What high-tech, ultra-secure data center would be complete without dozens of video cameras directed both inward and outward? After all, the best informatic security means nothing without physical security. But those eyes in the sky can actually serve as a vector for attack, if this air-gap bridging exploit using networked security cameras is any indication.
It seems like the Cyber Security Lab at Ben-Gurion University is the place where air gaps go to die. They’ve knocked off an impressive array of air gap bridging hacks, like modulating power supply fans and hard drive activity indicators. The current work centers on the IR LED arrays commonly seen encircling the lenses of security cameras for night vision illumination. When a networked camera is compromised with their “aIR-Jumper” malware package, data can be exfiltrated from an otherwise secure facility. Using the camera’s API, aIR-Jumper modulates the IR array for low bit-rate data transfer. The receiver can be as simple as a smartphone, which can see the IR light that remains invisible to the naked eye. A compromised camera can even be used to infiltrate data into an air-gapped network, using cameras to watch for modulated signals. They also demonstrated how arrays of cameras can be federated to provide higher data rates and multiple covert channels with ranges of up to several kilometers.
True, the exploit requires physical access to the cameras to install the malware, but given the abysmal state of web camera security, a little social engineering may be the only thing standing between a secure system and a compromised one.
[via Ars Technica]

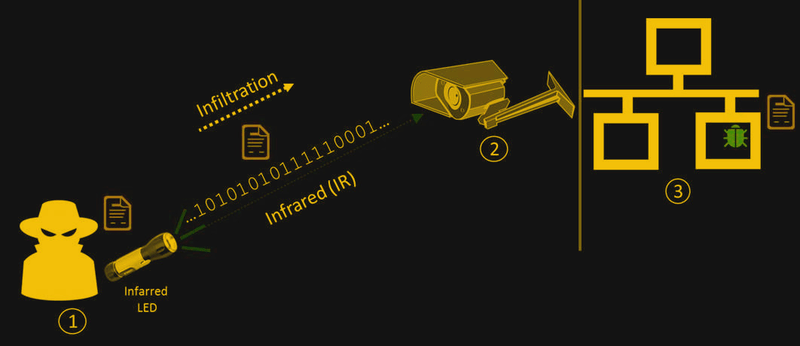














So in my mind, this is not a case of the air gap being breached, so much as being bridged. They aren’t launching an attack via the security cameras, they have already attacked the cameras somehow and are using them as a gateway or bridge into a network.
Getting something inside an air gap is easy. Plenty of opportunities for hidden installation of software as seen on this website many times in the past; your new keyboard might contain malware, and there are plenty of ways to interrupt a supply chain and get a special keyboard inside a secure facility. Usually air gapped networks are very secure because malware may be able to capture sensitive information, but it can’t do anything with the information if there is no network connection, and for more sophisticated attacks no way to control the malware once it is in place. These creative methods of defeating an air gap are important to discover.
If you are able to plant a device, then it’s also darn easy to add a radio link of some sort (in this case Rx only). So pretty pointless to use security cam path…
One can assume that the surveillance cameras are on their own separate network. Partly because the video stored can be used as evidence. But also because the video should not be disturbed by other network traffic.
This also allows you to physically reach the net by climbing on a roof, high above the ground. Then you can open one of the cameras and connect to the LAN.
sigh
But as you said, although you can do this, you have only accessed the network for surveillance cameras.
Then there are many easier ways and … above all, there are things that can give you much more money if you are so competent … and with less risk.
Addressing your disagreement with the terminology, an air gap is supposed to prevent unauthorized data from entering or leaving a network. Yes, getting malware inside the network is the first act of breaching the air gap, but using in-place technology to establish a live data connection is definitely breaching the air gap and defeating its purpose.
This is getting silly. This sort of thing passes as an easy-starter question in embedded software interviews – given ‘this’ board, how do you get debug out? Even a mediocre candidate quickly starts suggesting sideband stuff once you tell them all IO lines are used.
This is the sort of article that keeps a lab in funding, but doesn’t produce much of use.
Two complications with what they’re presenting:
Even good security cameras have a relatively slow frame rate (ca 15 – 30 fps) which puts quite a limit on the incoming modulation unless you’re using an array that presents a patterned signal at every point in time (eg, an LED/QR-code like scheme). From the article’s abstract: “Data can be covertly infiltrated into an organization at a rate of over 100 bit/sec per surveillance camera from a distance of hundreds of meters to kilometers away.” Um, no…not from a single source. Nyquist is spinning in his grave.
