[anfractuosus] has been reading magnetic stripe card… optically!
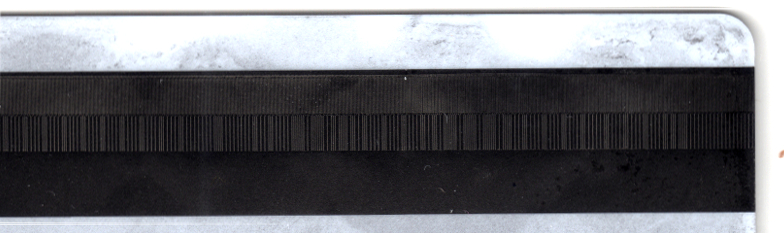
While hackers routinely read and write stripe cards, this is the first time we’ve reported on optically imaging and decoding data from the magnetic stripe. [anfratuosus] used a magnetic developer which is designed to allow visual inspection of the magnetic stripe. The developer uses micron sized iron particles in a suspension which are dropped onto the stripe. To the particles, the magnetic stripe looks like a series of magnets lined up. Long magnets ![]() represent 0s and short magnets 1s. With each bit the orientation of the magnet changes, something like the diagram to the right. The magnetic field is strongest where the poles meet. So the iron particles are attracted to these flux reversal points on the stripe creating a visible pattern . There’s an awesome video of the process in action below.
represent 0s and short magnets 1s. With each bit the orientation of the magnet changes, something like the diagram to the right. The magnetic field is strongest where the poles meet. So the iron particles are attracted to these flux reversal points on the stripe creating a visible pattern . There’s an awesome video of the process in action below.
While magnetic developer was designed for debugging faulty recording systems [anfratuosus] went a step further scanning the “developed” card, and writing a tool to decode the images and extract the card data. [anfratuosus] doesn’t mention any particular application, we love this circuitous hack anyway!
















I wonder if you could do something similar with a sheet of magnetic viewing film.
I did try that first, but it didn’t work, apparently they use nickel flakes in oil according to https://en.wikipedia.org/wiki/Magnetic_field_viewing_film I guess the capsules per square inch aren’t high enough, to work.
Magnetic nail polish works surprisingly well.
I actually tried that a few years back. Initially nothing happens, but if you leave the film on long enough (a few seconds) a weak pattern appears on it. But the resolution was too low to actually distinguish anything interesting.
In the first place, never knew such a liquid ever existed. Even more, it was commercially available!?
I’ll bet most of the people will think this is too cool to be true.
Really nice hack!
How hard is it to get off the card, or does it come off? Looks like something that would work well in a spy movie. Pickpocket a card, duck into a restroom, spread the goop on the card, snap a photo with a code reader app. Clean the card off and sneak it back.
back in the 90’s, now just use your phone and a card reader.
Skimmers existed in he 90’s too, they just didn’t use cell phones.
People coming into the event where the card needs to be copied get searched for the usual things that would work for such, but a small packet of this fluid, hidden under a shoe insole, would get past any electronics detection systems.
Pretty sure you could hide an RFID, or a smartcard (with the SIM-style connections) reader in a finger ring. If you were clever, or a TLA. Prob do mag stripe too, they’re coded to cope with a variable speed reading swipe. Is there such a thing as an electronics detector that works on switched-off stuff, and how is it different to a metal detector? You could prob hide something in a false tooth. Electronics come weeny these days.
With this fluid, a spy would still need a way to photograph it, or a hell of a memory for binary numbers.
A RFID reader inside a ring is feasible, a magstripe reader certainly is. You’d probably need a fair bit of practice to use the mag stripe reader.
Detecting electronics, even when inactive is possible. That’s called ‘non-linear junction detection’; you fire RF at a diode or transistor etc, the junction will emit RF back on harmonic frequencies. Well known bug hunting technique.
(Meanwhile everyone who isn’t American is saying “What’s a mag stripe, gramps?”)
The small magnetic particles just wipe off after it dries.
Haha, as opposed to just using a square magstripe reader for your phone? :-)
I wonder if a layer of cling film, pulled tight around the card, would be too thick?
Interesting to notice the increasing storage densitiy, for example between the 5″ and 3-1/2″ flexible diskette floppy.
!!! Searching asap.
I now want to record raw images into VHS tapes that can be seen with this stuff!
Apparently (image-search) the actual VHS-encoding (NTSC?) is a bit difficult to see images in, probably due to the various carrier-frequencies, Y-UV-encoding, etc…?
how’d I miss the video?
I worked with this stuff back in the late 90’s on payment card terminals. I was shocked that a magstripe is essentially just a barcode. There’s also a LOT of logic that goes into how you read it, it’s very difficult because there’s a person swiping it and variable speed and there’s no “pace” track (constant 0101010 pattern so that you can pace yourself). Lots of math goes into figuring out when the speed changes and using that to convert the analog barcode into digital.
This looks like a decent article hacking MSRs as well and shows some pictures:
http://electronics.stackexchange.com/questions/103369/reverse-engineering-proprietary-magstripe-cards
The included video says 2012, but I have a sneaking suspicion it’s actually from around 2000, maybe even the 1990’s.
As for that swipe, why not do the same trick done in so many instances and simply put a roller in the reader to know the speed it’s moving? Although I’m guessing they don’t because back when people in my area still used magnetic swipe cards (seems a million years ago now) I noticed that when it went wrong it was always people trying too hard and either doing it too slow or too ‘precise’ causing variation in speed during the swipe, the readers expected a constant swipe at some decent speed. Oh and of course when the damn reader needed replacing, or the card was worn, but that goes without saying really.
See those things called ‘sentinel bars’? That’s for speed detection.
The reader sits there waiting for a series of on/off pulses of the same length, it then knows to start reading, and uses the width of the pulses as a guide for the rest of the stripe.
Barcodes work exactly the same way (they call them ‘guard bars’).
This product should be in every school
True. You may also find interesting Magnetic Putty and Ferrofluid on youtube
I’ve seen this before using rust. http://www.tetherdcow.com/another-science-experiment/
Pretty cool though. :-).
Used this (or its twin in another brand) years ago with 800BPI and 1600BPI 9 track tape. When a tape got damaged, which happened routinely in a busy shop, especially since the machine room people were often the flunkiest of the flunkies, this glop came out to find the block breaks so the tape could be spliced. Not a desirable circumstance, but sometimes you gotta do what you gotta do. My dealings with it were fixing damaged data tapes from the lab I worked in. A few missing data points weren’t a major issue back then, and was, in fact, to be expected. Beat the heck out of losing the whole tape. After all, a 1200ft reel might have as much as 5MB on it. 1600BPI sometimes went over 10MB, depending on the blocking, which was always a balance– how much do you lose at one shot vs. how much block overhead
A while back I worked for a company that manufactured access control systems that used mag-stripe cards. It’s been a while, so I might be imagining the whole thing, but I seem to vaguely recall there being a spray that makes the encoding visible.
Used it to “develop” IBM mag tape in the 60’s – 80’s to diagnose various tape transport problems – you’d see bit packing if the pinch roller systems failed to speed up the tape to the requisite 75″/sec within 3/8″. One would lift off the magnetic “fingerprint” with transparent adhesive tape, then stick it in the microfiche (always one nearby for the field docs) viewer.
A lot of the old timers on alt.folklore.computers talk about using this on mainframe tapes.
3m made a small device magnetic tape viewer you could just set on the tape and see the lines https://youtu.be/aZOxn8ggX8w