There are innumerable password hacking methods but recent advances in acoustic and accelerometer sensing have opened up the door to side-channel attacks, where passwords or other sensitive data can be extracted from the acoustic properties of the electronics and human interface to the device. A recent and dramatic example includes the hacking of RSA encryption simply by listening to the frequencies of sound a processor puts out when crunching the numbers.
Now there is a new long-distance hack on the scene. The Cerebrum system represents a recent innovation in side-channel password attacks leveraging acoustic signatures of mobile and other electronic devices to extract password data at stand-off distances.
Research scientists at cFREG provide a compelling demonstration of the Cerebrum prototype. It uses Password Frequency Sensing (PFS), where the acoustic signature of a password being entered into an electronic device is acquired, sent up to the cloud, passed through a proprietary deep learning algorithm, and decoded. Demonstrations and technical details are shown in the video below.
Many of these methods have been shown previously, as explained by MIT researcher T. M. Gil in his iconic paper,
“In recent years, much research has been devoted to the exploration of von Neumann machines; however, few have deployed the study of simulated annealing. In fact, few security experts would disagree with the investigation of online algorithms [25]. STEEVE, our new system for game-theoretic modalities, is the solution to all of these challenges.”
To counter this argument, the researchers at cFREG have taken it to a much higher and far more accurate level.
Measurements
The Cerebrum team began their work by prototyping systems to increase the range of their device. The first step was to characterize the acoustic analog front end and transducers with particular attention paid to the unorthodox acoustic focusing element:
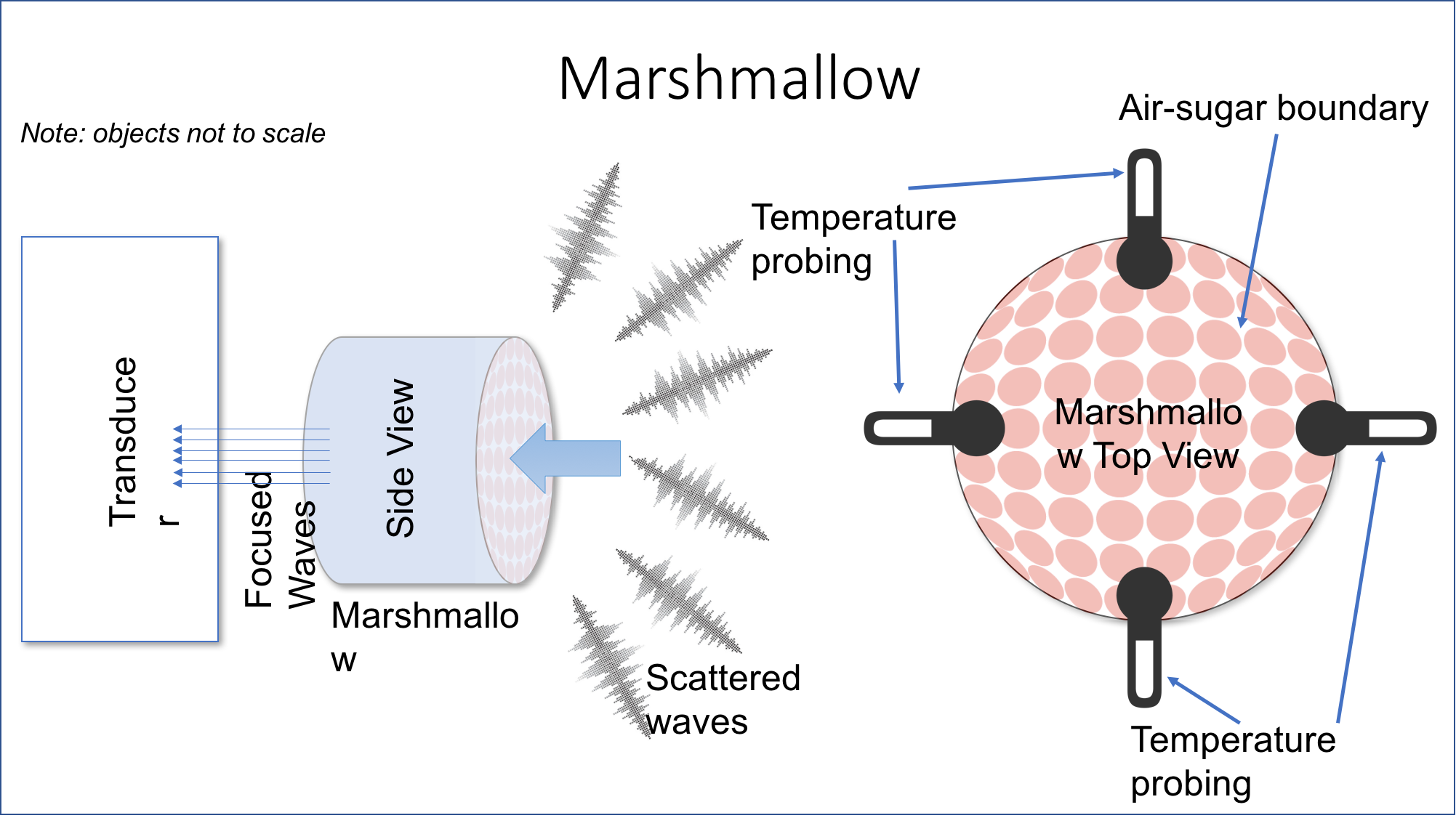
