Passwords are crap. Nobody picks good ones, when they do they re-use them across sites, and if you use even a trustworthy password manager, they’ll get hacked too. But you know what’s worse than a password? A fingerprint. Fingerprints have enough problems with them that they should never be used anywhere a password would be.
Passwords are supposed to be secret, like the name of your childhood pet. In contrast, you carry your fingers around with you out in the open nearly everywhere you go. Passwords also need to be revocable. In the case that your password does get revealed, it’s great to be able to simply pick another one. You don’t want to have to revoke your fingers. Finally, and this is the kicker, you want your password to be hashable, in order to protect the password database itself from theft.
In the rest of the article, I’ll make each of these three cases, and hopefully convince you that using fingerprints in place of a password is even more broken than using a password in the first place. (You listening Apple and Google? No, I didn’t think you were.)
Fingerprints are not secret
The first, and maybe most obvious, problem with using a fingerprint in place of a secret password is that they’re not secret at all. Think about the trope where the cops offer the bad guy a coffee in questioning and then subsequently take the mug down to the forensics lab to read his prints. Busted!
But it’s worse than that. You leave your fingerprints everywhere. They can be picked up off of paper, keyboards, and desk surfaces. You wouldn’t leave your password written down on a sticky-note attached to your monitor at work, would you? If your work is using your fingerprint for authentication, your password is probably on your monitor right now.
 German hacker [Jan Krissler], who goes by [starbug], has been hammering this home every chance he gets. Back when the iPhone 5’s touchID system was just announced, [starbug] started salivating. He bought one immediately, played around with it for two days, and demonstrated that he could fake out the fingerprint reader before the lines around the block at the Apple Store had cleared. In this interview with Ars Technica, starbug complains that it was too easy. An unnamed Apple source said they’d expected it to take two months, not two days.
German hacker [Jan Krissler], who goes by [starbug], has been hammering this home every chance he gets. Back when the iPhone 5’s touchID system was just announced, [starbug] started salivating. He bought one immediately, played around with it for two days, and demonstrated that he could fake out the fingerprint reader before the lines around the block at the Apple Store had cleared. In this interview with Ars Technica, starbug complains that it was too easy. An unnamed Apple source said they’d expected it to take two months, not two days.
How to Mimic a Fingerprint
His technique to mimic a fingerprint is pretty simpel. He takes a copy of a fingerprint, then etches it into copper (as if making a PCB), coats the etching in graphite spray, and finally tops it all off with a layer of wood glue or latex. Where the copper was etched away, the glue-and-graphite finger mold is deeper, simulating the ridges on your finger. The graphite spray gives it the right bulk capacitance. Do this in skin-colored latex, and you’ve made something worthy of Mission Impossible for $5 in materials and one afternoon of your time. All you need is a good fingerprint image lifted from a mug or a book.
Lift Fingerprints from Photos
Don’t show your prints in pictures. [Starbug] reproduced the thumbprint of [Ursula von der Leyen], Germany’ Defense Minister, from a single photograph taken at a press conference. Whether the thumbprint is good enough to unlock the entire German army remains untested, but you get the point; hopefully they’re not using fingerprints for secret passwords.
[Starbug] discusses the resolutions required and many more hacks against biometrics in general in this great talk at the Chaos Communication Congress (in German), but the point is that with enough resolution and/or a good enough lens, fingerprints can be taken from comfortable distances. The main limiting factors are depth-of-focus and lighting, which is bad news for politicians sitting on a well-lit stage in front a bunch of cameras. Politician or not, unless you’re always wearing gloves, your fingerprints are not good secrets.
Fingerprints are not revocable
So let’s say that somehow your normal password gets leaked. How bad is it? In an ideal world, the website that has been hacked lets you know and tells you to change your password. You replace your dog’s name with your cat’s name, and the year of your birth with that of your kid sister’s. Problem solved!
But if your fingerprints are your password and they get leaked, it’s “impossible” to change them. Indeed in traditional fingerprint applications, uniqueness and immutability are the whole point — tying criminals to the scene of the crime, for instance. If you could just change your fingerprints after each heist, you wouldn’t have to wear those awkward gloves.
A fingerprint stays with you for life. Once I steal your fingerprint, I can unlock your current fingerprint-secured device and every fingerprint-secured device that you’ll ever buy in the future. Fingerprints are half-secrets that can’t ever be changed, and thus make lousy passwords. There’s not much more to say about this point, and it’s pretty damning, but it’s worth emphasizing because of the prevalence of bad policy out there.
 For instance, sensitive government agencies have been using personal identity verification (PIV) cards that include a copy of the employee’s fingerprint. In addition to a correct password, federal employees subject to PIV have to swipe their finger, and the fingerprint is compared against the one stored in the card. The idea is to use the password and fingerprint match as a form of two-factor authentication.
