Every once in a while you get lucky and a piece of cool gear lands on your bench to tear down and explore. On that measuring stick, Kristin Paget hit the jackpot when she acquired a fascinating piece of current generation cellphone infrastructure. She’s currently researching a carrier-grade LTE eNodeB and walked through some of the findings, along with security findings of two IoT products, during her talk on the Laws of IoT Security at the 2017 Hackaday Superconference.
Evolved Node B (eNodeB) is the meat and potatoes of the LTE cellular network. It connects the antenna to backhaul — this is not something you’d expect to see on the open market but Kristin managed to pick one up from a vendor at DEF CON. Hearing her walk through the process of testing the hardware is a real treat in her talk and we’ll get to that in just a minute. But first, check out our video interview with Kristin the morning after her talk. We get into the progress of her eNodeB research, and touch on the state of IoT security with advice for hardware developers moving forward.
In the interview Kristin mentions that WiFi is certainly not the most secure choice for connected devices and she definitely drives this point home in her Supercon talk.
The first of three hardware devices she takes on is a WiFi connected lightbulb. We’ve all done the dance with WiFi connected “smart” items: connect to its AP with your phone, load a webpage and type in your WiFi credentials to the “Thing” can get on your AP. In this case after you enter your WiFi credentials the lightbulb got on the network but continued to serve up it’s own AP — with a easily searchable default password. Of course the issue being that your WiFi credentials are served up in plain text on the lightbulb’s config screen so anyone in range can get to your home WiFi credentials. Brilliant.
The Laws of IoT violated here are easy to understand and apply almost universally. Don’t hand out plain text credentials. Choose to use unique provisioning credentials so not just anyone can get to the config interface. Separate user privileges from owner privileges. And don’t leave the provisioning AP up once the device is connected to the target network.
Next on the chopping block is a first generation Amazon Dash button. These have been favorites for hacking since they came out. But of course Kristin isn’t going to be happy with watching the router for the MAC address to appear. She walks through sniffing traffic on the button and dissecting the certificate validation used. The surprising find is that all of the first generation Dash buttons expect SSL with an expiry in 2015 or they won’t work. Designers need to include a way to refresh keys or users will end up locked out of devices in the wild. Dash solved this just by dropping all of the SSL security used.
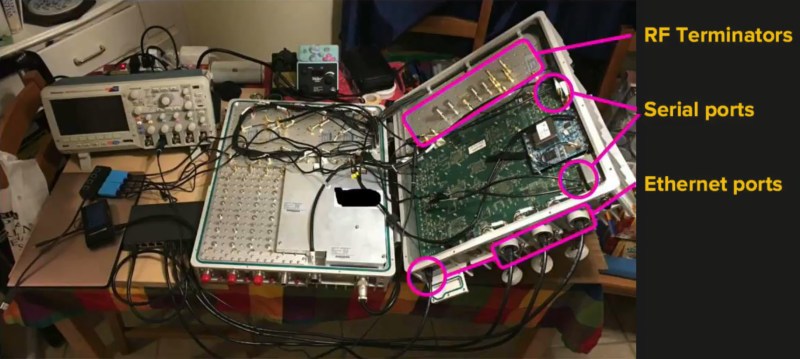
This brings us to the juicy part of the talk: the LTE eNodeB. Since this is carrier grade, this is designed to be in use for 10 or more years and in this case is a software-defined radio ready to upgrade as new technology emerges. Getting into the OS is almost comical: Kristin found the bootspew on one of the serial ports and realized it was running uBoot. How did she realize that? The boot process gives you a 5 second countdown to enter it with a keypress. Dropping into uBoot made it easy to start a shell and Kristin’s inspection of /etc/passwd included hashes and multiple accounts that shared UIDs. It’s a delight to see how she worked through all of this.
The first step to designing more secure hardware is to understand the mistakes that have become all too common. From simple and cheap lightbulbs to elite infrastructure, Kristin makes an excellent case that we as hardware developers must be codifying and following a set of IoT security laws to make connected hardware work for us as an asset and not a liability.
















This is the kind of stuff I love watching talks about
Wow, me too.
I want to learn more about this stuff.
It’s a shame this kind of hacking isn’t so common. I’m the only person at my makerspace into this stuff.
Sure. The bootloader on tiny cheap home router is encrypted to “protect the wifi spectrum” and similar bullshit. But 4 100W radios? No need to protect it – who would be interested in that???
It’s physically protected – if you can’t even get to where the box is located let alone open it/connect to a serial port/reboot it, then it’s fine.
“It connects the antenna to backhaul — this is not something you’d expect to see on the open market”
Anything like Stingray? As for the uBoot access, there’s that whole “whomever has hardware access, has root”. Good for a sneakers type movie with people breaking into base stations.
“Physical access > all security” is a rule of thumb, but with on-chip and between-chip encryption, it’s not 100% true any more. Even with noxious acids, laser beams, and really thin bits of wire, there’s still limits. I don’t fancy anyone’s chances against, say, the Intel IME by drilling holes into the chip. Most chip hacking seems to be against 8-bit level stuff fabbed with chunky processes.
