Earlier this month a single person pleaded guilty to taking down some computer labs at a college in New York. This was not done by hacking into them remotely, but by plugging a USB Killer in one machine at a time. This malicious act caused around $58,000 in damage to 66 machines, using a device designed to overload the data pins on the USB ports with high-voltage. Similar damage could have been done with a ball-peen hammer (albeit much less discreetly), and we’re not here to debate the merits of the USB Killer devices. If you destroy property you don’t own you should be held accountable.
But the event did bring an interesting question to mind. How robust are USB ports? The USB Killer — which we’ve covered off and on through the years — is billed as a “surge testing” device and operates by injecting -200 volts DC on the data lines of the USB connection. Many USB ports are not protected against this and the result is permanent damage to the computer hardware. Is protection for these levels of abuse necessary or would it needlessly add cost to our machines?
A chip like the TPD4S014 has ESD protection on the data lines that is rated up to +/- 1500 volts, clamping to ground to dissipate the energy. It’s a solution that should protect against repeated spikes on the data lines, as well as short circuits on the power lines and over/undervoltage situations.
The ADuM4160 is an interesting step up from this. It’s designed to provide isolation between a USB host and the device connected to it. Rather than relying on clamping, this chip implements isolation through air core transformers. Certainly this would be overkill to install in every product, but for those of use building and testing USB devices this would save you from “Oops, wrong USB cable” moments at the work bench.
Speaking of accidents at the bench, there is certainly a demand for USB isolation outside of what’s built into our computers. Earlier this year we saw a fantastic take on a properly-designed USB power strip. Among the goals were current limiting, undervoltage protection, and a proper power disconnect switch for each port. The very need to design your own reminds us that consumer manufacturers are often lazy in their USB design. “Use a USB hub” is bad advice for protection at the workbench since quality of design varies so wildly.
We would be interested in hearing from anyone who has insight on standards applying to equipment continuing to survive over current or over voltage events and remain functional. There are standards like UL-60950 that should apply to USB. But that standard includes language about failing safe for the operator, not necessarily remaining functional:
After abnormal operation or a single fault (see 1.4.14), the equipment shall remain safe for an OPERATOR in the meaning of this standard, but it is not required that the equipment should still be in full working order. It is permitted to use fusible links, THERMAL CUT-OUTS, overcurrent protection devices and the like to provide adequate protection.
So, we’re here to ask you, the readers of Hackaday. Are our USB devices robust enough? Do you have a go-to USB protection chip, part, or other circuit you like to use? Have you ever accidentally killed a USB host device (if so, how)? Do you have special equipment that you depend on when developing projects involving USB? Let us know what you think in the comments below.
















> “Use a USB hub” is bad advice for protection at the workbench since quality of design varies so wildly.
Yep, fried one computer acciddentally connecting 230AC to usb. It was through hub. Only ssd survived (that was lucky). Ram, motherboard, keyboard and mouse connected to that hub were toast. Several years back coworker did the same thing to his mac mini. Somehow mac survived, but monitor was toast (also avr-usb programmer literally exploded). We still have no idea how that mac survived but monitor was fried.
Noob question: How do you accidentally connect 230VAC to a usb port?
+1
+1
Could be something like this:
https://i.redd.it/mbkk3cu4u5mz.jpg
The worst case scenario there is on a phone…theoretically the outside of an all metal phone could become live and shock someone.
Doing the same on a computer would probable just cause a short to ground…no reason for it to get to the MOBO.
Funny US people with their funny outlets :-) /s
Comedy wiring.
I’ve had it happen once. An android tablet (cheap!) was connected to a “wall-wart” 5V power supply (cheap!) using a separate non-usb cable. Simultaneously, I’ve connected it via USB to my PC. Bang!
It turns out that a capacitor between the AC & DC sides inside the power supply has shorted out, at least for a split second before exploding. I think that 230V was supplied to the GND part on the tablet side, while it was shorted to 0V (earth connection) on the PC side.
The wall wart, tablet, USB hub, PC mainboard and PC power supply were fried.
[BigClive] has some answers…
https://youtu.be/3Hdn0MuCK_0
And that’s one of the less dodgy USB power devices he’s taken apart! From him I’ve learned terms like “Capacitive Dropper”
Apple’s pretty good at isolating USB ports for some reason.