For instance, sensitive government agencies have been using personal identity verification (PIV) cards that include a copy of the employee’s fingerprint. In addition to a correct password, federal employees subject to PIV have to swipe their finger, and the fingerprint is compared against the one stored in the card. The idea is to use the password and fingerprint match as a form of two-factor authentication.
And then the US Office of Personnel Management (OPM) got hacked and 5.6 million (!) fingerprints of government employees got taken, presumably by a foreign government’s spy agency. So now the Dept. of Homeland Security is possibly going to have to move to “three-factor authentication” because one of their factors is entirely burned. If the government had chosen a revocable second factor for the PIV cards, at least that part of the spill would be a lot easier to mop up.
Passwords need to be changed to remain secret and secure. Fingerprints don’t change.
Fingerprints are not hashable
The problem with fingerprints is that close is good enough, and needs to be. If I press my finger harder into one reader than into another, or swipe differently, or have a cut, I still want the reader to accept my fingerprint. Trained FBI agents make matches with “partials” all the time, and with reasonable accuracy. Close matches are a fact of life with human flesh and real-world scanners. But a fingerprint with a tiny flaw will hash into something entirely different from the reference version. What this means is that fingerprints are not hashable. Hashing makes passwords strong and without it, fingerprint protection is much weaker.
When a responsible website gets hacked these days, and the thieves walk away with the password database, they’re not actually in possession of a list of any passwords at all. Instead, what they get is a list of usernames and one-way hashes of the passwords.
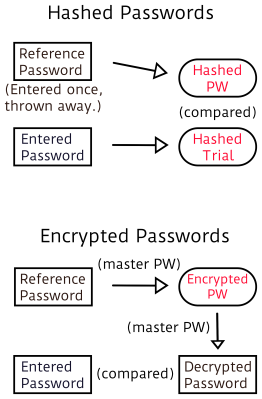 When you type your password in, the website hashes the result. If the trial hash matches the stored one, they can be sure that the password was right. Because the hash is essentially one-way, it’s exceptionally hard for anyone to start from the hashes and figure out what your password is. In fact, the easiest way to go from hashes back to passwords is to start guessing every possible password, compute its hash, and check for a match.
When you type your password in, the website hashes the result. If the trial hash matches the stored one, they can be sure that the password was right. Because the hash is essentially one-way, it’s exceptionally hard for anyone to start from the hashes and figure out what your password is. In fact, the easiest way to go from hashes back to passwords is to start guessing every possible password, compute its hash, and check for a match.
Contrast this with a naïve implementation where the website stores everyone’s passwords, but encrypts them with a master password. If the hacker can break the master password, he or she can decrypt the entire database and all of the passwords. And because this master password has to be used every time a normal password is validated, it’s going to be very vulnerable as well as very valuable. Encrypting each user’s data with a different master password just means that they’ve got to maintain a gigantic master password database, which doesn’t help things either. This is why every responsible website only stores hashes of users’ passwords.
Hashes can be made still better than encryption, though. If the security people are doing their job, the passwords are salted with something that’s different (but not necessarily secret) for each user before hashing; this slows down a brute-force mass-cracking attempt, because each person’s password is essentially hashed differently.
If you and I both use the password “!password123”, but my password has “elliot” added on the front and yours has “joe_user” our hashed values will differ. Once the hackers finally guess your password, because of the salt, they won’t automatically know mine.
And if the website’s security is really good, this hashing process will be repeated thousands of times with a slower algorithm which further slows down brute-force attacks. If it takes one half second to validate your login, it’s no big deal for you, but it’s a deal breaker for a brute-force attempt where they rely on millions of trials per second. As an example of best practices, the disclosure when the password manager LastPass got hacked is pretty solid. It’s still lousy that they got hacked, and you should still change your master password, but if it’s a good one nobody is going to be brute-forcing it any time soon.
Fingerprints and the Avalanche Effect
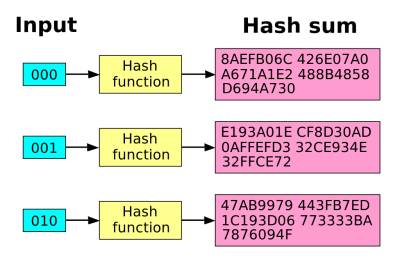 What does any of this have to do with fingerprints? Fingerprints don’t hash well, so all of the above security advantages of storing only salted, hashed passwords in the database don’t apply. That’s because in addition to being one-way, a good hash exhibits the avalanche effect: a small change in the password makes a much larger difference in the hash.
What does any of this have to do with fingerprints? Fingerprints don’t hash well, so all of the above security advantages of storing only salted, hashed passwords in the database don’t apply. That’s because in addition to being one-way, a good hash exhibits the avalanche effect: a small change in the password makes a much larger difference in the hash.
