If the headline makes today’s hack sound like it was easy, rest assured that it wasn’t. But if you’re interested in embedded device hacking, read on.
[Andres] wanted to install a custom OS firmware on a cheap home router, so he bought a router known to be reflashable only to find that the newer version of the firmware made that difficult. We’ve all been there. But instead of throwing the device in the closet, [Andres] beat it into submission, discovering a bug in the firmware, exploiting it, and writing it up for the manufacturer. (And just as we’re going to press: posting the code for the downgrade exploit here.)
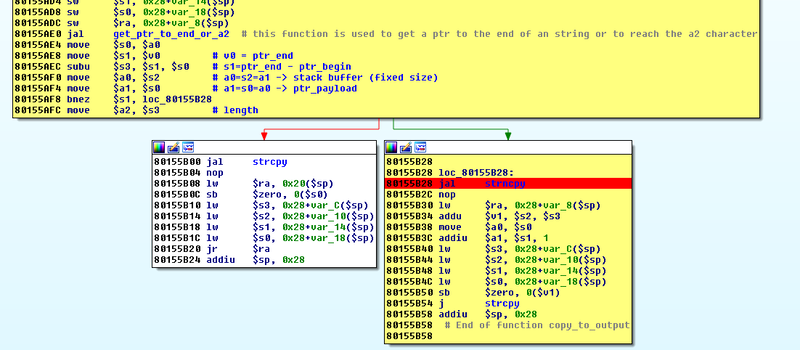
This is not a weekend hack — this took a professional many hours of serious labor. But it was made a lot easier because TP-Link left a debugging protocol active, listening on the LAN interface, and not requiring authentication. [Andres] found most of the information he needed in patents, and soon had debugging insight into the running device.
After some heavy-duty static reverse engineering based on the firmware that he downloaded from the manufacturer’s website, he found a buffer overflow opportunity in the code, and managed to run his own code over the debugging link.
Because [Andres] is a security professional, he gets paid for finding vulnerabilities like this, but also for making them sound ominous. Still, he notes that you can only reach the debug protocol over the local LAN, and not from the network at large. So it’s much more likely that you’ll use this exploit to flash the firmware of your choice than it is that any baddies would do so. (It’s not a bug, it’s a feature!) But still, this is an awesome hack!
Thanks to [norber] for the tip!















The problem is if a device on the network gets infected, your router can get infected leaving a permanent way into your LAN, if you don’t know it’s there. Which is also the reason it’s recommended to use a non-default subnet and log out of your router’s admin page when you’re done – so web pages loaded in your browser can’t (easily) attack your router.
Yes… suddenly segregating stuff into VLANs and using ex-data centre kit starts to seem necessary rather than just “fun”.
“Smart” switches come with VLANS. The harder part is the non-uniformity of implementation, and explaining the subject in general to the public.
The interesting thing is that even simple switches contain (sometimes? always?) the same chipset than the more capable (and more expensive!) ones, but without the (web) interface to do the configuration. If you void your warranty you can interface to the chip really easily with a µC (I2C or something like this), the real problem is that you can’t find documentation about the registers used…
About the hack presented here: Well, yet another security flaw in a consumer router… But why on earth does the linked blog need javascript to show something? Pages like this that use JS without a real need are so annoying!
You really need to find something else to be annoyed with.
@Jerry
Seems like you don’t use NoScript…
Repeat after me. “VLANs are a traffic management tool, not a security measure.” Or not, if you don’t care about security.
Pfft. Says who? VLANs are a perfectly appropriate security measure. Defense in depth doesn’t rely on each security measure being perfect, it assumes quite the opposite.
If VLANs were worthless for security, why would the NSA Cisco hardening guide spend so much time discussing them?
Exactly so. Hackers are going after low-hanging fruit. Raise the bar a bit and they go somewhere else. Hence, VLANs change the network from typical to odd from the hacker’s perspective. Even if it is not a serious defence, it is all you need… for now.
https://en.wikipedia.org/wiki/VLAN_hopping
Brilliant write-up! The techniques shown could be useful for many other devices and [Andres] explained them with great lucidity.
