For most people, calculators are cheap and simple devices used for little more than addition and the odd multiplication job. However, when you get into scientific and graphical calculators, the feature sets get a lot more interesting. For example, [Ready? Z80] has this excellent explainer on how HP’s older calculators handle infrared communications.
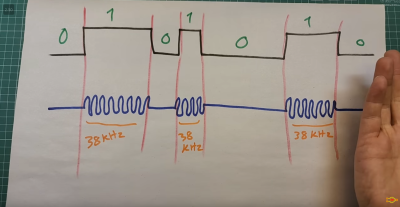
The video focuses on the HP 27S Scientific Calculator, which [Ready? Z80] found in an op-shop for just $5. Introduced in 1988, the HP-27S had the ability to dump screen data over an infrared link to a thermal printer to produce paper records of mundane high-school calculations or important engineering math. In the video, [Ready? Z80] explains the communication method with the aid of Hewlett-Packard’s own journal publication from October 1987, which lays out of the details of “the REDEYE Protocol.” Edgy stuff. It’s pretty straightforward to understand, with the calculator sending out bursts of data in six to eight pulses at a time, modulated onto a 32.768KHz square wave as is the norm. [Ready? Z80] then goes a step further, whipping up custom hardware to receive the signal and display the resulting data on a serial terminal. This is achieved with a TEC-1G single-board computer, based on the Z80 CPU, because that’s how [Ready? Z80] does things.
We’ve seen other great stuff from this channel before, too. For example, if you’ve ever wanted to multitask on the Z80, it’s entirely possible with the right techniques. Video after the break.
Continue reading “How HP Calculators Communicate Over Infrared”