I let the smoke out of an esp32. By accidentally shorting 5v (USB voltage) to ground.
Warning popped up about a device using too much power, and the port was disabled until I unplugged the board from it. Recent-ish macbook.
I think half of the times that I reboot my Thinkpad are because the USB ports need a hard power-down before they work again after a power rail short. :)
But this is entirely different from hitting them with a voltage that’s way out of spec. I haven’t done that yet, and don’t want to push my luck.
Yes. I have had some bad experience with cheap KVM’s. Monoprice’s to be exact
We had a customers KVM die so we switched it out. The next day we got a phone call asking why his phone wouldn’t charge again … He had unplugged the keyboard and plugged in his iphone. Which promptly killed that usb port. His phone also turned off when he did that. But thankfully powered back up later.
Not sure if it those ports were even up to usb spec.
Are you talking about USB hub or KVM which is used to swicth keyboard/mouse/video for multiple computers?
Fried my computer just two weeks ago by trying to start an FTDI connection with an unpowered board – it tried to draw a very large amount of current through the computer, frying both the display and the USB port.
Of course after sending it in for repairs only the screen was repaired; the USB port wasn’t even checked even though I reported exactly what happened. *eyeroll*
fried a macbook pro mb working on an arduino with an l298 and a 24v dc motor, bad manipulation, short circuit and everything died (h-bridge, arduino and laptop). only the motor survived…
Hopefuly my company insurance covered it up :)
Most made in China stuff isn’t up to par anyway. Faked FCC Compliance, Faked CE Compliance, Faked UL Compliance.
It’s taking “Plug-N-Pray” literally.
Well when they started making USB fans and coffee warmers I knew that they probably weren’t following specs to the letter.
“Most stuff” IS made in China. It’s not the manufacturer’s fault if the products aren’t designed for compliance.
i think the blame for fault is more appropriately determined by incident. Sometimes the products are not designed for compliance and china is one of the few places where you can find manufacturers who will build to that spec, other times products are designed for compliance but the manufacturers cut corners to turn a better profit.
It is irresponsible to paint all scenarios with the same brush when its the people who are dodgy regardless of where they live or what they do. The only reason that it is hard to find a manufacturer in europe and america who will build a product out of compliance is because of the litigious society that would try and find a way to sue the manufacturer.
It’s a good thing that non-Chinese always care about electrical device safety and not about profit:
https://en.wikipedia.org/wiki/All_American_Five#Potential_hazards_of_the_design
Not to mention multiple redundant flight safety systems on Boeing planes.
Personally, I would prefer the option to not provide internal (computer) power to USB devices. I think that the data lines should be opto-isolated between the computer and the device. But I recognize that opto-isolation has its own issues including increased cost, complexity and shorter life span than pure electric connections. However, in my view, usb type devices are generally transient and usually somewhat “ephemeral” devices to begin with. How many people are really expecting their mouse to usher in the next millennium anyway?
No matter how you protect somthing, there will always be a situation where somebody else is able to do some damage. Esd protection should be enough or should every port be protected against people poking in it with a ludicrous high voltage source DESIGNED to inflict damage.
i don’t know if you can opto-isolate modern usb data? i have the impression there is a funny differential low voltage encoding and in any case the clock is very fast…but i don’t know what opto-isolators are really capable of either, it just seems like the sort of thing that wouldn’t be straightforward. it’s not simple/slow like MIDI is.
fwiw most of the usb devices i actually use are more than ten years old, but the surprising part is that their mechanical parts haven’t failed yet! (scanner, cd-rom)
For simple, one-chip solution, USB 1.1 is the limit. USB 2.0 isolators are available, but as separate, quite expensive devices. They may protect the rest of computer, but USB killer would kill them without problem.
Raspberry Pi + USB/IP works pretty well for up to USB 2.0.
Ethernet shares the USB bandwidth, so at most you would get 1/2 before any additional overheads.
Still a cheap way of isolation. It is in Linux mainline unlike its Windows port that went dead since 2011. :(
Glass fiber optic gb/s is fast :-) and most pc have optic drive dvd mb/s, optoisolation is no problem. Also is isolation transformer in rj45 ethernet gb/s.
