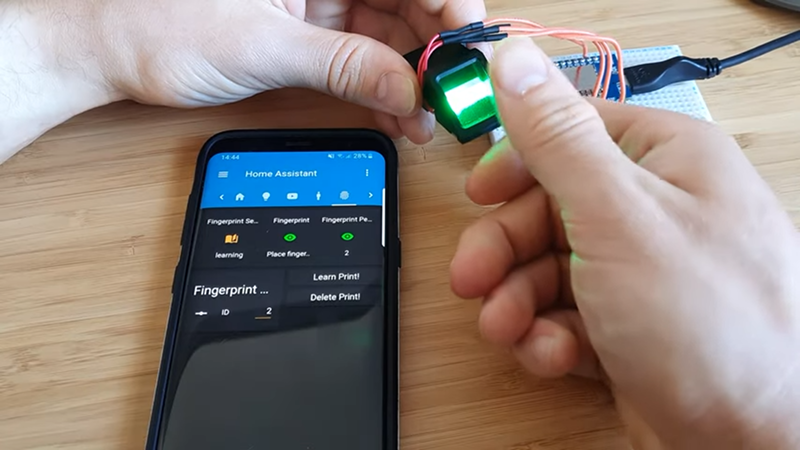
Biometrics — like using your fingerprint as a password — is certainly convenient and are pretty commonplace on phones and laptops these days. While their overall security could be a problem, they certainly fit the bill to keep casual intruders out of your system. [Lewis Barclay] had some sensors gathering dust and decided to interface them to his Home Assistant setup using an ESP chip and MQTT.
You can see the device working in the video below. The code is on GitHub, and the only thing we worried about was the overall security. Of course, the security of fingerprint scanners is debatable since you hear stories about people lifting fingerprints with tape and glue, but even beyond that, if you were on the network, it would seem like you could sniff and fake fingerprint messages via MQTT. Depending on your security goals, that might not be a big deal and, of course, that assumes someone could compromise your network to start with.
On the other hand, this would probably work fine for keeping little ones out of the workshop or the liquor cabinet or something like that. If the kid can hack the MQTT, she probably should be in the workshop, after all. Seems like for real security, you’d need to authenticate the fingerprint reader with some sort of key scheme at a minimum.
If you want to know more about how fingerprint scanners work, there’s plenty to read about. If tape and glue are too low tech for you, you can also print a fake finger. That’s why we don’t suggest them for security.















Biometrics should never be considered the ‘password’. Only use them for the ‘username’.
Hrmmm, I’ll admit that I’ve avoided bio-metrics on principle and their security issue flaws.
However, I have to say that I really like this idea. It’s simple and easy to implement. Thanks for the tip!
xx
Exactly
+1
it’s all about the threat model, in most cases the right biometric verification is a lot better than pincodes and passwords. The inherent advantages are of course that the user can’t forget his/her biometric features and it doesn’t need remembering :) Even if it’s technically feasible to clone the users biometrics features without cooperation other methods of authentication might carry more (risk) disadvantages.
In the usecases mentioned above, you might sneaky measure the persons weight wile doing the fingerprint authentication and use that as a second factor ;)
You can watch it the sound turned-off. there is no comment and it will save you from listening to cringey music.
I would prefer the eletrical noise of the microphone to these “YouTube” default soundtrack.
These fingerprint sensors are weird to me. They store all the data on the sensor itself and basically send pass/fail. I get that it saves arduino memory, etc but it’s still weird.
Realistically, this is going to be a net positive for a home security setup intended to keep out simple thieves and such. What are the odds that a random burglar will a) recognize that this scanner uses MQTT, b) know how to crack a network and spoof MQTT c) would rather do all that instead of moving on to an easier target or just bypassing the lock in the normal way (a swift kick).
Fingerprints can be much more convenient than a key. Convenient but marginal security that gets used is better than inconvenient security that gets left unused.
Giacomo said: “Fingerprints can be much more convenient than a key.”
Yeah, much more convenient at spreading diseases!
Hah yeah. But more than a door knob?
Biometrics aren’t the problem. It is the choice of where and how to implement them. If you don’t plan for the weaknesses in any security control you will experience failures.
To get my fingerprint all they have to do is cut off my finger.
To get my memorized password all they have to do is cut off my head. Oh wait – hmmm…
true story? Malaysia car thieves steal finger
http://news.bbc.co.uk/2/hi/asia-pacific/4396831.stm