The string “!password123” hashed using the MD5 hashing function is b3a2efccbe10c39f2119979a6f9a3ab2, but “!Password123” is d2583f9c75fbc22890d39e7241927511. The two strings differ by one letter, the capitalized “P”, and yet the hashes are very different. This prevents the cracker, who is brute-forcing potential passwords to get a hash match, from knowing when he or she is getting close. If each correct letter in your password got the hash closer to the target hash, they’d guess it in no time. The avalanche effect means that guessing “close” to the password doesn’t help at all.
As I mentioned before, fingerprint technology needs to be “close enough”. A miss is as good as a mile once it’s hashed. Which means that fingerprints have to be stored in plaintext or encrypted but can’t usefully be hashed, because a good hash avalanches. Fingerprint databases are necessarily a weak link; anywhere your fingerprint is being stored, on your iPhone or PIV card or inside your electronic passport, there is a version of your fingerprint that someone could decrypt if they knew the master password.
Electronic Passports
A great example of hashing versus encryption is found in electronic passports. They contain an encrypted representation of your fingerprint and iris images because they’re considered to be sensitive information. But these can only be encrypted because the passport reader will need to be able to decrypt them to compare with your real fingers and eyes.
 On top of this, all of your non-sensitive information and the encrypted package are all hashed together, which makes it harder to tamper with any of the info without changing the hash. You might think you could tweak one bit here and apply an offsetting tweak there, but the avalanche effect foils that plan.
On top of this, all of your non-sensitive information and the encrypted package are all hashed together, which makes it harder to tamper with any of the info without changing the hash. You might think you could tweak one bit here and apply an offsetting tweak there, but the avalanche effect foils that plan.
At the end of the day, though, this means that the fingerprints on your passport are only secured from reading by encryption, and not a hash function. That’s fine for Customs because they only care that your fingerprint hasn’t been modified. For them your fingerprint is only really used to verify that you are you, and that’s hard to tamper with without breaking the hash that ties it to the rest of your information.
For privacy-minded individuals, on the other hand, it’s a bit more of a concern to have your fingerprints only encrypted. An evil-doer with your passport and the right password(s) could undo the encryption and get your fingerprints out. Although it’s probably easier to just lift your prints off the cover of the passport — fingerprints aren’t good secrets, remember?
Conclusion
Don’t use fingerprints as if they were passwords. Being permanent and relatively-easily verified and obtained makes them great for criminal investigations or for certifying that you are who you say you are. But they’re not passwords because they’re not secret, they’re not revocable, and they’re very difficult to store securely.

















Right on! I’ve been telling the same story for a couple years, and people treat me like I called their baby ugly. Biometrics are terrible passwords, iris scans, fingerprints, dna, etc. Don’t let someone store that for you and assume it is “unhackable”.
I have a Microsoft Fingerprint reader sitting around here somewhere. Got it cheap on clearance and they orphaned it, so it was only ever 32-bit compatible.
The real kicker though?
The included documentation stated that it was not to be used as a security measure because the fingerprints scans were stored and/or transmitted with ZERO encryption. Of course, if you installed the software without reading this warning, you would likely be using your unsecured insecure fingerprint to log onto your PC instead of a password.
They certainly aren’t unhackable. But the security of passwords – as implemented by real people – is much worse. I don’t see that we are going to improve how the population uses passwords, so we need to improve biometric security instead.
Dit you read the article?
Because of their convenience, there is a move towards biometrics as a substitute for passwords. As shown by the OPM example, they are completely unsuitable for this. Thank God that the OPM used them only as a secondary security measure, otherwise the US government would have been completely owned by now.
Biometrics are ONLY suitable to indicate (not prove) that a certain person was at a certain location at a certain time.
In the future, all biometric details a person has ever stored somewhere will be for sale in cracker circles, and can be used to unlock all services that rely on such details.
Proper security is a thing you know and a thing you have. Good security is a thing you know, a thing you have, and a user chosen biometric. If it’s always your thumb then it is a failure, let me use my nose print or big toe.
Sadly nobody does good security.
MY nose doesn’t have enough ridges….
Try some more private part of your anatomy. I’m pretty sure it gets enough ridges.
Most workplaces would probably frown on their employees whipping it out whenever they need to authenticate. Probably not a practical solution in most cases.
In addition to being gender exclusive.
Harold didn’t get the memo on beaver tracks.
nipple?
Tried my toes on a fingerprint scanner on a laptop. Works like a charm ! Pretty weird to unlock my computer at work with my feet.
That would mitigate the photograph method. Your feed ARE covered most of the time, unlike fingers. Maybe if somebody breaks into your house and finds toe prints in the bathroom’s tile floor …
FWIW, the finger print authentication done on smartphones is entirely local. The data is stored in a specific chip that does the comparison and presumable would not willingly read it back out. Even when combined with online accounts, you authenticate with your password once, and the fingerprint chip stores a some type of token that it uses once the FP is locally verified.