Hard to find reasonably priced optos that will do the speeds USB requires. Transformers better choice .
Power delivered by USB killer is much greater than anything that can happen to USB port during any imaginable situation. No ESD protection circuit will last it. ADuM optoisolator wouldn’t help either – it will be destroyed by killer and port will be unusable as well. It may only protect rest of the computer.
It makes no sense to design USB port that can withstand using such device. I don’t even think it’s possible to have such protection and maintain USB data rate (without using fiberoptics anyway). Then again, if someone want’s to damage it, it will use a hammer.
You don’t want the ADUM4160 as it is only “full speed” i.e. 12Mbps capable. Blame the USB-IF for their terrible naming scheme since it goes Low Speed -> Full Speed -> High Speed -> SuperSpeed -> SuperSpeed+. They’ve finally started qualifying it with the specific USB standard used but I expect they’ll come up with another stupid name for marketing reasons.
There are isolators that will cope with the maximum transfer rate but they’re extremely expensive.
In this world of marketing with words the use of the word medium can’t be used at all because of pisschology so the next word is high. 720p should have been called medium def is an example.
HD radio is not what they want you to think at all. Not even close.
They don’t even need another stupid name; the USB standards are a mess themselves. Original 5Gbps was renamed from USB 3.0 to USB 3.1 gen 1 to USB 3.2 gen 1, and 10Gbps was renamed from USB 3.1 gen 2 to USB 3.2 gen 2. We should all just ignore the USB-IF and specify the link speed.
I suspect that it’s niche enough not to attract the necessary attention; but it seems like exploiting SFP modules would probably be a handy way to do USB isolation at high speed and fairly low cost.
Thanks to substantial demand in switching and interconnect applications they are about as cheap as high speed optical hardware gets and available in a variety of flavors depending on the type of fiber you are using and the run length you need. Even 1Gb modules would be enough for USB 2; and 10Gb would cover 3(the 8Gb ones for fiber channel would also handle USB 3.1 but not 3.2).
Those pass no power, and consume some; so you’d need an active box at both ends; but it would take quite an ESD event to burn through even a couple meters of fiber, so the host computer would be nice and safe.
See NMUSB202MC for a really cool part :)
3 times the cost of the AD chip, and still wants you to add TVS diodes at the output. The AD part only wants 8 capacitors for filtering. I’ll stick with the AD solution.
On the other hand, this part comes with an isolated power supply for the device.
Worth a mention that if you’re just looking for isolation on a USB/Serial dongle, that’s a lot easier because you can do the isolation between the USB/Serial chip and the outside world. (The USB/serial chip isn’t isolated, just the serial outside world.)
We have a handful of projects doing just that on Hackaday.io, so you can just point and click to get one made.
This is worth doing for level-shifting reasons as well as simply talking to any device that doesn’t necessarily want to share your laptop’s ground.
A killer device could just as easily pump a huge pulse into the 5v rail as well – with plenty of joules….but that’s not the really big flaw in USB.
It’s that computers trust (have to at this point) that the device is what it says it is.
Thus leading to things like the Rubber Ducky and related items – which can report itself as USB storage – and is, but while you’re not looking, can reset itself to be a keyboard and type badware right into your machine – and do it so fast you might not even see the screen blink. There is NO FIX POSSIBLE for this flaw that’s backward compatible.
It’s as safe as DNS before dnssec (well, actually not even that good), or BGP – it’s based on an utter trust that is trivially broken.
Otherwise, it’s darned handy.
The quoted 1500V is only valid for a very limited capacitance, relatively large source impedance, at low interval and low average power. You can’t assume any pulse less than 1500V is survivable!
It’s impossible to defend against such attacks; the attacker could simply increase the energy and power delivered to the port to blow it up. Even if you assume the attacker can only use power from the USB port, with enough capacitors he could charge those in half an hour and dump 4.5kJ in a single discharge. Good luck dealing with that, if you need to minimize the capacitance on the data lines.
Granted, a 4.5kJ capacitor bank isn’t exactly inconspicuous, but a LiPo battery will do the same, and doesn’t need to charge on the spot.
