The Amazon Dash button is now in its second hardware revision, and in a talk at the 33rd Chaos Communications Congress, [Hunz] not only tears it apart and illuminates the differences with the first version, but he also manages to reverse engineer it enough to get his own code running. This opens up a whole raft of possibilities that go beyond the simple “intercept the IP traffic” style hacks that we’ve seen.
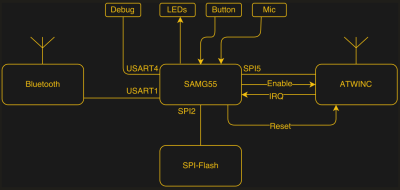 Just getting into the Dash is a bit of work, so buy two: one to cut apart and locate the parts that you have to avoid next time. Once you get in, everything is tiny! There are a lot of 0201 SMD parts. Hidden underneath a plastic blob (acetone!) is an Atmel ATSAMG55, a 120 MHz ARM Cortex-M4 with FPU, and a beefy CPU all around. There is also a 2.4 GHz radio with a built-in IP stack that handles all the WiFi, with built-in TLS support. Other parts include a boost voltage converter, a BTLE chipset, an LED, a microphone, and some SPI flash.
Just getting into the Dash is a bit of work, so buy two: one to cut apart and locate the parts that you have to avoid next time. Once you get in, everything is tiny! There are a lot of 0201 SMD parts. Hidden underneath a plastic blob (acetone!) is an Atmel ATSAMG55, a 120 MHz ARM Cortex-M4 with FPU, and a beefy CPU all around. There is also a 2.4 GHz radio with a built-in IP stack that handles all the WiFi, with built-in TLS support. Other parts include a boost voltage converter, a BTLE chipset, an LED, a microphone, and some SPI flash.
The strangest part of the device is the sleep mode. The voltage regulator is turned on by user button press and held on using a GPIO pin on the CPU. Once the microcontroller lets go of the power supply, all power is off until the button is pressed again. It’s hard to use any less power when sleeping. Even so, the microcontroller monitors the battery voltage and presumably phones home when it gets low.
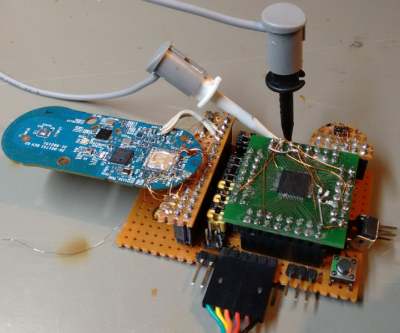 [Hunz] looked at the communication stream, finding HTTP data over SPI between the microcontroller and the WiFi radio chip, and TLS-encrypted HTTPS from there on out. So he soldered in an FPGA to man-in-the-middle attack the hardware, making a beautiful hacker’s development kit out of the $5 gadget.
[Hunz] looked at the communication stream, finding HTTP data over SPI between the microcontroller and the WiFi radio chip, and TLS-encrypted HTTPS from there on out. So he soldered in an FPGA to man-in-the-middle attack the hardware, making a beautiful hacker’s development kit out of the $5 gadget.
The old Dash buttons had SWD debugging enabled and a serial console, and the new firmware has it disabled except for a few commands, so it’s not easy to dump. So [Hunz] desoldered the SPI flash and read it externally. That gave him the firmware, minus the bootloader and some configuration storage. Next came a great trick: he wrote the same firmware to a fresh SAMG55, and the firmware worked. The chip he flashed it to had SWD debugging running, however, so he was able to work in a much more friendly environment with developer console and everything. (Brilliant!)
With a firmware dump and a running version of the system under debugging, he eventually found a hole in the audio configuration protocol — which is used to configure the device through an audio file played into the microphone like an updated version of an old-school modem. The input in the audio protocol, unfortunately for Amazon, wasn’t checked for length. Buffer overflow and a complete flash dump ensue. The video of him hacking the button with an earbud is classic.
Amazon will patch this hole sometime soon, of course, but they can’t do so if the button can’t connect to their servers. [Hunz] has said he’s not going to work on it much more, but here’s his GitHub. Have at it!
















49:27 question about how long this hack took made me smile:
“Some guys buy a cinema ticket for about 10 EUR and get about 90 minutes of fun and I buy the Dash Button for 5 and then have plenty of weekends [of fun]”.