Sure it’s not super secure, but it does require knowledge of your FP and physical access to the device in question. So if your phone is stolen it is more secure than leaving it unprotected. I stopped using it on my phone because it was a pain in the but, and if you had 3 missed swipes you had to wait a minute to try again. Unlike the Iphone, mine is swipe style, so slightly harder to just lift a print off the button. And if you pick a finger you normally wouldn’t touch the phone with, even harder.
I’m with you on weak security. The pattern lock on Android phones is weak security. Careful study of the oil on the screen will probably let someone unlock your phone. The point is to be secure long enough for you to notice the phone is missing and change all of your account credentials. Fingerprint will be nearly as good for this.
That said, I don’t allow my important accounts to log-on automatically with my unlocked phone. I still need to enter the passwords for banking, etc. This way the screen lock is good enough. My fear is that people will make fingerprint protection their go-to for banking and password safes. That’s a definite step backward in my opinion.
You might be interested to know that some Android versions have the option of scrambling the location of the numbers on the screen to make each unlock different. It makes it difficult for someone to guess your code from finger movements. They need to be able to see the screen too.
Really? Haven’t seen that. It’s a nice feature. I always thought that ATMs should deploy something similar – but then it’d probably trick people.
Yes, cyanogenmod has this feature. I use it and think that it should be enabled by default.
http://www.naldotech.com/scramble-pin-layout-cyanogenmod-11/
Maybe it is just Urban Legend, but I read on Facebook (that pinnacle of accuracy) that police can require a person to unlock their phone if it’s fingerprint protected, but need a search warrant if it is password protected.
They can and do require fingerprinting easily. To create a fake finger print impression is trivial. So while you may choose not to and fight to not to give over the information that is your password, your finger print is a forgone conclusion.
There are DIFFERENT levels of warrants. IE the police CAN do a search and seizure in a BANK. BUT CAN NOT open safety deposit boxes…
http://www.justice.gov/sites/default/files/criminal-ccips/legacy/2015/01/14/ssmanual2009.pdf
Overall “Forced to Unlock”? FALSE! If I am a CEO with patents or schematics on my phone. You’d need a Superior court judge for the warrant.
Repeat after me “I will only speak with and comply with my attorney present.”
Here is the ugliest truth, A police officer or any other federal agent may NOT EVER testify on YOUR BEHALF or serve as Character witness.
Word. Fingerprints for phones are fine by me too, honestly. But then I leave my phone unlocked.
But an unlock pattern is not a PIN, and a PIN is not a password. And fingerprints fall on that continuum somewhere around PINs, I think?
You’re right, but fingerprints are still better than passwords for two major reasons:
1. They’re easier to use
2. When people are told to choose passwords, they largely choose GOD AWFUL passwords
It’s still way easier for someone to guess a terrible password than it is for someone to fake a fingerprint. And using fingerprints means that your adversary has to be physically near to you to capitalize on the compromise. Passwords allow your adversary to be anywhere in the physical world while still being digitally “near” you and the resources they intend to compromise.
Bottom line: I believe fingerprints still offer more security than insecurity _for_the_average_user_. If your adversary is the type of person that’s going to take the time to fake your fingerprint, they’ll probably find some other hole in your opsec to exploit when you stop using your fingerprint.
There is a simple solution for average person: hardware password manager. USB stick which mimics HID keyboard, and has your passwords. Most versions can generate a crazy password as you don’t need to remember it.
Hackaday features those on a regular basis. Even one of the regular columnist made it – https://hackaday.io/project/5588-hardware-password-manager
A better solution would be Mooltipass, but an average person doesn’t loose their keys easily, so they wouldn’t lose their simple online key :)
Wow, I didn’t know it, it’s very similar to a project me and a friend are working on:
https://hackaday.io/project/8342-memtype
Ours is much simpler, cheaper, and some added functions, like encryption and a PIN unlock, also typing not only the password but also the user, changing from user to password field and submitting it all without you having to touch the keyboard at all!! Also each user/password has a name, so it list the name before you apply it. Also not a limited number of passwords, it stores them encrypted in a dynamic structure :)
Anyone with visibility of the usb bus could still instantly sniff that though.
Anyone with visibility of the USB bus can put a real keylogger between the keyboard and the computer. We’re talking about an average person which uses lousy passwords. Using a hardware password manager average person can add additional “salt” sequence to protect their passwords
2 factor still moar better.
That is kind of ridiculous logic, the truth is that given my want to get into your phone (even from a solo attacker vs state attacker) I can guarantee gaining access were you to use a fingerprint, whereas if you used a password or pin I can not guarantee access. Sure, people may use trivial passwords — but even in that case brute forcing that password is much more work than lifting your prints (with or without your knowledge).
