The Internet of Things is going gangbusters, despite no one knowing exactly what it will be used for. There’s more marketing money being thrown at IoT paraphernalia than a new soda from Pepsi. It’s a new technology, and with that comes a few problems: these devices are incredibly insecure, and you only need to look at a few CCTV camera streams available online for proof of that.
The obvious solution to vulnerable Internet of Things things would be to get people to change the login credentials on their devices, but that has proven to be too difficult for most of the population. A better solution, if questionable in its intentions, would be a virus that would close all those open ports on routers, killing Telnet, and reminding users to change their passwords. Symantec has found such a virus. It’s called Wifatch, and it bends the concept of malware into a force for good.
Wifatch is a bit of code that slips through the back door of routers and other IoT devices, closes off Telnet to prevent further infection, and leaves a message telling the owner to change the password and update the device firmware. Wifatch isn’t keeping any secrets, either: most of the code is written in unobfuscated Perl, and there are debug messages that enable easy analysis of the code. This is code that’s meant to be taken apart, and code that includes a comment directed at NSA and FBI agents:
To any NSA and FBI agents reading this: please consider whether defending the US Constitution against all enemies, foreign or domestic, requires you to follow Snowden's example.
Although the designer of Wifatch left all the code out in the open, and is arguably doing good, there is a possible dark side to this white hat virus. Wifatch connects to a peer-to-peer network that is used to distribute threat updates. With backdoors in the code, the author of Wifatch could conceivably turn the entire network of Wifatch-infected devices into a personal botnet.
While Wifatch is easily removed from a router with a simple restart, and re-infection can be prevented by changing the default passwords, this is an interesting case of virtual vigilantism. It may not be the best way to tell people they need to change the password on their router, but it’s hard to argue with results.

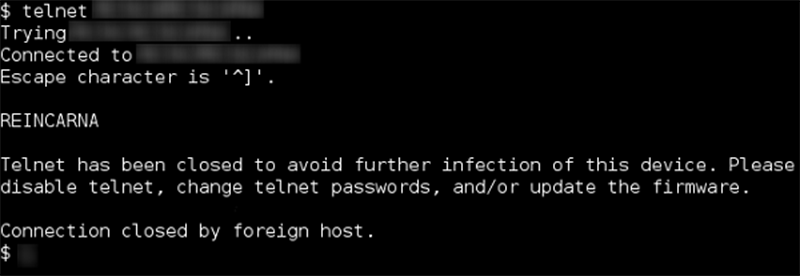















its always fun to ask every employee you meet when paying your bill at your service provider why shh ftp and telnet is open with the ability to change the password removed..the tech support gets red in the and denies it…i just tell them want me to show you….they always just say no
What to do?
wait what???
kinda like when I would scan local ip ranges and if they had unsecured shares I’d either print a message to their printer to secure their network, or put a text file in their startup folder saying the same
Ha! I remember those days, we would go wardriving and print memes for people.
I was taking a Cisco course a long time ago at a community college, and the lab was set up with a bunch of Win2K machines. Cheap to manage for their two admins, but dangerous around a computer science student from the big university (me) who had to take time off for surgery. So one day, while the teacher is talking about how things like echo can work on multi-user systems, broadcasting to all users, I decide to NET SEND * “Like This” into the command prompt I had open (i think I was in a shell on my home machine, so I could read instant messages or something). That really lit up the lab, since it popped open dialog boxes on all the powered on machines in the lab. They were named in order, so when the teacher laughed and asked who sent that NET SEND Lab3PC1 “I did”. I did out myself later and showed the teacher (who was an avowed Unix nerd and hated windows) how it worked, and showed the fellow classmates everything but the wildcard.
Fast forward a few months, and we’re talking with the BoFH there and there is some mention of every computer on the, relatively small, campus getting a “Like This” pop-up window. Turned out every computer, from the lab PCs to the other classrooms, to the administrative machines and the ones that the secretaries used were all on the same workgroup and domain. He had since changed that, but he hadn’t known it was even set up that way since he hadn’t been on the job that long.
He never called me on it directly, even when he took over teaching another Cisco CCNA class the next year. Guess that kinda dates when the classes were, since it was still a general 1st tier CCNA instead of all of the branches they have now.
Hah! I did the same thing to my entire district (apparently) in high school — was sitting at a library computer (that they actually had somewhat locked down) and had just learned net send, and figured out I could still write a batch file in notepad even if I couldn’t directly open the command prompt. Fortunately I only sent a harmless “Hi There” message (thinking it would only go to the rest of the library), and I had previously worked for the network admin, so I just got an “uhh, that went to the whole district, and don’t do that again”
“Net Send” was great fun. Back in high school I wrote a VB app that turned it into a full fledged messenger – initially by looking for the window it popped up, fetching the text, and immediately dismissing it.
