[Gerardo Iglesias Galván] decided he wanted to try his hand at bug-bounty hunting — where companies offer to pay hackers for finding vulnerabilities. Usually, this involves getting a device or accessing a device on the network, attacking it as a black box, and finding a way in. [Gerrado] realized that some vendors now supply virtual images of their appliances for testing, so instead of attacking a device on the network, he put the software in a virtual machine and attempted to gain access to the device. Understanding the steps he took can help you shore up your defenses against criminals, who might be after more than just a manufacturer’s debugging bounty.
The device he attacked tried to secure itself. The bootloader was protected. The filesystems were encrypted. Did he get in? Read the story for yourself and find out.
As more projects connect to the Internet, there’s more opportunity for bad mischief. It wasn’t from hacking, but look how much trouble shutting down everyone’s Nest thermostats caused, not to mention the major internet outage caused by hacked cameras. We’ve talked about hardening Raspberry Pi projects before using things like two-factor authentication. Might not be enough, but its a start.















I hope people doing such things also tell the wider public if they find companies put nefarious stuff for themselves in there. Nasty intrusion of privacy and such, or attempts to access stuff it should not access.
Like Netgear Tp-Link D-link, Basically anyone that manufactures consumer grade Network equipment leaves doors everywhere, It’s absolutely intentional it’s bad because, We’ve got this DSL modem that anyone can just remotely query without logging in sending request to the Cli via HTTP without authentication no firmware update was ever created to fix it, the login details from simple running cat on the pwd file showed login info which then gives access to the remote email account and use of other ISP related services.
Interesting, were in the future everything will be virtualized, even the networking.
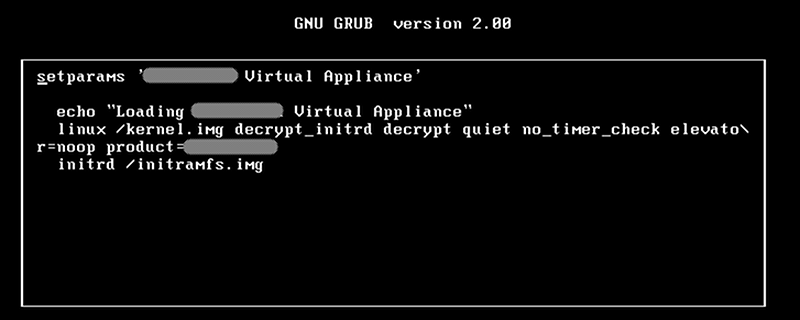
He could also try to ask the vendor for the GPL source code of the kernel to get the initramfs key.
I am gunna say reversing the key would have been faster
And people say learning assembly is ludicrous…
A interesting read.
If the security really matters, such keys should never be stored in the file system as is. They should be e.g. sealed with TPM chip storage root key or tied to secure boot. At minimum the real production keys should not be available in development VM images.
Agreed. Anything else is just security through obscurity.
And there are always hackers and hobbyist who have time to dig through the layers of obscurity :)
Ever wonder why your phone suddenly gets hot in your pocket when you’re not using it.
It’s a three letter agency uploading an updated image of it stupendously quickly. Co-processors and layers of abstraction, aren’t always a good idea.
Paranoid are we? Have any proof? Would be more of an interesting read than this…
+1000
If they hadn’t used a Grub password that had previously been leaked, they might have been saved.
There’s still ongoing DDoS and traffic overload issues, likely from the Murai botnet, has been for the past week. Murai is said to have over 1 Tb/s of total capacity.
http://downdetector.com/status/level3/map/
https://www.akamai.com/us/en/solutions/intelligent-platform/visualizing-akamai/real-time-web-monitor.jsp
the proof is when a fully charged cellphone, when shut down, drains the battery faster then when it is “on” in standby, … interesting how such an occurence might only happen when in the presence of others in direct competetition for information andor mis-information, and may happen many times in such an identical situation involving identical groupes of people andor pwned devices…
… of course im crazy; cellphones can not be hacked, thats impossible!