Question for reason 1: why do you lock your car/house? Much easier to operate to leave is unlocked or in case of the house even without door (much easier to enter when hands full.)
As to reaseon 1+2 are for me reasons to not let people use things that require security, because these 2 demants clearly show that said person has non knowledge ans awareness for using these devices…
actually, a fingerprint, and many other biometrics ARE revokable AND hashable. you should never use the entirety of any biometric as the “passphrase”, you select a subset (based on a reliably reusable algorithm) and hash that subset of values.
How much entropy is in one fingerprint? (PS. I am genuinely asking)
Are there any “reliably reusable algorithms” for selecting a subset of biometric information? Won’t this have the same problem as hashing biometrics?
To that would get around the issue of stolen encrypted biometrics. But Once an attacker has a good copy of the entire fingerprint that breaks any ability to change what part of it you are using unless you change fingers, etc.
Lifting a copy of the fingerprint is not enough for the latest generation of fingerprint readers. These new readers are ultrasonic and read the internal physical structure of your finger including blood veins, bone and muscle tissue.
https://www.qualcomm.com/products/snapdragon/security/sense-id
It seems that the Henry Classification System (a number system for storing and comparing fingerprints) is easily hashable and real-world comparable.
Are they really fingerprint readers at that point?
I was looking for examples when writing the article, but couldn’t find any. It _is_ entirely possible to imagine some feature extraction technique that would allow hashing and still work with smudgy fingerprints, but I couldn’t find one in the wild.
Do you have a cite? I’d love to add it to the article.
The answer to “how much entropy” is “how microscopically are you looking?” In real-world crime scene prints, there’s often not much info b/c prints are smudged or partial or whatever. You’re limited by the resolution of the capture device and the tolerance for false negatives, and these are variable.
one example using eye features
https://patents.google.com/patent/US20140270405A1/en
the extraction method it’s self can in theory be included in the pass/fail metric.. and is NO substitute for proper liveness testing. that is a different line of biometrics that is focused on the actual spoofing. but revocability is the first step in avoiding a purely digital attack method. (ie spoofing the reader instead of the user)
Totally agree. I do agree with the convenience of fingerprint unlock on devices but this should be treated as a Valet key. or a Visitor badge. It will let you in the front door but if you want to do more (change settings or enter higher security areas) prepare to fully verify your identity with a PIN or password. (get it wrong the print access gets revoked, but can be reset with the Main Long Password). Tiered access is the best mix of convenience but still restricting access to impersonators.
Inre: Valet key.
Other than having the convenience of remote “Unlock, Lock, Trunk Unlock, and Panic” buttons on the main key, I’ve done well using the Valet Key. It will still lock/unlock doors (manually) start the car and drive 85 mph.,,
I understand that some “high end” cars do limit speed and engine RPM with the valet key, but not with our car.
Historically, most “Valet” keys would only work for the side doors and ignition, and would not allow for access to the glove compartment or the trunk. Of course, this type was usually back in the 80s and 90s when every door, trunk, and glovebox had a mechanical, key-operated latch on it.
Six Flags theme park uses finger print scanning to validate season pass holders entering their parks (they don’t scan those under a certain age which is not 18 interestingly enough). I seriously don’t think their security is anywhere near as hardened as say… the FBI.
But if theft of fingerprints is such a concern then where does IAFIS and NGIS come into the mix? Those databases hold, not only criminals fingerprints, but also military and federal employees.
IAFIS & NGIS are used for IDentity, not Authentication.
simpel?
This is nothing new: The science fiction writer Mack Reynolds [1917-1983] worried about this many years ago – and had a character in one of his stories ‘break’ a debit card setup with a photograph of the finger about 30 or 40 years ago –
My fear, how easy it is to print your finger print at the scene of a crime. Malware that could harvest your finger print data from anywhere in the world off your internet connected device… Now that is some scary s#!t right there.
I don’t think the unhashable part of this is completely true. Although I do not completely understand them (haven’t had time to read enough about them) perceptual hashes are used to identify music in services like Shazam. So if a hash can be applied to something as changing as music, it should be possible to create an equivalent perceptual hash of a thumbprint. Does anyone more knowledgable on this subject care to discuss?
My take is that the hashes are being used for different purposes. A hash that hints at any partial features of the source would allow cracking or searching in stages. Shazam wants to recover musical detail to match with other examples. That is to say they want hashes that will match musical features when they search.
Password hashes are used for exactly the opposite reason. They want the hash to say NOTHING about any part of the password apart from being a one way function of the whole password. This leaves trial and error the only method for cracking it (viewed on it’s own).