I just made a messenger using winsock…
At college I managed to build “write” or “talk” or whatever it was (send text straight to another real TTY terminal with it’s write permission open to you) into a sortof messenger program written in sh.
Also knocked up a nice multi-player game where each player had a ship on screen that had to shoot every other one. Using Curses, and switching from one TTY to the next quickly. Hadn’t figured out inter-process communications yet. Was a bloody good game though!
Simplest solution: No open port on devices that don’t need them.
Why should my car have any access to critical systems that doesn’t involve a direct physical connection? Why should my refrigerator, for gods sake, have a connection at all?
Forget security through obscurity. Forget security through algorithmic finesse. How about security through no damn way to connect?
Honestly, is it that difficult to flip a light switch? Does a 2W LED on the front stairs and another at the door take so much power that a net-connected light is needed? The standby on the net connected unit is more than the basic always on takes.
Is it that difficult to get up and walk to the television? Young people these days, getting too lazy to change the channel the normal way.
Not the point. Why did my last rental car allow connections to the CAN bus via the entertainment system bluetooth? There is no way to make this secure. None. The entertainment system has no business being connected to the same bus that the engine controls are on at all. This connection provides no benefit at all, and leaves a wide open security hole. My own vehicle does not have this, as it is too old, but my next one likely will, due to lazy design and a vague feeling that more connectivity is automatically a good thing, and I will have no practical way to secure the system.
In many cases we have gone well past the balance of benefits vs drawbacks, and this has been known for years in both the energy community and in the security community, and the failures in each are often sold due to arguments in favour of the other. The end result is both insecure and energy inefficient.
The answer is simple: The US government wants a way to remotely disable cars of fleeing criminals. They forgot that back doors don’t know good guys from bad.
It’s part of their secret project to put a snarky AI into a Trans Am and give that car the ability to jam other vehicles as well as drive itself and jump off ramps really well.
If only somebody was to fuck with that, it might bring some consumer awareness. Almost nobody’s aware of it, horrifying as it is.
It’s utterly easy to build a little Bluetooth whatsit, give it a list of default login methods, and get it to do something non-fatal but noticable to cars. Say, flash the lights, and announce over the CD player’s display “I could override the brakes if I wanted to”. One could plant these next to busy roads, programmed to go off randomly, keeping quiet the rest of the time.
Of course if you did this, YOU’D be seen as the criminal / terrorist (face it!), and the person irresponsibly risking lives. But it only needs to get the attention of a journalist. Assuming there are any journalists left. The Volkswagen thing is still news, news stations like a followup. It’s sort of like the “big lie” though, such a huge problem that everyone would rather ignore it.
No benefit? It’s there to allow speed-dependent volume control…
“no reason” except for that fancy radio that passes controls through the steering wheel and that shows the radio Id info in the display in dash. A controller area network is not itself the issue the issue is the manufacturers not including enough abstraction. People want the functions so oem will sell them
No, they could easily just have 2 separate CAN networks, one for anything important and life-threatening, one for everything else. Putting vital control and engine signals onto a bus with fucking BLUETOOTH access is just unbelievable. For the price of a bit of copper wire.
It’s literally a deathtrap waiting to happen.
Modern TVs don’t have the interface. You can’t pick from 100 channels using the CH + / – buttons, usually tiny little buttons hidden on the side of the set, with their tiny markings embossed, black-on-black, into the casing. They stopped putting proper controls on TVs years ago. It’s the remote or nothing.
Good side is, you can’t lose the remote, because as soon as it goes missing, you look for it!
Exactly. IOT devices do not have to be on the internet directly without routing and firewalling, put them behind a router and have them connect out.
I have 12 IP cameras that have login as “root” and “password” as the password. and they are 100% unhackable by the world’s best hackers because they are all on a private network with the recorder. You do not need DOD level of security on private air-gapped lans.
Nobody is going to try and infect all my USB drives with a specialized QNX virus to infect the recorder via sneakernet.
I hope that’s a wired network. Because otherwise, just give me directions to some place near you and we’ll see whether I’m better than, as you put it, the worlds best hacker.
I used to preface this statement with “or WPA2-RADIUS” but it seems that’s been busted up in recent years too.
> WPA2-RADIUS”
was it? afaik state of the art is offline dictionary brute force attacks
I think is something about sending deauthentication comand and then recording the heandshake.
With that information you can guess all but 56bits of 256bit code, which is brutforcable in less then a day.