Switching to optical fiber should do the trick, but that would be rather expensive for small and cheap USB devices. Also, the power pins, while somewhat easier to protect, could still be vulnerable.
Those USB suppressors can only deal with ESD. They can’t be scaled up as their parasitic capacitance will degrade/break USB traffics.
Your typical surge suppressor for AC outlet is round 10-400J range. A 10kJ device is more a hockey puck 60mm device. There is always the AC power cord to USB plug with a lot more sparks, fire that one can’t protect.
I work with a product that’s powered by a higher DC Voltage than 5 but far lower than 200, that then connects to a PC via USB. If there is a failure of the product’s internal voltage regulator then the full supply Voltage ends up on the data lines, quickly and permanently disabling the PC. I have seen the top blown off a North Bridge chip. We’ve started using USB hubs as sacrificial “fuses”; $10 is cheaper and easier to replace in a foreign country than a $700 PC with a proprietary software package loaded. Only twice has the PC taken the brunt in the last 12 years, but we have received cases of dead USB hubs.
At the time we were designing the interface such products as the ADUM4160 didn’t exist. I ended up with an electromechanical isolation solution that allows time to check for faults and shut down the supply that would kill the PC otherwise. It requires some software burden but has been largely successful in its mission (there are still a few failures due to the nature of this product but they only kill the hub, still in place). Anything else I tried with protection/isolation hosed the USB data transfers.
Sorry, can’t give any more details due to social media policy / trade secrets.
A crowbar circuit on the power rail could help to clamp the voltage and blow the fuse for protection.
https://en.wikipedia.org/wiki/Crowbar_(circuit)
Sounds like the regulator reliability is the issue and you are only covering the symptoms/reduce the damages.
Is there any wired port that is invulnerable to malicious overloads? I can’t think of one. Any connector that provides power, either intentionally or as a side effect, is subject to having that power stored over time and sent back as a quick high voltage spike.
Things that don’t deliver power are still subject to overloads, but the malicious device must provide its own energy source.
Ports ought to be protected against the kind of unintentional static zapping that can happen on a dry day when walking across a carpeted floor. And they should probably be protected from damage if any pins are shorted in any combination. But I don’t believe protection against all sorts of intentionally malicious attacks is reasonable.
There is a mix of problems listed above –
In summary –
1) the external device draws way more current – say is shorts – the power coming from the pc.
2) there is a possible application of a high – but ‘natural’ (say 240V) external power supply to either the power or data connections.
3) some malicious product does whatever it can to fry the pc.
The there are a number of different possible responses.
A) PC and everything connect survives with no damage, but may need rebooting.
B) something of low economic value – say usb hub or fuse – blows
C) everything is fried.
I think we would all agree that (1) should always result in (A) – but in the real world it doesn’t, as I’ve had fried hardware just from the usb power lines being shorted…
The next step would be that (2) results in (B) at most – this is still much better than everything fried as fuses etc are easy to replace… I think this is the big one we should aim for.
I think (3) is just going to be unstoppable unless there are specific needs OR if something like (2) can be done.
So what I think we need is a small ‘fuse’ device in the usb chain somewhere…
I’ve had that with one of my (slightly older) tables. I plugged some experimental hardware in (my own design!) that was also battery powered.. Large flash of light from inside the tablet and then it was completely dead… But when I pulled the tablet apart – as one does – there was an actual small fuse that had spectacularly died. Replaced that and the whole thing worked again.. :-)
I used to work cable TV back in the day, and we had a lot of problems with people in MDU’s(multi-dwelling units) stealing cable, almost always to the detriment of paying customers’ quality of service. We had a particularly bad one who was apparently an electrician whom knew nothing about low-voltage wiring for RF(it was a house converted to apartments, but you get the point).
In the basement was the distribution point, and he would regularly cut up wires, put in crappy splitters(sometimes incorrectly), have shorts on the connectors, etc. We disconnected him multiple times, cut the coax he installed, installed the kind robust lockable boxes that we put on poles for power supplies… we even tried yanking the coax to pull his TV off of whatever stand it was on. We were always back the next week for a trouble-call.