The IoT stuff is legit bad, no argument. But the stuff about the LTE node is just FUD, analogous to saying “look guys, if I hold this button down on this cisco router, I can get it to reset the password and let me in!!111!1one!11!”. Now, show me a remote execution exploit, and that’s another matter entirely….
Still, there must be plenty of base stations in the middle of nowhere, where a ladder and a long cable will be all you need to connect physically. Then you’re on the inside of the network. There might be a lot more remote stuff you can do to other nodes, once you’re controlling a legitimate one.
Don’t even need a long cable either, just prepare a esp8266 with the old school wifi-serial firmware. Take a couple of minutes to install it. Then access it whenever. Potentially scary stuff.
Not that strange to have root access on an eNodeB. Some models even provide SSH, for running testing or debugging software etc.
Also not that strange to be able to buy one second hand (or new, but it would be quite expensive). In some countries you may not be allowed to own it without license to the frequency space or some kind of dealer ‘holding’ license, in some you may have it but not in a ready to go state, but in most you can just not turn it on.
Connects the antenna to the backhaul? This sounds more crappy than the Bollywood movie dialogs. What BS is this.
I suppose by “antenna” it means “local cell site”.
Even of root access maybe possible, getting past the LTE protocols is going to be a near impossibility. You just end up getting access to the equipment side not the LTE.
Physical access trumps everything.
This is still just the RAN segment. Or worse, has not protocol stack in it at all and just backhauls the demodulated RF to a separate protocol unit.
So no EPC or other protocol segments required for running your own LTE network with it.
And now to implement in SDR, this is great hacking these rare to hands on for non-NDR signers systems. Does current restrictions permit the SDR signaling rate required?
I have considered the impact of leaving a console port open. In fact, during this talk, my thought immediately turned to the TS-7670 which my workplace uses in its low-end gateway devices. These things boot of SD cards (removable) or NAND (older revisions)/eMMC (rev D and later) flash.
The official firmware image uses the Freescale bootloader, but we opted to port U-Boot to ours. The upshot being, yes, you can totally pwn one of these devices. However, you need to be there. The rule usually is, once an attacker has physical access, it’s game over. Most devices are not resistant to the evil maid, and these things are no different.
Pop the cover, and you’d see it’s a TS-7670 inside with a bog-standard Freescale i.MX286, and there’s a helpful jumper that switches between booting internal flash and the SD card… and since you can BYO SD card with any code you like … well… I didn’t see a lot of benefit in delaying the inevitable.
Once these things have done their tour of duty in whatever application you care to name, at some point, they’ll find their way likely into the hands of some aspiring hardware hacker. The schematics and code are out there, why not let them re-purpose that box how they wish?
The interview seemed to completely miss the real nature of IOT threats. The major threat is not someone gaining access to a few IOT devices on your wifi network. With a few exceptions, such as alarm systems, the value to a criminal is not high enough to be worth the effort. The real problem is when thousands or millions of IOT devices are compromised. As most IOT systems involve passing the data and commands through a central cloud service, there is a real threat that someone could take over, say, every Amazon device. Although centralized systems tend to be better protected than local systems, they are not perfect and there is a huge incentive for malicious players to put a huge effort into attacking them. A remote firmware update mechanism would be a great attack target.
If you study the design of castles you will see that security requires using a diverse array of mechanisms in a layered approach. It also requires a segmented architecture to limit the scope of an attack. It should require just as much effort to break into the second castle as the first.
So, IOT security, and equally importantly resilience to failure, is primarily a systems architecture problem. First, IOT systems should be decentralized. The Internet should just provide the plumbing. If you send a command to an IOT device you own, it should go directly to a server (e.g. home control hub) or other device fully under your control. Centralized cloud based systems not only lack resilience but also compromise privacy and hand over control to others.
Secondly IOT systems should be layered, with each layer providing additional security. I use multiple dedicated IOT networks in my home. The first rule is to have IOT networks that are separate from your regular home network. They can share an entry point but ideally even that would be separate. First I have a dedicated locked down IOT router to connect the home hub to the Internet. Then there are multiple dedicated IOT networks for subsets of IOT devices so that, for example, the home security system is separate from the lighting system. Then there are more dedicated networks for individual IOT components, such as individual IOT switches. These connect to the subsystem networks through IOT coordinating devices that both provide the logic for object collaboration and act as mini-routers providing further security and isolation. Wifi networks are cheap and relatively secure even with the WPA2 vulnerability.
There is a lot more to IOT security, privacy and resilience than that. I haven’t touched on the importance of open software or software and hardware diversity and many other topics.
It is important to understand that it is a system architecture problem that has come about because of the way that Venture Capital works. In order to make zillions of dollars, they require systems to be highly centralized so that they can vacuum up your data and have control. It is much harder for a single business to make a vast amount of money from open, diverse, distributed systems.
Having tried i can now testify that with the professional services of spymasterpro3x(at)GEEmail(dot)com you’ll be able to exercise commands on the Targets device unnoticed and undetected. You will also have access to view all the target’s information including communication data like sms messages, KIk, WhatApp and other social media apps in a secure control panel that’ll be on your phone. It’s time you stopped circling the idea of infidelity and get to the bottom of things. Send a mail to spymasterpro3x(at)GEEmail(dot)com stating your complains.