Even less if you upload recorded heandshake here https://www.cloudcracker.com/
“The standby on the net connected unit is more than the basic always on takes.” A μC uses more than 2 W on standby?
A μC that has to run an entire TCP-IP stack and possibly a mini-webserver, on top of that wifi…
The people on HaD have great benefit from their devices allowing access, the same for people who wish to root their bought devices to remove spyware or add functionality.
That stuff might have holes either from dumbness, or more likely to assist the NSA and their ilk, but it can help us too in plenty of cases.
Hell I bet sometimes it’s done by the low level coders to help people not being completely controlled by the parent company.
Never ask for perfect security and control before thinking it over and thinking about what that will mean.
Let the air gap rule! And close those wifi ports as well.
Yes, the purpose in this case is for good, however now all the script kiddies in the world can see it and change it easily to do bad.
May have been better to properly obfuscate the code.
Better idea still is to get the manufacturers to REQUIRE YOU TO BE SECURE. What’s so hard about requiring a wifi router to have its password changed because it actually, you know, wifis?
This doesn’t give them anything more than they already had with the thousands of pieces of malware already available that makes it trivially easy. Especially for a script kiddie – they won’t bother figuring out how to add their own payload to this when they can just grab one off the shelf.
Wasn’t Robert Tappan Morris’ original Internet worm originally supposed to patch up a lot of the security holes, the same ones it used to gain access ? I believe him when he says that it was an internal program that escaped before he could finish it.
A parasite which tries to eliminate competition is not necessarily benevolent or even benign to the host.
A parasite that improves your immune system then immediately dies can’t be so bad. Until someone downloads the source and puts a different payload on it. But there’s been virus construction kits for skiddies for years now, so that’s nothing new.
My first two roommates had terrible IRL security. We lived in a crappy neighborhood and they’d constantly leave the house with the windows open or the door unlocked. One night I came home to an empty house with all the lights on and the front windows open. My guitar was sitting on the couch in plain sight. I picked up an ashtray stand, threw it through the screen and climbed inside. I went room to room removing everything of value, hid it in the shed out back and sat on the porch waiting for the roommates to return. I let them go for almost an hour thinking we’d been robbed before finally telling them that their stuff was in the shed and I did it to teach them a lesson. They were pissed at me for days but they never left the windows open again.
This virus is the virtual version of that. I like it.
Did you pay for the replacement of the screen?
So a thoughtless, perhaps even rude action, but one devoid of malicious intent on their part excuses a decidedly malicious one on yours. I don’t think I would care to live with either of you, but if I had to pick, I know which I would choose.
I have no less enmity towards the creator of this malware than I would to the creator of any malware.
Where was the malice in his action? He didn’t do it to screw over his roommates, he did it to correct their behaviour before it *actually* resulted in them losing their property in a legitimate robbery.
Exactly ‘hey close the windows and lock them when you leave’. After the 3rd or 4th time I probably would do the same. They were being the rude ones.
you sound as good as this retarded four http://www.usatoday.com/story/news/nation/2015/02/05/sheriff-boy-kidnapped-to-teach-him-a-lesson/22961305/
Wow. That sheriff’s head looks to be about the same size and mass as a 1980’s vintage 24″ CRT monitor.
If you can access a CCTV camera from the internet that means it isn’t a CCTV camera, CC means closed circuit meaning it isn’t connected to anything outside of its recorder and a few monitors.
The term was coined when the alternative was a camera connected to a TV broadcast network. Back then video cameras were really, really rare.
Certainly a different take on/use for malware. I wonder if those that weren’t tech savvy enough to change it in the first place though will even understand the message?
This is textbook grey hat. Not white hat.
Who would of thought batch/shell level coding tasks would make security headlines? The power of marketing..
“unobfuscated Perl”
Is there such a thing?
Sorry I have to laugh when HaD busts its guts for months to get us all on the IoT idiot bus and then remembers it is stupid. If you don’t have enough time to manage your food supplies, your life has some serious priority problems. Own your possessions, don’t let them own you.
@wayward oak
Just because you can doesn’t mean you should have to.
Just because you choose not to doesn’t mean you can’t.
Why can’t these companies who manufacture routers & modems just create truly random login & passwords credentials for each device, and stamp that information on the label where the serial number is located? It’s not the best solution, but it would make it very difficult for a hacker to remotely gain access to the device without having physical access to it; plus the owner has the ability to change those credentials.
They are starting to do that. My current wireless printer and ISP wireless router both have somewhat random initial passwords tied to the hardware IDs, serial number for my printer and WPS PIN for my router. Hopefully we’ll see them continuing in that direction in the future.
And of course the passwords can be changed, at least for my router. In fact it reminds you every time you log into its admin panel to change the password, until it’s finally changed.