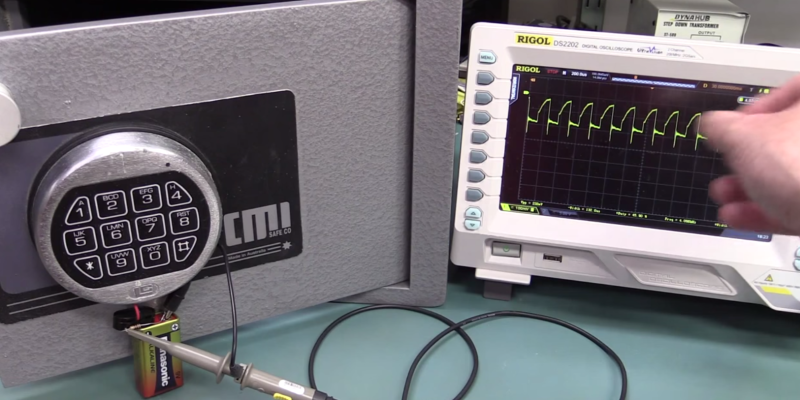
[Dave Jones] over at EEVblog got his hands on a small safe with an electronic lock and decided to try his hand at safe cracking. But rather than breaking out the thermal drill or shaped charge, he hooked up his Rigol scope and attempted a safe cracking via signal analysis (YouTube link).
We have to say that safes Down Under seem much stouter than most of the inexpensive lock boxes we’ve seen in the US, at least in terms of the quality (and quantity) of the steel in the body of the safe. Even though [Dave] was looking for a way in through the electronics, he still needed to deal with all that steel to get himself out of a face-palm moment that resulted in a lockout. Once that was out of the way, he proceeded to capture usable signals from the internal microcontroller using the only two available contacts – the 9 volt battery connections. While he did get signals, he couldn’t find any signatures that would help determine the six digits in the PIN, and as he points out, even if he did, brute-forcing through the one million permutations to find the right code would take too long, given the wrong-code lockout feature of the lock.
Even though he failed to hack into this particular safe, there’s still plenty to be learned from his methods. And who’s to say that other similar locks aren’t a little more chatty about their internals? Maybe you could even manage to EMP your way past the lock.















Didn’t we learn anything from 80’s hacker movies? All you need is bubble-gum and a paperclip!
Plus he failed to spray camo war paint on his scope.
I think he gave up far too easily. A little more analysis might have revealed timing differences at the end of a 6-digit sequence, but he never checked.
I was wondering that as well. If I were to write the firmware for this I wouldn’t read in the stored password from EEPROM until a full code had been received.
This is exactly what I was thinking throughout the entire video, too. I was a bit disappointed.
Even better, have a 1:1 map or hash or something and store and compare that, so you can’t resolve timing differences as “the first two digit were correct but not the rest.”
I think you meant constant-time comparison,
Please, somebody correct me if I’m wrong, I am only a mediocre programmer at best. But I reckon since you don’t have to worry about when to start your six digit sequence, the programming probably has a buffer of the last six keypresses and compares it to the correct code after each keypress. A simple bitwise comparison of the buffer to the correct code would not differ between a correct code, a single wrong digit, and all wrong digits, only the comparison result would (obviously) trigger differently between right or wrong code.
(Addendum: Note the absence of a “clear” or “start over” button on the keypad. I might be totally off though.)
Ugh, I take it all back, sorry. After rewatching the relevant part of the video, the lock indeed wants you to enter six digits and then confirms or denies, so no shifting buffer there. Yes, it would have been nice then if the comparison routine isn’t programmed in a completely idiotic way (i.e., returning after the first wrong digit it encounters). That would have been nice to confirm.
Seriously, the big weakness of these is that the membrane keypad wears very quickly from finger presses. Greatly reducing the number of possible combinations.
how exactly is that a weakness? Seems like preventing a brute force attack is what the safe is supposed to do (in fact there are firmware features to prevent such things)
Because if your password is 346872, those digits will be worn on the keypad. So, you would know that you don’t need 0,1,5, and 9. The number of brute force attempts needed is severely reduced.
I’d call that a weakness. Wouldn’t you?
And if only 5 numbers are worn, you know one of the numbers is repeated twice. 4 numbers, and either one number is repeated three times, or two numbers are repeated twice. Each time, reducing the number of possible combinations dramatically.
The problem is that the safe locks you out after three incorrect attempts. Waiting and brute forcing this is not something you want to do if you are a burglar that needs to get out ASAP before the home owners or the police shows up. So from that point of view this is pretty much good enough.
I’m sure you can defeat the lockout by just cycling the power. That’s a classic trick with things that attempt to prevent brute force, drop them before they can write the failure to flash.
Because the key presses are usually visible to the naked eye as the buttons are tarnished. One of the reasons i have rfid based security in my work, yes rfid can be cloned but its much easier to see what buttons my oily fingers have pressed lol
Actually if you watch the video, he does the same using a thermal camera. However, unless the code is very simple, the number of possible permutations is still astronomical, especially if repeated digits are allowed. The timed lockout feature is a very effective deterrent making this sort of attack pretty much unworkable on this type of safe.
Which is why you change the code periodically, so the worn-out keys will mislead the attacker.
Yep. But you and I both know that people are lazy. That’s why hacking is often times very easy.
It’s not my gig, but I bet there is a psychological table of what numbers are most often used in what combinations to make up a PIN. Things like picking two adjacent numbers the furthest apart, etc…
Nice article about pin numbers and what is often used:
http://www.datagenetics.com/blog/september32012/
Obviously a best practice, but I’d wager most people don’t follow the best practice.
