Back when Windows NT was king, Microsoft was able to claim that it met the strict “Orange Book” C2 security certification. The catch? Don’t install networking and remove the floppy drives. Turns out most of the things you want to do with your computer are the very things that are a security risk. Even copy and paste.
[Michal Benkowki] has a good summary of his research which boils down to the following attack scenario:
- Visit a malicious site.
- Copy something to the clipboard which allows the site to put in a dangerous payload.
- Visit another site with a browser-based visual editor (e.g., Gmail or WordPress)
- Paste the clipboard into the editor.
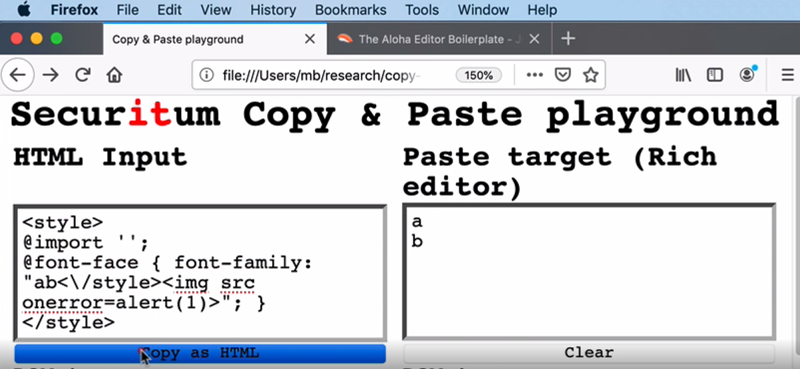
The issue is that the editors accept HTML data and this allows the clipboard to inject JavaScript. If you’ve never worked with the clipboard at the API level, it might surprise you to learn that the clipboard usually has more than one item in it at a time. For example, the clipboard could have some plain text, some HTML, and a special proprietary format all at one time. Presumably, though, all of those items represent the same information.
Browsers are aware of this problem and attempt to clean text they put on the clipboard. [Michal] put together the “Copy and Paste Playground” to allow exploration and demonstrate what the browsers will and won’t accept.
The rest of the post covers fixed bugs in several major browsers and editor systems, including GMail and Google Docs. There is also some discussion of a few systems that remain nameless since the bugs have not yet been fixed.
[Michal] was very thorough and unsurprisingly has claimed about $30,000 in bug bounties for his work. We have gotten used to seeing exploits on IoT devices, but it is a bit surprising that something as ordinary as the clipboard can pose a threat. If you want to claim some bug bounty yourself, maybe next year you can try hacking a satellite.















They better not try to take away cross-app copy and paste!
They will to pry it from your dead mouse?
*have*
Applications (whether local, remote or in a webpage) should not accept user-provided data as safe, it should absolutely be sanitised. This is one of the basic rules!
So the issue really is – how well sanitised is the pasted data in the application being pasted into?
Pasting HTML (with embedded JS) as rich-content (i.e., not as the plain-text source) should obviously raise an issue. A web-application is likely to be a CMS or Wiki – it really should strip the pasted content to a barebone (high level structure and core formatting) representation, and reconstruct it from that in a safe manner, to work well in the target platform’s needs.
Yes, that means work for the developer, likely additional work for the person pasting, but that’s a cost of security.
“Yes, that means work for the developer, likely additional work for the person pasting, but that’s a cost of security.”
Handed over to a third-party library.
+1
I think that is exactly the way to go. Software should structure data in a way that does not pose a (potential) threat to be used in clipboards (and similar facilities, message passing, etc.) and anything that manages the copy&paste (or other such interfaces) should sanitize data in both directions. And yes, that does mean data should be sanitized by both whatever produces it and also all that consume it before it is used.
I always find it very odd when formatting is copied between applications, the only time I can remember wanting to be able to copy formatting was when I wanted to spoof the displayed originator of a quoted piece of text in Skype, and really that’s exactly the type of exploit that’s being discussed in this article.
Seconding that. I usually copy some bit of text from somewhere into an email, find it has a weird font size and style, undo, then paste as plain text. ctrl+v, “bleugh”, ctrl+z, ctrl+shift+v. I’d rather paste as plain text was the default.
I usually copy and paste in a plain text editor first to remove all the formatting. I must admit, I like using Apple’s handoff feature (shared clipboard between Apple devices). I’ve honestly just avoided thinking about the potential risks of doing that. Big yikes!
It should be fairly easy to make an AutoHotKey script (or whatever keyboard macro software you prefer) to automatically plaintext anything you copy.
I had few cases where i needed to keep formatting mostly excel – word in both ways, and sometimes excel, word or web page to powerpoint. But its rare and 99% i prefer plain text to format it later so shortcut ctrl+v and ctrl+shift+v shoud be swapped.
Salesman: “This computer is 100% secure you could no more penetrate it or exfiltrate data from it than you could that large rock decorating our parking lot.”
Customer: *Flips switch to on.* “How about now?”
Salesman: “Errrr….”
Intel Management Engine
There have been copy/paste attacks where a webpage with a helpful looking Linux command actually puts a malicious command in the paste buffer. The best approach is to always paste into a text editor first.
That’s why when the install progedure of some program says “just use curl … | sudo bash” I ditch it w/ no remorse.
oh, that obscenity. It’s Even More Better when they say “curl -k”
All rich editors I’m familiar convert the pasted HTML into their markup. While they are at it, they also grab images and add them to attachments.
Microsoft Notepad is extremely limited and cannot run anything malicious that gets slipped into the copied clipboard. Paste the block there and if there’s extra text, the website or one of the ad on the website was likely malicious.
I use Notepad all the time to clean up formatting and just leave the text.
Not so long ago browsers didn’t allow access to clipboard and every website worked around this by using flash.
Today browsers allow access to clipboard? Whoever though that was a good idea to do so the way it was done?
Allowing it at all to read or write clipboard without explicit user confirmation is a bit nuts. Having it as the default is a bit mind boggling, mostly becuse it’s a huge security hole with so little potential benefit.
And of course browsers facilitate this by allowing websites to fuck with the copy function, inserting whatever text they want.
What’s very annoying are sites that append their URL or some other promotional BS onto the ends of anything copied.
Much more common but still annoying are when a space gets added to the end of the selection. Did the source do that or was it the destination app or program that stuck in the space? We have no way of knowing and it’s a PITA when one needs to copy and paste an *exact* string of text. “Error? What error! I copied and pasted, it’s *correct*!” *looks closer* #$^#$^@^ added a space to the end.
Then there is how MS Word and some others “help” by automatically selecting whole words when you want to start or end a selection in the middle of a word, or to not select a punctuation mark.