You could certainly make a hash for a fingerprint, but for it to be useful it would have to throw away a lot of data or arrange it tree like so finer detail can be matched on a partial basis. This would make it much easier to reverse engineer a synthetic fingerprint that would match the hash as well or better than the users own.
I swear that when I woke up this morning I thought deeply about how insecure fingerprints were for the exact same reasons mentionned above. Imagine my amazement when I saw a hackaday post about the same subject when I came back from school ! :D
Simpel!
You talk in your sleep, your Android phone recorded your speech, and sent it to HaD’s Tip Line.
B^)
It was a few years back when I had my course in human computer interaction but I still remember there were algorithms/methods for extraction of some distinctive features from images of fingerprints and storing those in a way that it its possible to verify if a finger matches the stored data but it is impossible to recreate an image from the data. This can be thought of as hashing of sort.
From Apple.com:
“Touch ID then intelligently analyzes this information with a remarkable degree of detail and precision. It categorizes your fingerprint as one of three basic types—arch, loop, or whorl. It also maps out individual details in the ridges that are smaller than the human eye can see and even inspects minor variations in ridge direction caused by pores and edge structures.”
(see https://support.apple.com/en-us/HT204587) Granted, there is a lot of marketing there, but then, there is this form Tested.com: https://youtu.be/2u4ZLGsw1zo
From what I understand, there are SOME fingerprint scanners that “reads” deeper than the skin, making it harder to duplicate.
For most cases, I’d rather have TouchID than a PIN password. I figure that if someone has the resources to successfully duplicate my fingerprint AND is able to access AND unlock my device AND find the sensitive information, I would be vulnerable anyways.
Spoofing fingerprints seem to be way to easy to do on (presumably) most devices.
I had a big aha moment when I saw Adam and Jamie use Grant’s fingerprint in a Mythbusters episode some years ago. After succeeding with all variants, one of them using a print lifted from a CD, they actually succeeded also when trying with a laser printed fingerprint that they licked.
https://www.youtube.com/watch?v=8Wsc8fnf-aM
For those interested: http://www.cedar.buffalo.edu/~govind/fingerprint_hash_icapr05_ver2.pdf details a method to hash fingerprints.
The problem looks to me like its similar to google goggles being able to detect an Eiffeltower in a picture you take with a phone at a non specfic angle and distance. The trick there is to convert the edges into a normalized vector representation which can then be found by searching for its hash value.
Thank you! That paper’s very interesting.
Instead of considering the whole fingerprint, they take groups of three features at a time, and hash those. The result is many, many hashed sub-groups of features per fingerprint. They then compare all of those hashes with the hashes from target print, and if “enough” of the sub-sections match, they call it a match.
Their procedure has strictly less (statistical) power than the baseline “plain matching” strategy, but they think that the extra classification errors may be worth the security tradeoff. I’m sure there are applications where that is true.
Cool stuff. It’s an obviously important area for academic research, so it’s good to see people working on it.
The fingerprint is obviously stored as a digital file, likely a number, and so it’s already hashable.
And they now make sensors that scan the vein structure of the finger rather than the fingerprint.
Either way, I want there to be uncertainty and want to be able to have someone else to use things on my behalf if I wish to, so I’m still against it.
Yes, a fingerprint is hashable. However, the hash is useless (with any hashing function *I* know of, anyways) because the finger print must be EXACTLY the same to get the same hash — that’s how all (that I know of) hashes work, tiny differences in input make a HUGE difference on the output. You need a way to read a fingerprint EXACTLY the same, time after time (and what about if you get a cut?!?)
What if you get a cut (or your finger is slightly off-center)? Well it’s actually good practice to change your password once in a while :)
People forget their passwords all the time and you have to make a new one, and a new hash obviously. That’s part of the password system. Even with RSA keyfobs people lose them or the system gets hacked (remember that incident?) and you need to get new passwords/keys.
And talking of which, perhaps more security systems should allow people to have a separate reset password that they can store in a safe place so they can fix issues when they occur. But please companies, fuck off with asking me to enter my phonenumber.
And incidentally, most all fingerprint systems just take the fingerprint and greatly simplify the information, specifically since they don’t want to go nuts with analyzing and getting confused by small errors. Plus it’s the curves and some key features that are the difference between people, not every tiny line.
I’ve always wished there was an option in iOS to use BOTH fingerprint and password. I use the fingerprint because it’s easy, but really want the security of the two methods combined.
Yeah, the problem is that they’re not willing to guarantee that Touch ID is 100% reliable to the point of letting you require it without a passcode fallback, and even if they were, it’s a bad idea — what if for some emergency reason you need someone else to be able to get into your phone? What if you’ve injured your finger/hand? What if you drop the phone and somehow break the sensor? Nearly every biometric system I’ve seen has some way to override/bypass it in the event of malfunction, whether that’s a password alternative, or an administrator/manager override, or (in the case of access control, passport control, etc) a lane/window/desk where a human can identify you and let you in.
