Do you see the patterns everywhere around you? No? Look closer. Still no? Look again. OK, maybe there’s nothing there.
[Oona Räisänen] hears signals and then takes them apart. And even when there’s nothing there, she’s thinking “what if they were?” Case in point: could one hypothetically transmit coded information in the trilling of a referee’s whistle at the start of a soccer match?
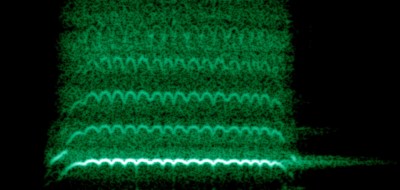 To you, the rapid pitch changes made by the little ball that’s inside a ref’s whistle sounds like “trilling” or “warbling” or something. To [Oona], it sounds like frequency-shift key (FSK) modulation. Could you make a non-random trilling, then, that would sound like a normal whistle?
To you, the rapid pitch changes made by the little ball that’s inside a ref’s whistle sounds like “trilling” or “warbling” or something. To [Oona], it sounds like frequency-shift key (FSK) modulation. Could you make a non-random trilling, then, that would sound like a normal whistle?
Her perl script says yes. It takes the data you want to send, encodes it up as 100 baud FSK, smoothes it out, adds some noise and additional harmonics, and wraps it up in an audio file. There’s even a couple of sync bytes at the front, and then a byte for packet size. Standard pea-whistle protocol (PWP), naturally. If you listen really closely to the samples, you can tell which contains data, but it’s a really good match. Cool!
[Oona] has graced our pages before, naturally. From this beautiful infographic tracing out a dial-up modem handshake to her work reversing her local bus stop information signs or decoding this strange sound emitted by a news helicopter, She’s full of curiosity and good ideas — a hacker’s hacker. Her talk on the bus stop work is inspirational.. She’s one of our secret heroes!
















Someone please insert a video of the hackaday logo encoded in sound from the best badge hack contest at SuperCon yesterday.
I had a good laugh at –
Quote: “Standard pea-whistle protocol (PWP), naturally”
Now there’s one RFC that I probably wont read lol.
Well that’s something not everyone would think of but it’s cool, it would be interesting to embed a password in the whistle sound.
The long 3+ second whistle doesn’t sound completely random, the high/lows of the whistle sound like “data”. Now, if one were to encrypt the message first, to appear more random . . .
You can see it in the spectrogram picture in this article, strongly. Not exactly steganography, which is supposed to be undetectably messing with a baseline signal. More hiding a whistle in a lot of other whistles. Still, more work could be done. And it must be interesting to hear a whistle and immediately start thinking of FSK!
I can’t imaging the way the brain works that hears a normal whistle and thinks “FSK!”. The only clue I can get close to that is hearing the encoded data and going “yeah, that’s not a whistle, that’s data.” Even then, I’m not sure how certain I am I would notice it if it were in some situation, and not just a bare recording of the whistle.
@Elliot Williams – I have a great innovation for Oona to work on. Have you ever wanted to know where a bad-guy’s audio or video recording or streaming broadcast or telephone call is physically located by within a few meters? Well some guys at some US university are working on one that listens for power line background sound anomalies and compares against a database of power plant-generated line noise. My audio-forensics idea is more tactical and precise. It could ostensibly use her PWP protocol. I’ll share details if she or anyone else is interested. Only a GrayMatterWare concept right now…
SOTB
I know folks at Virginia Tech were at one point trying to use audio recordings as a way to check the phase of power from the plants at different locations. I think the folks I know ended up settling on something else. But with smart meters providing data back to the power plant (and anyone listening to the right channels like LEOs and TLAs) could create that map you mention.
The problem with pinpointing a recording is time. If it isn’t live, and there is only one major power supplier in the area, then the small bits of phase data are washed out by any time shifting (i think, could be wrong). A live stream should be easy to pinpoint if they don’t put a very simple high-pass on the audio.
That’s why Oona’s PWS protocol would work great. You know those transceiver boxes with a dipole hanging on the light pole outside your house? They go all the way up the street. They were supposed to be a packet radio digipeater system to allow for Internet access via RF. But the bottom fell out and they went out of biz. The Public Utility companies picked them up for remote meter reading. They are so ubiquitous that Oona’s PWS could be added to them and rapid response vans could be equipped with a mobile version. All warehouse, docks, industrial parks and seedy sides of town could be outfitted with them on lamp poles like the DHS-funded gun shot detectors are doing right now,
When some VIP gets kidnapped the system is turned on. The idiots ALWAYS make a stupid video or audio tape with their demands. Audio forensics always try to pull out the background sounds to get a probable location. How about they pull out a PWS with geo-tagged L/L coordinates? Now they know generally where the idiots are holding the VIP. For telephone calls the PWS frequency needs to be lowered as close to 3Khz as possible so it will pass the POTS systems. That means it will be heard from the street, Need to make it sound like something innocuous (i.e. birds chirping?).
But VCR recorders and Camcorders can pass 20Khz or better. Adults can’t hear that anyway. Children can. So her PWS could chirp at 16-20Khz and no one would hear it., The kids would probably ignore it. It wouldn’t run 7 x 24 only when the need arrives.
The power line profiler doesn’t sound like such a great idea. This idea could work if countermeasures are not used.I call the PWS devices chirpers. All they do is chirp out their L/L coordinates and any recording device picks it up. The rest is academic,
SOTB
beyond awesome!
I would be interested in a captain crunch type whistle for cell phones ;) This would be especially useful at crosswalks where folks seem to think they can walk thru six lanes of traffic whenever they please as long as they have headphones on lol.
On a side note: neat concept and was a bit different article than I expected. Since we are primarily dealing with FSK, seems like a MIDI whistle would be made for simple “start stop/program change” data.
Very cool!
I’ve always wanted to try something like this, hiding data in ambient sounds from nature that nobody pays attention to. A major one is insect sounds – have a look at a spectrogram of a cricket chirp; it bears some similarity to the pea whistle but might give even more opportunity to stuff a bit of modulation in. So many projects and so little time…
Crickets do send out useful data with their chirps! Check out “Dolbear’s Law”
W.W. Heisenberg – Not true! A common field cricket changes it’s chirp rate in direct proportion to ambient temperature. If you empirically track it you could come up with an algorithm to judge temperature with just a microphone and a Arduino. Also the ancient Chinese used field crickets as rudimentary intruder alarms. They surrounded the house with them. At night they’d start in with the incessant chirping. Then when the crickets detected footfall (i.e. intruder) they did a cascaded ceasing of chirps only in that zone while others in other zones kept going. Hence you have a zoned burglar alarm. Albeit, a reverse alarm (normally on and alarm becomes normally off almost like a Boolean condition or binary data?).
W.W. Heisenberg – Oops! I thought you said “Crickets DON’T send out useful data…” Sorry my bad! %-(