Outbound data is astoundingly slow. From the article’s abstract: “Our evaluation of the covert channel shows that data can be covertly exfiltrated from an organization at a rate of 20 bit/sec per surveillance camera to a distance of tens of meters away.
20 bps ~ 2 baud. Really. This could get you the day’s passcode, but if you’re going to exfiltrate the drawings for the latest jet engine, bring an air mattress and a cooler….you”re going to be there for some time.
We’ve received high resolution photos from space probes with very slow data rates (we’re still receiving photos from the Pluto flyby last year) it just takes time.
to save some google time: New Horizons had a downlink to earth of about 1 to 2 kbit/s and 8 gb Pluto photos took about 15 month.
One could up everything by having different cameras transmit different things.
Holding up QR cards or a screen with compressed visual data playing on it will be orders of magnitude faster since they’re using a 2-d screen to recieve linear, binary data at very slow rates. This also presumes nobody wonders what the heck you’re doing..
I have to agree. If you can sneak malware in you probably have opportunity to exfiltrate data much faster by sneakernet.
You’re presuming the data you want to exfiltrate is already there and is unlikely to change over time.
Hide a micro SD card in the sole of your actual sneakers.
Or just burn it on CD’s and carry it out openly. ;)
But very few actually record footage at this framerate, it’s usually more beneficial to have less frames which actually have enough resolution to show the perpetrator clearly then a bunch at crap resolution.
You also have to keep footage for some time for it to be useful, so unless you don’t mind using a considerable part of that datacenter for storing all that, 30FPS is the max you want to use.
Since the exploit is running on either the camera or the system to which the camera is feeding raw images, the storage rate is pretty meaningless, the data transfer can still utilise the frame rate of the camera.
Which is usually set between 5 – 30fps set in the camera itself.
3k and 4k cameras are becoming common mow, so there are network congestion considerations on multiple camera installations too, the bitrate and fps is set in the camera to alleviate congestion rather than the camera just pumping out frames as fast as it can and leaving the recording device to sort it out.
But if you have physical acxess to the camera, somehow across the airgap, then you can set it how you want anyway.
But if you can access the camera on the network, you can probably access any device on that network too…
You’d think a modern system would do slow updates until it noticed activity and then switch to high framerate.
But hey it’s only 2017 and that kind of fancy technology is for the future…
Ummm, Jezzz. I feel violated, just when you thought it was safe. Next thing will be your coffee cup sending data, and yes – I’m sure that has been done too.
Nano-bugs that look like coffee grounds. Normal preparation, drink, listen, poop/pee, filtrate, ???, profit!!
Shooting microwaves at foam cups to make them resonate as an audio bug is a thing apparently……
If there’s any communications that go through the walls of a building containing supposed to be secured computers. it’s not completely airgapped. Phones, wired or any sort of wireless. Anything with a microphone, any cameras. Keep it all out.
Inside you have the isolated computers and the people using them.
Nobody gets to carry any data storage media in or out other than the persons in charge, persons for whom it is their interest to not have any data leak to other people.
If there must be security cameras inside, then their video storage should be secured inside with them, the camera system should not connect to any computer, and every piece of hardware in the camera system should have firmware (if it needs firmware) on chips that are not reprogrammable.
Another fix have some analog security cameras as well and keep the DVR or even some old fashion VHS VCRs somewhere safe that few people have access to.
So all you need is a planted person with a photographic memory, pwned!
note: I used that last word because it’s amusingly archaic (to me)
Intereseting article. Good find, Dan.
Your text contradicts the illustration and only “addresses” half of the story.
what kind of designer set the IR leds to be controlled by the camera software to begin with?
tap voltage, run a CDS cell to turn them on at night, done. no reason to have a data path.
My garden variety camera has CDS and there’s a setting in software to manually turn it off and on (there can be valid reasons for doing so).
israeli & USA intelligence was able to blow up Iranian nuclear facility using virus (https://en.wikipedia.org/wiki/Stuxnet) that broke their machinary pushing them over the security limit of speed og the internal engines. Iranian Nuclear Project was retarded by years without shot one sigle bullet.
in ‘eighties Israeli bombed the nuclear plant of Irak (https://en.wikipedia.org/wiki/Operation_Opera), but agaist iran, they used no bombs, only mind.