I’ve actually seen a fingerprint reader that uses hashes… like one would expect, it cant work if you want a perfect match, but a high percentage…
Granted, this was not a security application, just a work attendance system.
I’m still stumped, how can a hash be of *any use at all* without a perfect match?!
It all depends on the method you choose….they used the hash (I haven’t seen any source code, so it’s entirely possible that “hash” is not necessarily an actual hash, it’s what they sold it as) to prevent reconstruction of the fingerprint from the system.
Many combined hashes for one fingerpint. Then a partial hash match is sufficient and can be statistically constrained..
I love my iPhone6+.
The fingerprint to log in is the best thing ever!
Before I disabled the login 4 digit number because it was a PITA to me.
Sure it might be hackable, but how long will it take the crooks who steal my iPhone to hack into it. Meanwhile I can block/clear my iPhone or my credit cards, etc.
Nothing is going to be secure, but this way sure makes it easy, and it harder to hack than some other thing.
I’m curious how the fingerprint reader on my Galaxy S5 works, It looks like a loop of metal. Does it read the vibrations of the fingerprint as it is swiped across? Does it read capacitance of the undulating ridges? Ink wiring mimes Juan two no!
I don’t know about Samsung’s version, but the metal is probably either cosmetic, or just a capacitive sensor used to activate the fingerprint sensing. At least Touch ID works like that — the home button is a touch-style fingerprint sensor, and it’s surrounded by a capacitive metal ring that signals the fingerprint sensor to activate.
The ring on the iPhone isn’t used for activation. It’s used to transmit a signal into your finger which is sensed by the silicon under the sapphire glass. The s5 has a capacitive swipe sensor. The ring is purely cosmetic on the s5.
What is a “good” way to “Conceal Carry” a bunch of passords needed for various websites/terminals?
I like the idea of Mooltipass, but not the price…
I carry a file of passwords/logins/websites in an encrypted .ods file on a flash drive, but MS Office refuses to open the file.
(and a lot of “public” terminals have USB openings blocked).
typo:
How to Mimic a Fingerprint
His technique to mimic a fingerprint is pretty simpel. … “simple”
http://cdn.overclock.net/8/80/500x1000px-LL-806a7344_mib_fingerprint.png
What were you saying? I couldn’t hear you over my own screaming.
Excellent article! I’ve worked in the past on technology to confirm a person’s identity by taking their fingerprint via their phone camera, and you’re right: fingerprints are OK as a “something you have”, but not as “something you know” or even “something you are” since they can be spoofed. However, as an element of 2-factor authentication they can be useful.
Agreed! Excellent article! Thank you.
Biometrics are great for IDentity… not so good, as implemented by most, for Authentication. It is important to know the difference between these.
Biometrics ARE something you ARE. Yes, they can be spoofed, stolen, compromised.
In order to use them reliably for Authentication, they need to be handled properly. That includes never storing them unencrypted. Preferably never storing them at all. It also includes managing changes over time – machine learning.
Most of the problems with Biometrics as Authenticators can be addressed by getting away from the binary pass/fail and moving to a Probability Density Score with Thresholds.
Current “multi-factor” systems are flawed by design. Google, Facebook, Twitter, etc. use Sequential Single Factor… you need to enter your (must be presumed to be insecure) password, then they send a code to your phone that you enter. This has already been compromised. Swiss banks were compromised because the attackers managed to get malware installed on the phone that intercepted the code. They compromised the passwords, intercepted the codes, & made of with >$1 Billion.
Under a DARPA contract, one group I am involved with showed that actually combining any 2 factors into a single ceremony made a drastic difference in security. With virtually any single method, the correct person gets a score in the 100’s while an impostor receives a score in the 10’s. Combining 2 factors in a single ceremony gives the attacker a score in the 100’s but the correct person a score in the 1,000,000’s.
Interesting. Can you expand on the “single ceremony” a bit?
Like any security measure, you have to look at what threat model you are addressing. The usage on Android Marshmallow is quite sane for the expected threat model. They even have the added measure that a power cycle requires the unlock password.
Yes, a dedicated attacker could defeat the fingerprint lock, but they could also pin or password lock, unless of course you only ever unlock your phone in areas that you know are not monitored by video. The article mentions revocation, but revocation is only useful if you know your secret has been stolen, and anytime you unlock your phone is a time the password could be stolen without your knowledge.
Surely this is where the discussion turns to implants. An embedded chip has all the convenience of biometrics – you can’t lose it or forget it and you always have it with you – and all the benefits of randomly generated passwords – it can be updated in the event of a breach or periodically changed for added security with no chance of the user making stupid password choices. There’s just the small point of the technology being mentioned negatively in a certain millenia-old book.
