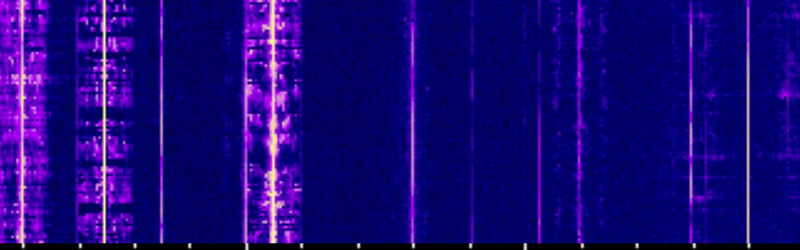
Identifying ham radio signals used to be easy. Beeps were Morse code, voice was AM unless it sounded like Donald Duck in which case it was sideband. But there are dozens of modes in common use now including TV, digital data, digital voice, FM, and more coming on line every day. [Randaller] used CUDA to build a neural network that could interface with an RTL-SDR dongle and can classify the signals it hears. Since it is a neural network, it isn’t so much programmed to do it as it is trained. The proof of concept has training to distinguish FM, SECAM, and tetra. However, you can train it to recognize other modulation schemes if you want to invest the time into it.
It isn’t that big of a task to identify signals using your built-in neural network. However, this is a great example of a practical neural net and it does open the door to other possibilities. For example, automated monitoring of multiple channels would need something like this.
One interesting tidbit is that the neural network doesn’t really know what it is learning, so input samples could be IQ samples, audio, or even waterfall graphics. You just have to use the same input to train that you want to use during operation. In fact, the code apparently started out as an image classification network from a course by Stanford.
If this gives you the urge to go out and buy an RTL-SDR dongle, you might want to look at some reviews. What else could you do with an intelligent radio? We’ve already seen a different kind of neural network decode Enigma traffic.














Wow, Randaller beat me to this with the COTS RTL-SDR. Awesome job Randaller!
I was going to perform similar to my NIR work ( http://www.americanlaboratory.com/914-Application-Notes/767-A-Novel-Tool-for-Searching-Sorting-Copying-and-Managing-Spectra-Files-for-Use-in-the-Development-of-Individual-Discriminate-Partial-Least-Squares-Material-Discriminators/ ) … though haven’t really been collecting signals data yet as I am still improving on my hardware system for calibration of the other systems. Impressive and thanks for sharing Al!
Before I was armed robbed and later my truck and office stolen in Utah… I was working on converting the NIR apps into C++. C# would have been easier, though at the time I wanted in C and if I had the time to learn assembly… would go that route now days.
Awesome work! Keep the code flowing! Someone can even try to code other discrimination or pattern recognition algorithms to see what works best if wanting more strict validation.
Office on wheels maybe. Sad to read that:(
Thanks ytrewq.
Worse is complaining over the years and being a victim and watching people close to me be forensically clean to most murdered.
The legal abuse syndrome and criminal operations that are pathological habitual false pretense malicious intent to destroy personality and property and murder though will act all cute, sweet and innocent incest narco sexual deviant pedophile two face back stabbing neutering acting like they’re invasive nuisance species inbreds who are no way allowed to be my or really in my opinion anyone’s guardian, parent, warden, trustee, power of attorney, have letter of authority, executors of estate, government official role or have anything to do with my or my families or associates that aren’t victimizing anyone’s life.
Very strange to me, though I was warned growing up that our neighbors were cocaine heroin pedophile drunks that were mentally ill and criminal though I didn’t realize they were so mafia style official looking that bad. I see now why the Whirlpool Executives had to move to other communities and why birth rates went down and even one of the elementary schools was demolished as was in the neighboring communities.. Disturbing being back here in Coloma working on restoring my parents old house. Here they won’t be so Chicago style bad COP that isn’t there in Chicago as much anymore since here they want the neighborhood to look clean. It’s like a community of vultures that stalk anything around me because I looked at them and actually could earn a living legally validly as most around me in certain environments.
They’re ethnic or anything, though they won’t admit to your face much, cleansing neuters neutering too with Ultrasonic,RF, Microwaves and more like the Cuban Embassy assaults is speculate and have collected some ultrasonic and sonic evidence. http://dewdetectionprojects.blogspot.com/2017/10/noticed-oscillations-on-me-decided-to.html
Correct, the mobile office as I would call it. Since the “Mission Control” and other files were on the desktop, laptop and my briefcases. I had my first brief case my Dad, who since passed, got me along with other items in the truck also with my baby book, history of paychecks, tax history and receipts for payments that I’ve had a history of in Michigan those I’ve paid attempting to make false claims. Had some FOIA Requests, hunting, fishing and camping gear and a Honda 1000W generator as well as Marine Deep Cycle battery and charger. Few $1000 in equipment and gear as well as the office. I even had a USB scanner in there so I could scan documents if I was at a library or courthouse or installation. Went out to complain to other U.S. Federal District Bases and Headquarters in person and was harassed only in two locations thankfully with the last location in Utah where all was stolen. Some items were robbed from me in North Dakota.
