Lastpass is a great piece of software when it comes to convenience, but a recent simple hack shows just how insecure software like it can be. [Mathias Karlsson] nabbed a nice $1000 bounty for its discovery.
Lastpass’s auto-fill works by injecting some html into the website you’re visiting. It runs a bit of Javascript to parse the URL. However, the parsing script was laughably vague. By changing the URL of the page, inserting a few meaningless-to-the server slugs into the URL, an attacker could get Lastpass to give it a password and username combo for any website.
The discussion in the HackerNews comment section more-or-less unilaterally agreed that most systems like this have their glaring flaws, but that the overall benefits of having secure passwords generated and managed by software was still worth the risk when compared to having a few commonly reused passwords over multiple sites.
One could get a more secure key manager by using software like KeePass, but it’s missing some of the convenience factor of remote-based services and relies on a user protecting their key files adequately.
Still, as scary as they are, openly discussing hacks like this after responsible disclosure is good because they force companies like Lastpass, who have some very big name clients, to take their code review and transparency more seriously.

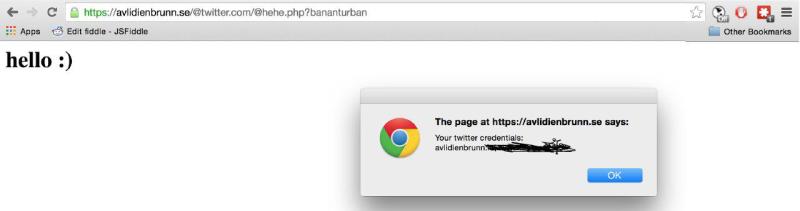














This hack actually brought a lot of Lastpass community to discover the Hackaday community-started offline password keeper Mooltipass, which definitely doesn’t have the same attack surface : https://groups.google.com/d/msg/mooltipass/Nq0jPIxmUm8/RRzSMOO1AgAJ
We should launch the mini crowdfunding campaign in a month :)
I fail to see the point. Keepass is the go-to solution for an offline password-keeper, the software and the encryption it uses is considered secure and strong, and they have quite a few years of experience now behind the belt, so what does Mooltipass provide that Keepass doesn’t? Would it just make more sense to contribute to what we already have instead of reinventing the wheel and all the bugs that come with it in the beginning?
I’m guessing from your post that you haven’t looked at the Mooltipass solution in details.
Keepass isn’t an offline password keeper solution, as it is running on your Operating System and uses your computer memory for your credential database and master password.
The Mooltipass is a standalone device which sends passwords through USB only when the user approves it on the device itself.
Which is neat and all but the day websites can just run rampant and read any memory owned by any process is the day we have bigger problems to worry about than whether the keepass DB was open at the time ;D
Well, it already happens and here are a few links:
– mobile devices: https://tech.slashdot.org/story/14/08/22/2042213/researchers-hack-gmail-with-92-percent-success-rate
– a trojan to specifically target sw based password keepers master passphrase: http://thehackernews.com/2014/11/new-citadel-trojan-targets-your.html
– vulnerabilities in other software based password keepers: https://slashdot.org/story/204593
It already happens… I have a comment with 3 links pending admin approval.
If you want to find them, google:
– “New Citadel Trojan Targets Your Password Managers”
– “Critical Vulnerabilities In Web-Based Password Managers Found”
– and the one you’ll find most interesting: “Researchers Hack Gmail With 92 Percent Success Rate” (slashdot)
Replying to my own comment because I can’t reply to limpkin:
What I was thinking of is literally browsing to say my-hacked-domain.hax and suddenly having the website without installing any malware scan my entire hard drive, get all my private keys, databases, family photos and whatever. Your links are distinctly not that.
Citadel is classic malware, install something dodgy and it’ll start a keylogger when you start keepass et al. Nothing new there.
Vulnerabilities in web-based password managers is pretty much what this hackaday article is about, some services like lastpass haven’t quite fixed all the logical problems with their software so there are holes.
As for the researchers hack gmail thing, it’s essentially malware installed on the device being able to see how much memory an app is using (so running top) and from there guessing which page of the app they’re using. With careful timing so it doesn’t look odd they then create a popup that mimics the log-in screen of an app, and there’s your complete attack.
2 x Malware installed, 1x logical errors creating vulnerabilities.
@Max : you are right, I went over the fact that you mentioned website based attacks only. My point was that unless you are 100% sure of what you’re installing in your computer or devices you have no way of knowing if your passwords haven’t been compromised.
Most of those password utilities are commercial, and I always assume they are harvesting your passwords. And even if they did not from themselves, most of them are US based too.. enough said.
And they always want to back up in the cloud too, that’s not suspicious.
So yeah, a hardware solution like that is indeed more viable.
Which is why I like KeePass. It is open source, so allows you (and everyone else) to look at the code and you can determine if it is secure enough for you. You can then compile that source code yourself if you wish, and you then know exactly what you are using.
even though i hate how half the internet is overusing this word; rip.
$1000 sounds a bit low for a serious vulnerability on this scale. I’ve always held off on password managers because it was a single point of failure to breach everything.
But I’m considering using ‘pass’ (https://www.passwordstore.org), does anyone have any experience with this? It uses GPG to encrypt and I use an OpenPGP card so it would use hardware encryption, making a breach less likely.
I will continue to use LastPass until SQRL has made user name and password a thing from last century. SQRL is an authentication system designed for the 21st century with hackers and “trust no one” as the philosophy.