I finally told my boss, an old school-type, to contact legal, but he said to get in the truck and go for a ride. We went down there, located the offending line and he showed me a dirty trick… stripping the coax to obtain two conductors, and very gingerly with the linesman gloves, hooking it into the 220VAC outlet… he let it marinate for a few minutes, unhooked it, reset the breaker, and stabbed the coax through a piece of paper upon which was written, “No more.” We stuck around for a half hour or so, to make sure the place didn’t burn down(we were yards from a firehouse)… rolled an got some chow. He said they used to have a device called a “bullet” to do this, but that was no longer part of the kit.
Now, that 220 probably only blew out the RF section of the TV, but this was in a time where the TV repair shop had already ceased to exist. We stopped having problems there after that.
Great story, thanks! :)
Great study in human nature.
Good story and explains in part the move to all-digital. People sometimes are their own worst enemies.
Funny but very risky. 1. Someone could have been hurt, and 2. If that guy decided to sue it would be a slam dunk, with the note and all. Using a special device would at least be relatively safe, and would drastically reduce the the legal shit storm this could get you into.
I’m not sure why the thief would connect the note to his TV not working, AFTER they reconnected the line despite the note. The damage could be attributed to a run of the mill lightning surge.
It is no challenge to damage an electronic device through any of its physical connections.
Securing it against such threats would double its cost – at least.
It’s a race you can never win…
You probably can find some solution now to protect your device from a 200V DC event of limited energy. But as soon as you would bite the bullet (pay the cost) to have your devices protected against that event, someone comes up with the next best USB Killer device 2.x, that has more energy, higher voltage or both.
At some point, even the “protection device” will not save you (or your device) anymore. Just apply high enough power to the USB port to vaporize away the copper traces on the PCB or the connecting tabs inside the USB port itself will still give you a permanent damage on that port.
So, the best line of defense would be a defined point of failure that just completely and permanently disconnects the USB port that was “attacked”, in order to at least save the rest of the hardware. Might be some modular solution, so you can basically just replace that port and the protection device, but for most uses, the space required and the cost of extra connectors would already be a killer argument against that solution.
User servicable “fuses” on an impedance controlled differential pair would probably be possible, but not that easy to design and implement and again, customers would not want to pay the price for that.
You would have to ask yourself: “Why would all of the customers accept a massively higher cost of every USB device out there, if they never even had a single failure of an USB device where that protective circuit would have saved theyr device or computer…”
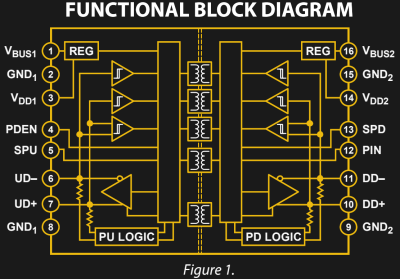
Aside from bidirectional nature, USB2 also uses DC common mode signal for sideband which makes it harder to isolate. This is the reason why they ended up with 5 transformer symbols in the block diagram instead of just 2.
In USB3, they introduced an additional RX and TX pairs of signals along with the old 4 pins of USB2. They could have used AC coupled signals like PCIe, SATA. The small capacitor offers a tiny bit of protection against shorts to low voltage power rails. Whatever after the caps still have to withstand the charging/discharging current.
Even then it won’t protect against high voltage attack to power rails nor the USB2 signals.
Even if you have the best protection for the USB, people can simply destroy a PC by inserting a screwdriver into the power supply and jiggling a bit. Or simply “accidentally” spilling some coffee into the P.S. fan opening :)
You’re making a very strong argument for thin clients. Keeping the expensive stuff away from the “children”.
Type “USB isolator” into eBay and you’ll find them for ~£7 including delivery and £17 for local stocks. They’re awesome and much more useful than just mitigating against mains connections. I use them for connecting to some Hi-Fi kit to eliminate the tiny amount of mains hum that was there. And for connecting to guitar kit that a sh1t load of mains hum. Fixed.
A handy plus is the built in isolated power supply so anything up to about 1 W draw can be fed without an additional adaptor. Won’t charge a phone though.
i have designed and produced a TI TUSB8041 based USB3 via fiber (SFP) extender for a highly specific job.
works great. only thing it fails doing is USB2, but we did not need that.
Has anyone tried isolating the data lines with an ethernet transformer?