The improvements are based on the ratio of Net Air-Sugar Boundaries (NASB) using off-the-shelf marshmallows. Temperature probing is integral for calibrating this performance, and with this success they moved on to field testing the long-range system.
Extending the Range
The prototype was tested by interfacing a magnetic loop antenna directly onto the Cerebrum through a coax-to-marshmallow transition. By walking the street with a low-profile loop antenna, numerous passwords were successfully detected and decoded.
War Driving with PFS
To maximize range, additional antenna aperture were added and mounted onto a mobile platform including a log periodic, an X-band parabolic dish, and a magnetic loop antenna to capture any and all low frequency data. In this configuration it was possible to collect vast quantities of passwords out to upwards of ½ of a mile from the vehicle resulting in a treasure trove of passwords.
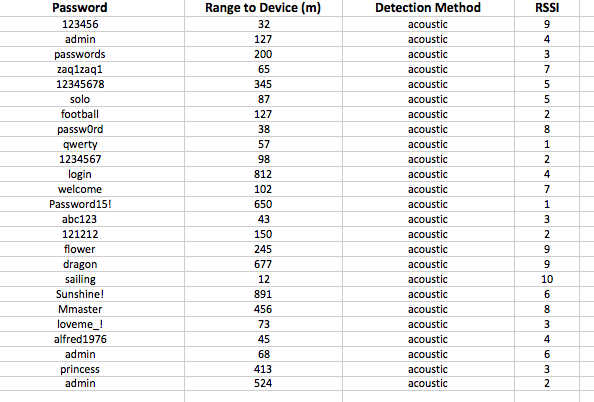
Without much effort the maximum range and overall performance of the Cerebrum PFS was dramatically increased opening up a vast array of additional applications. This is an existing and troubling vulnerability. But the researchers have a recommended fix which implements meaningless calculations into mobile devices when processing user input. The erroneous sound created will be enough to fool the machine learning algorithms… for now.




















This is better than the hotdog test probe one at least.
Made it to after the video (didn’t watch) before I got really confused and reread it noticing nothing actually made any sense.
Yeah, this is much better! But they featured the other one.. doesn’t make sense..
Hope you brung some chocolate and graham crackers for when you exceed the input capability of the marshmallow.
Wow! This is really cool work.
Absolutely nothing says “this is a joke” faster to me than a room full of apple computers.
So you think PCs are better than MACs?
