As long as there has been radio, people have wanted to eavesdrop on radio transmissions. In many cases, it is just a hobby activity like listening to a scanner or monitoring a local repeater. But in some cases, it is spy agencies or cyberhackers. [Giovanni Camurati] and his colleagues have been working on a slightly different way to attack Bluetooth radio communications using a technique that could apply to other radio types, too. The attack relies on the ubiquitous use of mixed-signal ICs to make cheap radios like Bluetooth dongles. They call it “Screaming Channels” and — in a nutshell — it is relying on digital information leaking out on the device’s radio signal.
Does it work? The team claims to have recovered an AES-128 key from 10 meters away. The technique reminds us a bit of TEMPEST in that unintended radio transmissions provide insight into the algorithm the device applies to encrypt or decrypt data. Most (if not all) encryption techniques assume you can’t see inside the “black box.” If you can, then it’s because it is relatively easy to break the code.
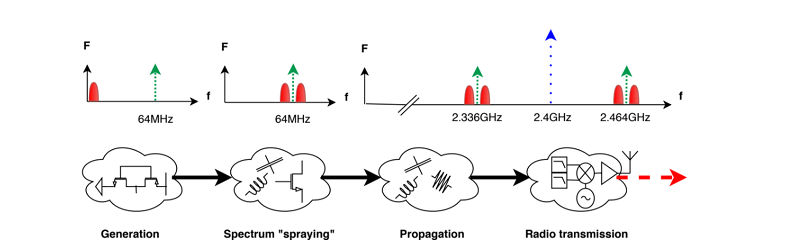
Some simple experiments (and knowledge of the device’s clock frequency) allowed the team to visualize the difference between encrypted data and non-encrypted data. Using software-defined radio techniques, they attacked a Nordic Semiconductor nRF52832 device in which they were able to easily find the part of the signal that corresponds to a single transaction. Some work had already been done on recovering a key when an attacker can measure the power using something like ChipWhisperer, and the team was able to leverage that work. Unlike ChipWhisperer, however, Screaming Channels doesn’t require a physical connection to the device.
Oddly, this isn’t as new as you’d think. A WWII-era Bell researcher noticed that he could detect the crypto machines operating from a distance by looking at noise on an oscilloscope and could read the text the machines were handling. Once they proved this was a real threat, they devised a cumbersome and difficult-to-deploy solution. The Army was too busy fighting a war, so they simply directed forces to keep the area around the crypto machines clear to prevent this kind of attack. Eventually, though, crypto machines would be shielded to prevent just this sort of attack.
The problem is now you have everything on one chip that you need to make for a few pennies. Protecting against this attack will require quite a bit of redesign and possibly separation of RF and digital data circuitry. Or, the market could do as the Army did and just decide to accept the risk.
We will probably see a lot of reinvention of security principles as more people who don’t develop secure systems try to do it anyway. The market may yet ignore low-risk issues, too. After all, many phones have fingerprint scanners even though those have been hackable for more than 15 years.















Security decisions are often a compromise. I use a fingerprint because I’m more at risk from shoulder-surfing by the kids than someone serious enough to print fake fingerprints.
Ever see that Robert Redford movie SNEAKERS? Cool movie. But I hear facial bio-metrics is promising. But for high security ops you need a multiple suite of bio-metrics and passwords. Making our lives easier is NOT conducive to good cyber- or site- security. Its annoying but necessary. I also would push for ambush-codes too. A clever way for the ambushee to obscurely notify security you have been opsec compromised without letting the ambusher know right away (or ever).
To block attacks like this is not easy – You would need to isolate the digital section with ~221dB of attenuation (Johnson-Nyquist noise for 1Hz bandwidth @ 300K is -174dBm. Dropping the temperature of the first RX LNA from 300 K down to 0.006 K could increase the sensitivity by an additional 47dB). If it is a 3.3 volt chip you would need an additional ~23dB of attenuation, or ~14dB if it was 1.2 volt device.
