In fact there’s been a symbiotic relationship between the two. I believe some of Merlins features were introduced into later official firmware.
I have this router and have been pleased with its performance, features, and stability. Supports AC fine.
Don’t like it’s firmware? install your favorite flavor of open source firmware. The hardware is capable.
Most of the routers these days use bits and pieces of Open Source code and because of GPL, the vendors usually have the source code available. The memory prices are no longer the weak excuse that they would revert to closed source kernel (see the old Cisco with some of their later WRT54* revs).
Strangely enough that this particular model from D-Link didn’t show up in their GPL website. Not sure why, but it is something that people can ask D-Link about.
http://tsd.dlink.com.tw/GPL.asp
Just have to google gpl or open source with the name of the router vendors if you want to mess around with the source code before you complain about these things in general. If/when the source code are available, then the “community” could have fixed these issues, right? Can’t have it both ways.
Anyone who follows the gpl-violations mailing list will know that getting the correct source code (i.e. the bits they need to release in order to be compliant with the licenses) for many of these routers is very difficult. Many many companies continue to violate the GPL and it takes a lot of work by various entities to get the companies to comply.
And this would be exhibit A as to why I abandoned consumer routers altogether. Lately I’ve just been taking old boxes, throwing some extra NICs in there and slapping OpenBSD on top. So what if I don’t get a UI to manipulate it, at least I’m immune to ridiculous bugs like this. For the longest time I was using a machine I picked up from Goodwill for $25 (133 Mhz p-II, 256 MB RAM and a 10 GB Hard disk) and slapped in a couple 10/100 NICs and a PCI 802.11g card. The thing ran perfectly until the motherboard finally kicked (a couple caps blew an shorted out the power pins on the north bridge). Bought an old P-4 system to replace it for another $20. So much cheaper than even a standard “router”.
How about pfsense, then you get a GUI. It is FreeBSD though, not OpenBSD.
pfsense is ok for some things but I’m seeing some issues, lately. for one, there’s no good way to re-get a public side (north) dhcp addr. web gui won’t do it, cli won’t do it. rebooting does it, though, but that’s harsh. and it has no powerfail protection ;( it used to but not anymore. if I power it off abruptly, it does not recover gracefully! the whole web gui ‘goes away’ and many things break on reboot. you have to do a full install again!!!
I’m about ready to give up on this POS and go back to linux for my firewall router. with voyage linux, at least, its mounted readonly at boot and you can pull power at any time and not reliable boots again next time. pfsense totally misses that aspect and so for a firewall, it falls short.
the dhcp thing is my big problem with pfsense, though. if I reboot my cable modem, I need my firewall to get a new dhcp and it won’t unless I reboot IT.
PF sense is just a copy of OpenBSD’s PF firewall daemon, except lobotomized. In OpenBSD it would be a simple matter of encasing the name of the external interface in parenthesis in the rule set and then just running dhclient on the console…
I’ve never like GUI-based systems anyway, just one more thing to produce holes and fail when all I want to do is change some settings. I prefer to see the daemon restart rather than a dialog box saying “Restarting, please wait”
There are many embedded x86 options as well, many of them a few years old and pretty affordable. I routinely troll eBay for used PC Engines and Soekris boxes. If you need more throughput, pick up a Mini-ITX board and add a multiport Ethernet card.
Yeah, I have an order for two Soekris 6501’s in rack mount cases. Planning on setting them up for a redundant pair.
Watts a router spends vs. watts a Pentium 4 “preshott” spends?
Is a LinkSys/Cisco soho router more reliable/safer than a dlink? The name “Cisco” would make me assume so, but trusting names is one of the silliest things to do.
Linksys is Belkin, not Cisco, for overy 2 years.
http://www.bloomberg.com/news/articles/2013-01-24/cisco-sells-linksys-home-router-unit-to-belkin
Does anyone know the name of the code grapher used in the article?
I think this might be what you are looking for: https://code.google.com/p/idapathfinder/