Utah has strange laws with vehicles also and I’ve found that after 30 days notice the vehicles in most all states can have a salvage title created and legally stolen even with false pretense perjury malicious intent to destroy personality and property criminal acts like you have to hire an attorney and for some reason denied U.S. Constitutional, Statutory and Administrative Pro-Se Rights. Talk about legal abuse syndrome as in a book I read about LASD.
Strange… then my Dad died Easter Sunday 2015. Of which I went out west to complain about the Perrigo and Berrien County Sheriff’s and other Meth, Cocaine, Heroin and other Nationalities Cartels and Mafia’s now looking official compounding and concealing their serial killing mass murdering unreasonably continuing criminal enterprises (Benton Harbor, Allegan ,Coloma, et.al.) of mafias, terrorist cells, WWI/WWII prisoner of war camp criminals descent and pedophile satanic cohorts operations.
Thankfully, I am making progress with my Congress People since everyone else is so malicious intent to destroy personality and property if not forensically clean murder using MCL 750.200h&i, 750.224a and 750.543p devices if not kinetic devices.
Someone at Central Wesleyan Church did mention take all my cases directly to the State of Michigan Supreme Court since most others are malicious. I’ve found some prosecutors are for certain beyond a reasonable doubt with a preponderance of evidence and others are not.
Does this allow actual decoding of sound / audio of digital signals my understanding is that it does not it just tells you the modulation scheam in if it does decocode audio technically encryption would not be efficient any more than as I understand it?
I assume it does an FFT (of the raw IF stream?) and compares it to known samples for the closes match.
I wonder where they get the comparative samples though, I tried to find some info on signals I did not recognize and even on dedicated sites you only find a subset of what you come across on the air. And info is sparse for anything not part of the 5 or 6 main ones.
Anyway it’s a very clever use of neural networks I think, because it can be a bitch to know what you are dealing with – as I indicated.
I haven’t analyzed and validated the method, data sets or code yet… have other projects and stressors. I doubt there is any demodulation let alone decryption or de-multiplexing.
Was thinking I’d post this thought while I have on my mind. An additional open source algorithm integrated for processing the de-modulated stream once modulation was determined for optimal signal and audio sampling rate. I’m guessing is performed somewhere already… though not so open source observable and if so, please point to the reference from this article.
I think the source is encrypted and run thru tunnels and vpns plus Tor so tracing is damn near impossible. But the audio is audible to a certain frequency and random people can hear what’s all going on but can’t no one do shit about what’s being transmitted and received. I come from a hostile environment and I know neural networks with facial recognition , speech recognition and deep learning can detect people and objects and even tell when your lying or about to lie and whoever set this up can save data, audio, video, even lidar images. It’s crazy. Only select few know about this stuff. And with the ham radio embedded I. And an antenna shoot you in the game ! Broadcast lover airwaves and using the right frequency people would just think they are crazy or hearing voices that aren’t real. When in facts it’s all to real and the frequency used is only audible barely to the brain. Like a voice in your head
Nothing new here. This is old hat to any 35N at one of the 3 letter intel agencies.
“Since it is a neural network, it isn’t so much programmed to do it as it is trained. ”
With the current neural network applications and models, it is proramming but rather indirectly.
Reason being, when the neural network is deployed in the application, it is fixed in its connections and therefore forms the equivalent of a fixed algorithm or a program – something which you could (and some argue should) come up with by manually typing it in – which would have the added advantage that you’d actually understand what the code is doing.
The training of the network is simply indirect programming, broadly equivalent to hammering your keyboard at random and testing whether the resulting code a) runs, b) produces the desired output. With neural networks, the system just converges to your desired solution faster – assuming your testing criteria are exhaustive enough to leave no “bugs” in the resulting algorithm.
Typing in the almost same code over and over until you have a good match to various signals in various state of noise would work, except it would take hundreds of years instead of seconds, but meh, real men code in notepad and take a few hundred years am I right?
Yeah. The point is that “neural networks” as they are currently employed isn’t so much different from programming. It’s just a faster way to throw shit at a wall and see what sticks.
If you knew what you were doing, you’d write the algorithm yourself rather than have a training function stumble upon it.
Other manual training set methods would require another algorithm to input the discriminated specification signals back into the sets and re-calculate with the models where the unknown would have to be reviewed and determined what they are identified as then a model created or labeled in a single model method..
Been doing this using Tensorflow and IQ samples and getting diagonal confusion matrices with 128 IQ samples for all signals of 4 kHz and narrower for two years at Virginia Tech. PhD student just published thesis on this work. We are moving to networks learning “how to communicate” optimally on a channel given marked data. Part of the same thesis. Look for Tim O’Shea on arrival.org. Bob McGwier, N4HY
Arxiv.org not arrival.org
In coming years, we’ll hear some OM on 160 grumbling….
“Bah…. get off my confusion matrix”
Yeah, I had to look it up. Still confused a bit about the confusion matrix. I guess the best description is…a fuzzy truth table?