The cheapest solution is if it involved the highest level of security is not to use RF.
Pretty impressive approximations, would you mind sharing how did you came up with those numbers?
He pulled them out of his butt – just like the authors of the alleged paper. Without a working piece of hardware for “peer review”, it’s nothing but vapor-ware. Cracking an AES128 bit key ? (in a reasonable amount of time using COTS equipment?). I call shenanigans!
So application of Boltzmann constant, is “out of his butt” ? I’m just looking at the current (cooling) technology that exists today, it is extremly exotic (¥¥¥/€€€/$$$/£££) and no where near COTS. If you want to protect against COTS equipment, then you are not really looking for security at all.
It’s called a “spec sheet” copy & paste…
However, intro to Faraday basics in indicated here. But the last sentence is 100% true!
Lookup “Johnson-Nyquist noise”, every resister generates noise, which is dependent on bandwidth and temperature. The higher the temperature the more noise, the larger the bandwidth you are looking at the more noise you will see. The rest is just basic maths.
Basically I when what is the most sensitive RX device that could be made in theory using the laws of physics and the lowest temperature achieved (0.006 K). And then what is required to drop the signal levels radiated from the device that is being spied on to below the noise floor of such a receiver. The RX device is not a very practical device, it is only looking at 1 Hz of bandwidth and it needs the very first gain stage cooled to (0.006 K) which is difficult.
But the end number is totally crazy, every 3dB of attenuation drops the signal level by half, so ~221+23 dB would be attenuating the original signal by a factor of ~2,417,851,639,229,258,349,412,352. Once numbers get that large it is very difficult to comprehend.
Might be more feasible to put generated noise above the leak.
Actually, to be a clever SOB , now knowing this info, one could think outside the box and figure out how to think like Geordie LaForge in ST-TNG. Just figure out how to generate cyber-psuedo-background chatter (i.e. faux-noise) that “appears” to be legit traffic but is just a fake-out maneuver for Camurati (and other Van Eck Phreakers) to listen to on their o-scopes. Didn’t Geordie figure something like this to defeat the Borgs? Maybe not but close enuf’ :-P
The problem with adding noise is that it needs to be above the signal level that you are trying to hide. And if you look at the paper part of the leak from the digital side to the analogue side of the circuit is going to effect the jitter of the voltage controlled oscillator. The phase shifts of the intended RF emissions, could leak digital information. Maybe add a clock jitter attenuator (DSPLL).
Pretty much can’t avoid EM propagation when transferring information. You could use gravity waves. I guess it is kind of expensive and the bandwidth is going to be in the audio range, so probably going to be back to dial-up data rates.
Never could understand how this type of Star Trek (TOS) technology could be viewed as “safe” cyber-wise and health-wise. A microwave transmitter this close to your head? Even if it is just a flea-watt. Then the thing Wim van Eck exposed in 1985 should have convinced all of you post-Trekkies to stick to harder target hard-lines (wired ear buds) and forget BlueTooth dongles dangling from your ears like some later-day Nichelle Nichols (aka Uhura) – including Spock and other bridge crew. No wonder it was so easy for Romulans (et al) to penetrate Star Fleet OpSec. :-D
https://i.pinimg.com/originals/ab/94/d9/ab94d9a665134da371436c0a91eec58f.jpg
And you wonder why 99% of certain clearance level systems are supposed to be hard line based. I’m thinking they can be fiber optic by now like everything else can be???
Basically, just need to make micro Faraday Caged layers with micro Anechoic Chambers I’m thinking with opto-couplers with a vary narrow line of sight if wireless, fiber optic or wait… just make sure the output of the caged chambered system is the wireless transmission signal if need be. Securing the processing box to TEMPEST standards that I still need to read into I’m thinking in micro size is a future objective that I’m sure the NRO/ODNI clients aren’t going to like anyone else to have. Like I’ve heard the 6″ coaxial cables NASA uses are way shielded. I’m thinking power lines can be way more shielded also… talk about WTF radar potential.