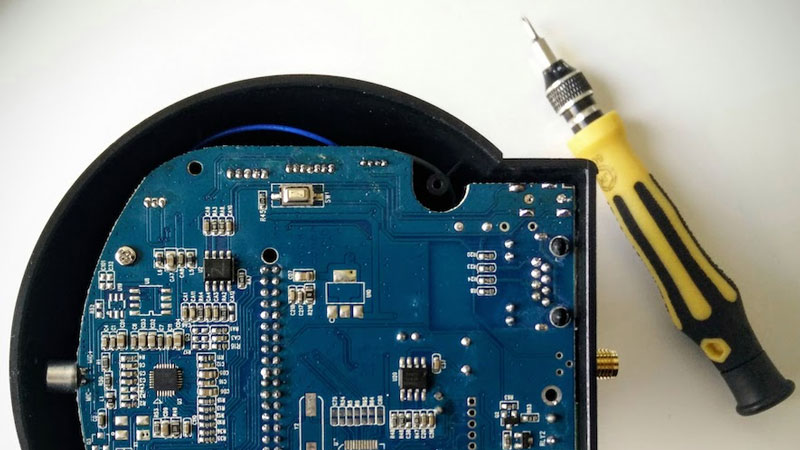
So you bring home a shiny new gadget. You plug it into your network, turn it on, and it does… well, whatever it wants. Hopefully, it does what you expect and no more, but there is no guarantee: it could be sending your network traffic to the NSA, MI5 or just the highest bidder. [Jelmer] decided to find out what a new IP camera did, and how easy it was to find out by taking a good poke around inside.
In his write-up of this teardown, he describes how he used Wireshark to see who the camera was talking to over the Interwebs, and how he was able to get root access to the device itself (spoilers: the root password was 1234546). He did this by using the serial interface of the Ralink RT3050 that is the brains of the camera to get in, which provided a nice console when he asked politely. A bit of poking around found the password file, which was all too easily decrypted with John the ripper.
This is basic stuff, but if you’ve never opened up an embedded Linux device and gotten root on it, you absolutely should. And now you’ve got a nicely written lesson in how to do it. Go poke around inside the things you own!















Very nice writeup, that trick with tunneling a tcpdump session from your router to a local wireshark session is gold.
Would be interesting to see his plans to reflash it with openwrt pan out, it could even make these little cameras usable. The real question is if they have the horsepower to do support RTP/RTSP, since doing ipcams using mjpeg requires huge amount of bandwidth and server side processing time.
Thanks!
From what I read so far, horsepower of the Ralink chip is currently indeed the limiting factor when doing openwrt and USB-cam in a sort of useful ipcam configuration. If I manage to get something usable running on it, I’ll do a follow-up post.
mjpg-streamer and motion packages are available for OpenWRT. That’ll get you video streaming/motion detection. How you do pan/tilt is up to you.
I used iSpy 64bit to access the tilt and pan of a recent ip cam bin find. I brought them home just to test out the sd cards and see what was on there. The cards had been corrupted and it was more effort than value to watch a desk chair for 45 minutes so I ended up slogging thru forums for an afternoon. In the end, it appears that the previous owner had locked it straight. I thought I was crazy, sending commands to get it to turn because I knew it had the capability from the swiveling it did on boot up. Thanks for the write up, Jelmer. I will have to dig in more and poke around to see what other goodies are in my no-name cam :)
Yes, you can run openwrt on it, though you’ll have some annoyances with drivers and gpio crud.
the soc chip and board, is like the nixcore,
http://nixcores.com/nixcore_x1.php
It also has the pinout of the little soc board.
some friends and I had a little poke at a similar one a few years ago, and got bored with it.
http://cam.yankie.be
oh yeah, it’s one thing to get openwrt running on it, it’s another altogether to get the motors, sound, and webcam working. but that was two years ago, maybe things have changed by now….
PS. I looked around for how to add clickable links here, though didn’t find it with a simple google search. if any editor can fix this, thanks.
enjoy !
Every time I read one of these I’m left with the feeling that I would never want to be the engineer who is responsible for locking these down. Seems to be just impossible. Maybe that is why they are so easy to get in too. They’ve given up trying. :)
They aren’t locked down on purpose. You would be amazed seeing how many security systems are open to attack or eavesdropping. Nearly all of those cheap H264 DVR contain fixed hidden passwords that allow full admin access from everywhere. They’re cheap ($40 or less) Linux boxes that would well deserve some reverse engineering to remove these security holes, and possibly to get rid of their dreadful dependency on active-x web controls to be controlled (yep, Linux based but no Linux and IE only on the client). First one succeeding in that task is going to get a lot of attention.
There’s too much money to be made to consider trivialities such as responsibility… sheesh! Priorities, people, priorities!
If you secure it 100% then you will have the FBI on you back saying put damn backdoors in it now. You only have to look at Apple, and in reality they are only fighting in public for PR reasons, because they were asked publicly (If the request was a secret FISA court order it happened already).
Pure speculation, but there’s a possibility in between.
FBI privately asks Apple to put ..say 8 backdoors , then asks publicly for 2 more (*).
Apple bows and install unseen first 8 backdoors, then publicly strongly opposes the last two.
Win-Win: FBI gets what it wants and Apple gets huge PR.
*= very likely over a mutual agreement. FBI does not want to screw Apple, and Apple does not want to oppose FBI, but both have an agenda that the above scenario could help to fulfill.
The FBI didn’t ask for a back-door, they asked for that specific phone to be modified so that it would not care about incorrect PIN input, then the FBI just need to try all combinations to open the phone.
Clearly this mod could not work “in the wild” as people would notice it.
Apple’s argument was twofold, one that the FBI did not have a constitutional right to force them to help (to be decided in court in the future, perhaps) and two that if they changed that phone they could be made by other governments to do it again to other iPhones, which is a spurious claim as they have already (stupidly) publicised that doing so is technically possible so there is nothing right now from stopping other governments from putting pressure on Apple to do it.
The facts are known, the logic is not complex, so why don’t you people lay off the paranoid conspiracy theories?
lmao no. That won’t happen. Apple just likes to support terrorists and sue everyone out of existence. I can’t think of a more “American” company.
Hell I help folks out on a weekly basis with iOS9 locks (bricks). Some kind soul out there wrote Adoni.s just for that. Apple has yet to patch it three versions of their store-bought OS later. The whole thing was a PR stunt. Make sure you are on the right side of history ;) Apple was protecting terrorists not some dead beat dad not paying his child support… Dog comes with the fleas.
And that’s where you go wrong with thinking someone is responsible.
Crap, was trying to reply to Richard
That colour balance issue, the purple couch, is probably a lack of an IR-cut feature. This may be why the unit is so cheap too.
Priority one. Stack em high. Priority two. Sell em cheap…
Security doesn’t get a look in if your design brief is get this project done, get on to the next one.
Am I the only one that sees that there is a typo in this article in the root password? 1234546 would have been a much harder to guess (not to brute force I guess) than 123456.