An crypto NFC chip that returns signed messages would be excellent. Think of public/private key crypto in your hand. No spoofing, no replays, no plaintext.
See: https://www.yubico.com/products/yubikey-hardware/yubikey-neo/
Let’s use fingerprints instead of a PIN or a swipe card in low security applications and instead of a user name in higher security applications.
Fingerprint hash encrypted with MAC pin used as key to decrypt data within hardware isolation(Trustzone,TPM->TXT, Ring0, Dongle CPU etc… If we’re going to say something is insecure because of inter-process sniffing than nothing is secure.
“His technique to mimic a fingerprint is pretty simpel. He takes a copy of a fingerprint, then etches it into copper (as if making a PCB), coats the etching in graphite spray, and finally tops it all off with a layer of wood glue or latex. ”
That’s more then enough effort to put of a criminal in any normal situation.
Security is not about being 100% impenetrable – its just about being impractically time taking for the value of the item.
Hi! Great article!
I’d like to translate it to Russian. Please let me know if you’re fine with that.
I don’t think we can stop you! :)
But be nice and include a link back to us here? Thanks.
Relying on the biometric alone is completely flawed and I wish we could move on from kicking that dead horse. You must assume your biometric will be compromised. Please reference our work at BRIVAS. We transform biometric template, then salt it with realtime contextual data making the biometric completely revocable. You cannot be at 2 places at once. We hold 2 patents on this and we just finished our robust algorithm. Seeking commercialization partners. http://brivas.org.
Finally, and this is the kicker, you want your password to be hashable, in order to protect the password database itself from theft.
This conveys a bit wrong message. It helps in case when database gets stolen. But it does nothing to stop the theft from happening. I doubt hashing would deter a hacker from stealing the database.
Firstly, NEVER use fingerprints in a bulk central store where they can be stolen. The only way fingerprints should be used is a way to authenticate the owner to a personal device that will then perform a traditional cryptographic authentication to the central end point. This way the local device only needs to store a small number of prints and they are never available in bulk to an attacker.
That said, the main premise of this article is faulty, in that not all hashes are created equal. The type of hash function referenced in this article is a Cryptographic hash digest function (https://en.wikipedia.org/wiki/Cryptographic_hash_function). This type of function has the features mentioned that make using it on a fingerprint a pointless proposal in that local changes in input have global changes in output.
BUT, there are other types of hash function (https://en.wikipedia.org/wiki/Hash_function) that can have features that optimise their use in this and other fields (also see music ID). Now I don’t know the exact details but a good model for a fingerprint recognition hash would be as follows:-
1/ Take image from reader and analyse for features in as a successive approximation, starting with overall shape of whorl, then sub-worl, then a normalised vector net description of the joins, ends, deviations of all ridges.
2/ Convert these to a string format starting with course features first.
3/ Use a hash digest function that would be useful for string matching, in that its output deviates greatly for changes to the beginning of a string but less and less towards the end of the string.
You can store this hash and use it as a repeatable approximation for the print, such that provided the number of prints is limited then a hash value that is close enough to a stored value will in all probability be the one the owner possesses.
Of course this would not work for bulk storage but as stated above, YOU DON’T WANT THAT!
All said, it is possible that in a population of millions there will be quite a few people who could fingerprint unlock my smartphone, but it is statistically unlikely that any of them will be the one who steals my phone, remembering that the unlock method only gives a limited number of tries before reverting to needing a full passphrase unlock.
Great read. Now the real scary part: Most of this also applies to your signature! Think of all the places : hotels, petitions , renting a car etc … All places where you leave your handwritten signature. Even worse ideas pop up now on new tech companies: digitally storing your hand signature . Meaning so it can be replicated if the reading online device or anything in between sending the picture data and computing the hash out of it is somehow compromised…
A fingerprint is essentially the equivalent of a username or ID, not a password. Must be unique, but not secret. And that’s how it should be viewed and used, crazy that it is considered as anything more.
“You wouldn’t leave your password written down on a sticky-note attached to your monitor at work, would you?”
Never mind.
From a practical atandpoint, fingerprints degrade with age. My mother needed to be fingerprinted for her drivers license and only 2 of her 10 digits had readable prints. The ridges wear down especially in people with thin and delicate skin.
Passwords will never completely die and here’s why: http://bit.ly/1US6lMT
“Never” is a long, long time. Like it or not, eventually people’s identities will go with them wherever they go. But we are a long way from that point now.
Hello, I’m interested about translate this article to korean. May I do it and leave a link here?
Steal my keys, but please don’t steal my fingers. I hate for the “what-you-have” portion of the key to always be on you, with out even the threat that it may not be.
http://newsroom.bankofamerica.com/press-releases/consumer-banking/bank-america-introduces-fingerprint-and-touch-id-sign-its-mobile-ban
https://en.wikipedia.org/wiki/FIDO_Alliance