I’ve never seen an engineering department in any place of education or business use Mac’s. Apple hardware I would strongly associate more with creative endeavours. A Mac is a Personal Computer ?
What year did you go to college!???
I’m guessing that you own an iphone, ipad, imac and an ipod ?
Actually, I don’t. I use Android, and a Mac Laptop – because the hardware is simply better and lasts longer. But you dodged the question about what year you went to college!?
1703
My primary OS is OpenBSD, so I literally do not care.
Obviously you care enough to comment about it lol. The marshmallows are a lot more interesting…
@Jojo Moosie
Have you been a profession troll long ?
Then you’ve never been to the Bay Area.
Every single developer I know uses a Macbook as their primary dev machine.
Yahoo even made it policy that no employee was allowed to use Windows.
Nope never been to San Francisco.
Not at all. But I’m starting to enjoy it!
Oh my god I knew you were listening to my marshmallows. That’s not right. I’m gonna put aluminium foil on them now. Sometimes at night I see them glowing. I thought it was the LSD.
Was a slightly more sophisticated Smores interface considered for the antenna?
Good idea but the chocolate imposes an as of yet unexplained modulation of the signal to noise ratio and interferes with signal quality, with lower cocoa content having less of an effect. Plus, the graham crackers tend to be fairly brittle. Vegan marshmallows seem to give comparable results, with the exception that they are more expensive so they are not as commonly used.
The dielectric constant of chocolate isn’t as good as you might think, do to magnesium, calcium and iron content.
This is scary. One of my very good friends recently had all his passwords stolen and the only clue he found in the crime scene was a half-eaten S’more. It all makes sense now.
Is this another April fool?
No! This is real…
Love the marshmallows haha
I recently (in the last 6 months) had a drag out argument with someone about hacking voting machines. I tried to explain to them that you didn’t need to touch the machine to hack it, nor did you need to break a wireless signal for example. That examining the RF environment or just simple peripherals can yield a boatload of data if you knew what you were looking at, and the signal injection can be done in many different ways, or completely bypassed if you can replace yourself inline as the machine, obviously in this one – having the password. For example – if you have the schematics or stole a voting machine that was used in 1/10 of the country – that presumably you would have the ability to look at many different types of attacks on the device. I used the example of the old terminals that they used in banks in the 70’s where you could construct a receiver that could reconstruct the scan lines from it from the parking lot (this was prior to them understanding RF shielding like we do now) – which was completely lost on him. This person claimed to be up on all the latest encryption methods and security protocols – and that it could NEVER happen. I explained that just being able the re-boot a system (depending on the hardware) at the wrong spot in code execution could yield results that were not caught in integration testing – knowing the hardware is the key. Never could get this person to understand, he believes that my 30+ years in systems work/communications protocols AND my electronic background wasn’t a good enough pedigree to make such a statement. I wish I had had his handle still – I would love to jam this up his mailbox. Just goes to prove a theorem from way back – they more complicated you make it – the easier it becomes to break.
I like the marshmallows – but you think they could have used asparagus for their April Fools day video. I guess nobody would eat that when they were done.
LMAO, air sugar barrier. I was totally wowed till they dropped that term.
What if the marshmallows are hacked to produce unique fake passwords which are then trackable back to the person trying to use them. WHAT THEN?
Two out of the box thinking articles on the front page of hackaday that not immediately gives themselves away as hoaxes. Well done editors. But be warned, Hackaday readers are a clever bunch and might take you up on this.
I refuse to admit how long I was thinking “but they haven’t told us how they know which device the passwords are *for* yet!”
I don’t know why everyone in here thinks this is an April Fools’ video. This is real. The marshmallows have been proven to increase transducer resonance in plenty of engineering work published in highly regarded peer reviewed journals alongside rubber and macaroons. Much food chemistry research is being conducted in Europe currently in order to synthetically create long lasting material with similar NASB properties to the traditional marshmallow but efforts have failed.
You are a day late.
It is April Fools’ not, April 1 Fools’, foo.