This is a great write-up, and a great hack all around. I like the “sleep mode”, may implement something like it in a future project that need ultra-low power. Also the attack vector is awesome. I’m gonna buy a couple of these before they patch this “vulnerability.” I always wanted a find-my-phone button
The sleep mode is a classic trick that has been used for decades. (Not that makes it any less useful)
re: used for decades: I would believe it. It also reminds me of Sprite’s self-powering AVR step-up converter hack. http://spritesmods.com/?art=ucboost&page=3
In this case, it also means that the device isn’t spying on you. (Which is also evident from the small battery vs. WiFi power requirements, but this provides an extra layer of tinfoil for the hat.)
Can confirm. I’ve seen it in general use in the industry certainly for as long as I’ve been involved (15 years or so).
Yup, I’ve done it before. Run your device’s battery through a relay. Power button bridges the relay’s contacts, supplying power to the circuit. The circuit energises the relay’s coil through a GPIO and driver transistor. Then when you want to switch off, drop the GPIO.
Depending on your choice of relay, it means more power use while it’s on, but zero when it’s off. Mine was a toy I was making for a friend’s kid, I figured it would be off most of the time. Ran off AA batteries, so this way keeps it simple.
You could use a transistor instead of a relay I suppose. I was going for simplicity.
Devices these days are proof that “good things come in small packages”.
Amazon: “We need this gadget thing. Make it good and cheap, Mr. Productmanager!”
Productmanager: “Hey top-of-the-line Developer, do this!”
Top-of-the-line Developer: “OK, I can bill you 3 hours now, I will add all kinds of bells n whistles, so I can bill you 10.”
Simple products done right – loving it (although the product itself is about as useful as a rectangular wheel (unless you are driving on a sinusoidal road))…
For some unknown reason, the video exits the fullscreen always. This makes it harder to see the details in the video.
Might just be an issue with the embedded video on our page. Try clicking through to the 33c3 talk page linked at the beginning of Elliot’s writeup.
I’m new into the hardware hacking scene and those grey grabber things with the wires attached look like exactly what I want!! I’ve been using aligator clips which seem to destroy the boards I’m clipping them to (and the metal clips touch and short things out). Can anyone give me the technical name for the “grey grabber thingies”?
From now on, I refer to them as “grey grabber thingies”. ;)
Due to your spelling of “grey” I’m going to guess you’re from the UK (or Europe). You can find some “probes” or “test hooks” here: http://www.hobbytronics.co.uk/test-hook
Actually I’m in the states, but I really like star trek.. so you know.. “Tea, Earl Grey, Hot” and all.
thanks :)
You’re not going to believe this: they’re called “grabber test probes”.
Grey is only one of the many colors they come in.
Tinfoil hat time – did he find any hooks that allowed amazon to issue a command that would turn on the microphone and stream the captured audio across wifi?
Sooner or later and with some toys already. The ubiquity of IoT and such as this will be a problem.
In this case, battery life is going to limit it. It’s got a nice powerful processor, but even if you have it monitoring the mic constantly for keywords, and only starting the Wifi connection on that trigger, you’d wipe out the battery in a couple of days. That’s assuming voice-rec of the necessary quality is possible without an online Google-farm available.
This particular device I don’t think would make a good bug. But that doesn’t matter, cellphones make fantastic ones, and they’re all over the place.
This is a great start. Who is going to work on a way to flash a new firmware without opening the case? And to update the firmware on the PRoC over UART as well so it can be a Bluetooth or WiFi button.
I would love to see an exploit to download custom firmware. I know that the generation 1 dash buttons does not really check the server cert (I can use self-signed cert to fool it, as long as it pretends to be from parker-gateway-na.amazon.com). I wonder if the generation 1 is capable of firmware download? I can definitely set the POST requests through my fake server.
The tough part is getting my hands on the previous generation Dash. Among the dozens of dash buttons I bought, only 1 is the previous generation dash button.
The packet length exploit has been patched in the latest firmware, with an “Invalid Packet Length” message being printed on the serial console.
Here is a youtube mirror because that video host is total shit. https://www.youtube.com/watch?v=7he02D7Wqgk
How many rolls of toilet paper were ordered accidentally while hacking the device?