From this kind of people (israeli &USA) you can espect a lot of tricks. You can never be too much paranoic, because their attack can came from every side: webcams, keyboards, usb stick, etc. Everithing that has inside a chip, is a possible vector to attack your network.
To be offline, is not enough. severe policy for workers is not enough. Paranoid mind is not enough. you need all of those togheter (offiline, policy, paranoic) to be able to protect yourself form cyber attacks.
The main problem is that security is “heavy”: many limitations, many controls, etc. And uman beings prefere “fast and easy”, over “secure”. And taking in mind that Manangement never take care of of warning caming from IT technitian, the topic “we was attacked with success” is just a matter of “when”, not “if”.
They didn’t blow it up, this is a vast oversimplification of what Stuxnet did. Nothing blew up, but sensitive machinery failed.
What Stuxnet was meant to do was modify the settings of centrifuges used for uranium enrichment. By slightly speeding up then slowing down the centrifuges repeatedly, they could damage the equipment eventually causing the centrifugal tubes to expand and then come into contact with one another.
i have an objection to your narrative that you might consider obtuse but which i consider fundamental to understanding the nature of power.
the idea that stuxnet did not involve the firing of a single bullet is an inaccurate whitewashing. the simple narrative is true as far as it goes: stuxnet was created by people typing on computers (not firing guns), and then carried into the industrial supply chain through an unknown (?) but likely not immediately violent mechanism. but that’s only a tiny part of the story. every step of that activity was made possible by american military conquest. industrial supply chains are defined not only by the law of supply and demand but by the conduct of war (past and present).
in some very abstract sense, obviously all modern human endeavor builds upon a violent past. but we do not need to be abstract to see that it is not analytically useful to distinguish the CIA’s “non-violent” actions from the extremely bloody history of the cold war which they have been almost synonymous with for their whole history.
At most secure facilities, the security cameras wouldn’t be connected to either the secured systems inside, or the outside world, They are going to be on their own independent setup, and if it’s of any age, it’s going to be analog cameras, connected with coax, to an analog or possibly digital recording device.
Even a newer system, you aren’t going to use wireless cameras, and the camera’s wiring isn’t going to be allowed to touch the wiring of the other systems. These places use ethernet cable colors as a code, different systems use different colored cables, and you absolutely aren’t allowed to substitute. The cameras would have their own independent wiring pulled through the walls at installation, that just goes from the cameras to the recording and monitoring setup, and the recording system wouldn’t be connected to anything sensitive.
Sorry if that rambled, it’s late.
Some of that may even be fiber just to make certain there are no leaks, not even through ground loops.
If I can get malware inside, I have an excellent way to get data out; modulate the rate of mantainence issues by creating additional ones. You can then simply sit outside watching the workers at the end of their shifts for how grumpy they are. You can get almost 1 bit per day out, plenty to get a password before it’s changed at the start of the next month.
+1 dan
Mood Modulation
I have installed a lot of security systems over the years in large companies and really I fond them to be a joke.
The only security systems I like and were good were the ones at the casino’s. I just liked what they could do.
Way to computerized. I think that there could be a lot of ways in, But I think that would be a real hackers job.
I one hospital I did I told them that there lighting system could be hacked and I even showed them.
Your thinking lighting ( I could have fun with that. It harmless right.) well I would not want to be on the operating table at the time then. I don’t know why but the surgical lights were even on the same system. I was so so mad..
Man I really really mean It was easy. I showed them and I’m not a very good programer. If you could program a Arduino you can take over the system.
OHHH The Stories I could tell. Would make you say holly sht.
Oh for got to say I like the pictures.
And yea I know I should proofread better before I post. So So sorry.
It should say “The one hospital I did.”
So So Sorry again. I will try harder next time.
Not sure I’d put my security system installment in the hands of someone who can’t tell the difference between ‘there’ and ‘their’, nor the difference between ‘your’ and ‘you’re’. And who types ‘forgot’ as two words.
Not for snobbish reason, but because some minor code and configuring has to be done on such system.
Oh K Thanks like I said I will try better.
Made an error myself too by dropping the last s of the word ‘systems’. Oh well.
https://youtu.be/j4hvh5e8-nw
Chill out man. Not everyone here are native english speakers.
A laaer through a mask to encode, end the video file into the image, stops the dvr recording without killing the camera.
Happy to be a tetrachromat. If it’s slow enough for morse code who needs a computer.