I recently started using pass and I really like it. On Android I use the Password Store app for pass and on my PC the cli and Firefox plugin. Syncing via git works very well too (just make sure that you secured your git/ssh server enough. even though gpg should be good enough (TM) any additional layer of security is good)
Isn’t Veracode testing supposed to find that kind of weakness?
I am a little bit skeptical overall. How could this fall through the cracks?
Anyway I have a yubikey attached to my Lastpass. Knocking on wood that it saves me a lot of worries.
Ah, I just use 123456 for everything.
http://splashdata.com/press/WorstPasswords-2014.png
There’s gotta be a reason it’s #1 right??????
;-)
Ha! My password its it’s better, its goes to 11 … 9AB ;)
True Story… personally seen at a government facility, the password for a critical system was not only stuck on the monitor with a post it note, it was also pa55w0rd
this is another reason not to use password managers but rather to use macro software such as applescript to type the password because at least the script lives on my machine and i know how secure it is by who accesses my machine
I have this simple method where I memorised the last 5000 digits of pi in reverse order and apply an offset according to the hex value of the first 3 characters of a site’s name, picking 50 digits then mentally dividing by the unix epoch of the time I create the account, et viola! Unique yet easily memorable reasonably secure passwords.
Yeah, this method should be enforced everywhere. Ha!
Oh no! I’ve been doing the same thing! If we happened to create accounts at the same time, and the hashes aren’t salted, then attackers could pwn us both and get two for the price of one!
I don’t think you are being entirely open and truthful. If you really do know an algorithm to find the last 5000 digits of pi then you have access to technologies not from our universe. Why are you piddling around with us mere humans?
The last infinity of digits of Pi are all equal to zero. It will be ‘quite a while’ until we get to the start of the last infinity.
That’s a really interesting conjecture I had not heard about. Your own creation, or is this a commonly-accepted thought?
Your Pi comment reminded me, no surprise, of this.
I wrote this 26 years ago. Edited 9 years ago. May not have looked at it since then. Just for fun, of course.
“Theology” [tm] may be ignored & it still be fun. [Pasted from a Word document – formatting was very different].
I AM THE INVERSE SQUARE LAW
I AM the Inverse Square Law
Infinitely accurately
For the pure joy of my creation
I AM the arbiter of Pi
Non repeating to the 10 billion trillionth place
Precisely
Thereafter set to zero until infinity
That those of my creation who so determine may wonder
And grow silent
I AM not the unified field theory
For it was and is not
And shall not be
Until I recreate it anew in my new creation
I AM the Gravitational and the Weak and Strong Atomic forces
There are no other
Though to those who seek it may not so seem
Rejoicing in the dance of each particle
Knowing their all and every place and time
With no uncertainty
I AM the image of the invisible
In Me all things consist and have their being
Without Me is or was or shall be not any thing
I AM the Alpha and the Omega
The Beginning and the End
The First and the Last
The Passage and the Path
The Reason and the Cause
The Commencement and the Resting Place
Come unto Me
It’s voilà.
A viola is an instrument in the violin family
I create site-unique passwords based on a site name related algorithm which is amenable to mental implementation (unless you are my wife who thinks its crazy AND too hard). The passwords are deemed ‘strong’ by all basic simplistic metrics (ucase, lcase, numerals, non-alpha, …). I could post the algorithm here but (1) even I’m not that stupid even on a bad day and (2) then I’d have to kill myself. HOWEVER the point of writing this is to point out that such systems are entirely doable, within the mental scope of most people, relieve one of the restrictions of password management systems or lists and MAY even be ‘secure enough’. Try making your own – it needs to combine highly obscure method with relative ease of use and certainty of generating the correct password for a given site.
However, sites are stupid and have arbitrary password rules which screw up any attempt at a strong reproducible personal system. This can be, limitation of length to 10 or 12 chars, limitation of non alphanumerics, enforced strong password rules that insist you haven’t got enough numeric or other chars, or not enough upper case, or whatever. One obnoxious site did a dictionary check and wouldn’t let you use anything that had a dictionary word in, and two and 3 letter words will appear frequently in random strings of decent length.
So, I am highly sceptical of any system that claims it works everywhere.
My system fails on a few sites, and I have semi standard [tm] fallback methods.
Our inland revenue will not allow a password as long as I usually generate !
Our largest ISP will not allow some non-alpha characters I wish to use.
But those are almost the only ones of countless ones.
For key ones I keep a hinting log – you’d need a brain as weird as mine to make any sense of it and still no good
For trade sites and similar I don’t need to record, log or hint them – the system just works.
Others could make their own systems that work as well.
It’s worth noting that they patched the hole as soon as they were told about it.
The announcement about the vulnerability came after it had been patched.
It’s worth noting that a stupid flaw gives insight in the failings of the coders.
KeePass works fine. You can even host the binaries and database on your own SSL enabled server for remote access.
The database file can be left lying around without much thought if properly encrypted.
Can we just turn off the AUTO FILL IN feature? Then we can still click fill in whatever we want right?
I don’t think the issue for cases like this is whether LastPass (or any other password manager or scheme, or even SQRL) has a bug, but how they react to it. As far as I can tell, they reacted to it just fine.
All these other really cool-sounding schemes based on how you tie your shoes or comb your hair that day are fine for geeks, but everyday folks are just not going to put up with it. I don’t know about you foreigners (or as we in the USA call you, “suspects”), but here in America, we can sum up the populations willing-to-think-about-it-ness in a single word: Trump.
Say, aren’t we overdue for someone to mention the ridiculous “Correct Horse Battery Staple” algorithm? You know, the one that works fine if you have only 2-3 passwords to remember but wouldn’t do so well for my LastPass vault of over 400 unique passwords? OK, I guess I just did, so we can cross that off our list.
jesus you people are nerds