The SCEC/(alternate agency) endorsed versions of these locks come with four buttons and an LCD display at the top (which you can only see if you look down into it) that displays a current value. To unlock, when you press a button, a random value shows up and you have to use an up/down key to get to the correct value. Once you select the correct value and press the enter key a new random value shows and you do that until a password is entered. It then unlocks if correct.
Not only are the keypads designed specifically NOT to do this, but they also do not retain thermal heat, so any attempt to view the keypad later with thermal imaging will be fruitless.
Stick with hacking small electronic bits…whatever you come up with here, has already been considered, and long forgotten by the adults in the business…
Well, the fact that it is STILL a problem on just about every lock I have ever seen might just mean your “adults in the business” are pretty fucking incompetent.
Like this:
https://pbs.twimg.com/media/ByyQFALIgAAQswf.jpg
https://verkoren.files.wordpress.com/2013/08/i-wonder-what-the-code-could-be.jpg
a powerful directed magnetic field should pop the solenoid open.
Um, through that thick steel acting as a Faraday cage? Good luck with that …
what about Magnetic Particle Testing yoke? the safe becomes a magnet.
That thick steel makes it a bit more interesting, but it isn’t that thick, and it isn’t a Faraday cage in this context.
The steel IS ferromagnetic, so it will provide some shunting of a steady-state mag field, but far from perfect shielding. Likely take a pretty strong field in the correct direction(s), but I would not be too surprised if the thing could be opened that way, though I would not expect it. Easy to design the thing to resist such an attack, using a relocker in the same orientation as the solenoid and close to it, so an attempt to open using external fields sets it hard, requiring a physical entry be used to ever get it open again. I wouldn’t count on such in a low end safe. I wouldn’t even count on protection against an inertial attack (hard drop in the direction of the solenoid… Opened a small gun safe this way a few years ago. Didn’t damage the gun)
Faraday cages provide eqipotential surfaces on the inside, and substantially on the outside, providing shielding against frequencies below a cutoff frequency that depends on the structure of the shield. A continuous surface of high conductance (copper, silver, aluminum) with no breaks, gaps, of regions of low conductivity is ideal. The safe is made of steel, and, unless gasketed, has breaks in conductivity at the door joint. Steel is an order of magnitude less conductive than copper, so not a good Faraday cage. I’d bet that sniffing emitted noise from the lock is a reasonable choice here, and the exposed battery access is a big help.
Umm, Faraday cages do nothing for large static magnetic fields, only electromagnetic waves (of certain frequencies, dependent on the cage construction). The large Faraday cages we have a work are made of brass, but they conduct static magnetic fields through their walls.
Now, if their solenoid is shielded with mild steel or other high-permeability metal (e.g., sintered iron), that might prevent such a hack. But then, with a sufficiently large and powerful electromagnet…
The good ones use a DC motor instead of a solenoid to prevent this type of attack and bump attacks.
This bloke has become unwatchable for me. I unsubscribed roughly a year ago. When I saw this video pop up in YouTubes ‘recommended for you’ section, I got excited. Maybe he was going to do proper teardowns, hacking, etc…
Remember the garage days anyone?
+1
I know that being a jerk is kind of his thing, but it’s just become so insufferable. If I’m learning something new despite it the video is worthwhile, but watching him feign emotion as part of an adherence to a poorly-thought-out persona isn’t worth the bandwidth.
The problem is there hasn’t been much “Electrical Engineering” in the EEVBlog in a really long time. Mostly just opening mail and taking trash apart.
I agree, there are still so many EE topics that would add value to the EEVBlog, but that’s all gone now. Sad. Have a look at the W2AEW YouTube videos. Many are quite instructive, plus they touch on RF topics. Dave on the EEVBlog seems to avoid all things RF.
Thanks for the link Drone. I’ll check it out. :)
Every electronic safe I have seen has the battery on the inside, so there would be no way to access the contacts. But this is a neat technique for cheap home safes anyway.
Having battery inside is a great recipe for disaster once the battery wears out. With properly designed controller (circuit protection, only necessary signals routed outside, etc), having battery outside should not compromise security of the lock.
They have cylinder locks as the secondary method of entry, usually.
I have seen a number of electronic locks with battery contacts. If your (internal) battery dies, what are going to do besides tear it apart? With an external battery connection, the lock can then be powered up and opened to allow the battery to be replaced. (and the lock/safe re-used)
https://www.ar15.com/archive/topic.html?b=6&f=46&t=363719
If you drill the lock, these pictures might help. That solenoid is what you’re aiming for.
I would have liked to finish the video with a quick “what if we dump 30V into the battery contacts” segment. He wouldn’t have even needed to do it, just look at the transistor and discuss whether it would fail and allow power to go to the solenoid. THAT is my kind of brute-force attack.
Never mind he didn’t make it. He’s a real hacker and I like the video.
Maybe some very glitchy battery voltage could fool the MCU enough to do the job?
You could actually keystroke these types of safes if you can manufacture translucent or transparent keyboard matrixes with a silicon RF solution or flash. It’d have to be 1mm thich tops, but ideally micrometers thick. This can actually be done even using 1980s manufacturing tech, but costly, but not too costly considering to steal large sums of capital and assets with the product. If you can get the silicon and a clear conductor you can do it with a 3D printer.
Other than that a lance or a good mains powered tungsten bit drill in the hands of someone who knows the trigger point for the model.
Your idea at a complex system/overlay to steal the password reminds me of this https://xkcd.com/538/
That’s why I suggest it’s impractical, Unless what you’re stealing from the safe is a hundred times the cost of manufacturing..
It’s not actually complex it’s just expensive to make.. The tech was being used on cheap handheld games in the 80s..