The only data I could get from the device was the values of the PC and SP registers of the processes, located in the hidden web page found before.
My strategy was to develop an exploit using a “jump debugging” technique, consisting in using the jmp instruction to jump to different addresses depending on the success or failure of the executed code.
Where there is a will, there is a way!
Damn, I can’t even imagine the hours he must have spent to do that… awesome job!
Many of the Tp-link devices have a much simpler flaw that can be used. Bash code can be injected into the wifi network name. https://m.reddit.com/r/openwrt/comments/4bp49b/tplink_locked_firmware_workaround_without_tftp/?ref=search_posts
I read your post thinking “Surely it’s not back quotes, don’t let it be back quotes”. Then I went to the page. It’s back quotes! Oh no! Oldest trick in the book! Trying to stick back quotes in strings is the grandfather of injecting escape characters into SQL requests, and that’s the oldest trick on the web. Back quotes! It’s the sort of thing you’d try on Unix when you’ve got no idea, and are hoping for a fluke. Dear me!
This story shall include “my friend” anyway a few years ago he didn’t have an internet connection when moving into a new house, “My friend” being very much like me in fact you could almost say he was my double. tried to get connected as soon as possible but there was a problem with the line coming into the house and it wouldn’t be fixed and then connected for two weeks.
So he had a look at the neighbours WIFI networks and noticed he got amazing signal from one very close by and it was using WEP encryption. He opened up aircrack and started collecting packets, didn’t take long to get enough to then go on to crack the wifi password. My friend now had a fast stable internet connection but he wanted manually enter some port forwarding settings into the router for some of the many apps he uses. So after checking the router he realised the password wasn’t admin, black or password etc. After looking around and poking about he didn’t find much. Time for a port scan (I imagine he thought to himself), So he scanned the router for open ports and noticed something odd, Port 32764 was open, So he looks this up in google, and he finds out that this is actually a back door (netgear) that gave away the admin password if you sent the right info to the port, Better yet there was a python script that you could run that would automate the whole process. He downloaded the script using mobile phone data and boom Admin password. He now owned the network. He used the WIFI network until his connection was installed and was getting great speeds. He did set some QOS settings to favour every IP but his so if anyone was using the network they had full speed.
Anyway look your router up in google, Make sure you are not broadcasting password backdoors which the router companies left there by “mistake”.
Link to check Port 32764 http://www.ghacks.net/2014/01/06/find-router-listening-backdoor-port-32764/
The presentation (avaible as pdf) on Github is quite fun! :-) https://github.com/elvanderb/TCP-32764
I just downloaded the presentation and I remembered it once I seen a page or two, Yeah the author of this exploit has a great sense of humour.
The tale of SWIM – “someone who isn’t me”. SWIM once did bad things with an IRC botnet, etc.
I was going to use SWIM but I wasn’t sure if everyone would understand ;)
When comcast first started selling cable modems in the UK (the first broadband service we got) the network security advice was near non-existant.
People would connect them directly to their PC NIC or via USB.
My firewall used to get hammered by windows requests for SMB sharing or “hey who has IP xxxx”.
So I used to leave them a txt file on their desktop called README in caps of course, which gave them instructions on how to secure their PC.
And WEP was good times. £150 to install a phone line in a rental house? Don’t think so :)
Amazing how far a 300mW card and cantenna can go, but more importantly pickup the weak signal from a netgear etc at distance.
haha I remember scanning random IP ranges for SMB shares years ago used to find all sorts of things, I miss the wild west days of the internet.
>you can only reach the debug protocol over the local LAN
DNS rebinding solves that problem
What about WebRTC?
Hi Anton Kovalenko,I agree with you this was a great informative post you have shared on this page about the debugging of protocol by giving the keys to find a error in a packet with the help of wireless mobile router because today TP-Link left a debugging protocol active, listening on the LAN interface, and not requiring authentication. [Andres] found most of the information he needed in patents, and soon had debugging insight into the running device.,So you must secure your device by using the transport control protocol otherwise your system files may be hack due to the lack of system security through wireless mobile router.
Thanks.